Exchange Online Protection (EOP) interview questions and answers
Are you preparing for an interview focused on Exchange Online Protection (EOP)? Look no further! In this comprehensive guide, we’ve gathered a curated list of essential Exchange Online Protection interview questions and answers.
From email security to spam filtering and more, we’ll dive deep into these topics and provide expert answers to help you shine in your interview. Whether you’re a seasoned IT professional or an aspiring candidate eager to impress, this article is your key to interview success. Get ready to master the realm of Exchange Online Protection interview questions!”
📌We have categorized Exchange Online Protection interview questions and answers in different levels as below:
Freshers
Experienced
Advanced Level
Top 10 frequently asked Exchange Online Protection (EOP) interview questions
- What is Exchange Online Protection (EOP)?
- How Exchange Online Protection works?
- How does Exchange Online Protection handle email security?
- What are the different types of threats that Exchange Online Protection protects against?
- Can you explain the anti-spam features and capabilities of Exchange Online Protection?
- How does Exchange Online Protection handle malware and phishing attacks?
- What are the advantages of using Exchange Online Protection over traditional on-premises email security solutions?
- Can you explain the integration process of Exchange Online Protection with Office 365?
- How can we disable Exchange Online Protection (EOP)?
- What is the difference between Advanced Threat Protection (ATP) and Exchange Online Protection (EOP)?
Learn Exchange Online Protection (EOP). Refer to EOP deep-dive video on our YouTube channel.Exchange online protection interview questions for freshers
1. What is Exchange Online Protection (EOP)?
Exchange Online Protection (EOP) is a cloud-based email filtering service provided by Microsoft. It is designed to protect organizations against various email-based threats, such as spam, malware, phishing attempts, and other types of malicious content.
EOP operates as a part of Microsoft’s larger suite of productivity and collaboration tools called Microsoft 365 (formerly Office 365). It integrates seamlessly with Exchange Online, which is the cloud-based email and calendar service in Microsoft 365. EOP works by scanning incoming and outgoing email messages, analyzing their content, and applying a set of security filters and policies to identify and block potential threats.
2. How Exchange Online Protection works?
Exchange Online Protection (EOP) works by employing various layers of security measures to analyze and filter incoming and outgoing email messages.
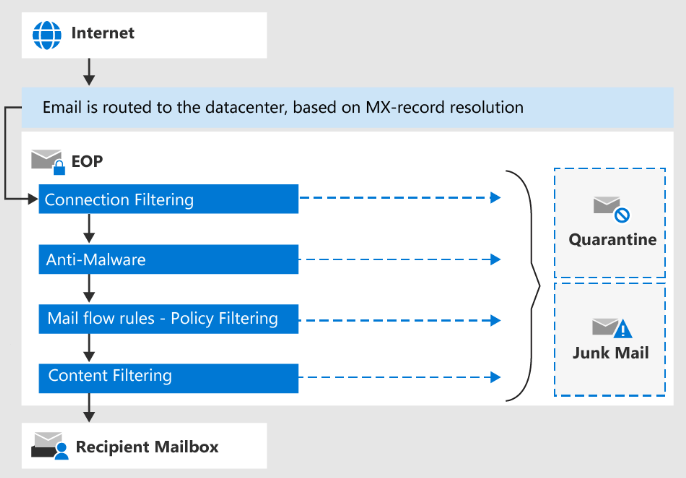
Here is an overview of how Exchange Online Protection (EOP) operates:
When an email is sent to your Exchange Online organization, it is delivered to Exchange Online Protection (EOP) basis on the MX record for your domain.
Learn how MX (mail Exchange) DNS record works in Exchange Online Protection.As soon as email is delivered to EOP, it goes through multiple checks within Exchange Online Protection as discussed below:
Connection Filtering: EOP starts by examining the connection properties of incoming messages. It checks the sender’s IP address against various reputation-based lists and blacklists to identify known malicious sources. If the sender’s IP address is flagged as suspicious, the connection is blocked, and the email is not delivered. This helps prevent emails from known spam sources from reaching the recipient’s inbox.
Malware Filtering: Exchange Online Protection (EOP) scans email attachments and embedded URLs in real-time to detect and block known malware signatures. It leverages multiple antivirus engines and threat intelligence to identify malicious files and URLs. If a message contains an infected attachment or a link to a compromised website, EOP will quarantine that email and only administrators can release them.
Transport Rules: Transport rules in Exchange Online Protection (EOP) are a set of policies that can be configured to control and manage the flow of email messages within an organization. These rules define specific conditions and actions that are applied to incoming or outgoing emails as they pass through the EOP service. Transport rules help organizations enforce email policies, apply compliance requirements, and automate actions based on specific criteria.
Data Loss Prevention (DLP): EOP includes Data Loss Prevention capabilities that allow organizations to define policies to prevent sensitive information from being shared via email. It can scan outbound emails for specific patterns or keywords that indicate sensitive data and take appropriate action, such as blocking or encrypting the message.
Content Filtering / Spam Filtering: Content filtering in Exchange Online Protection (EOP) is a feature that allows organizations to define rules and policies to analyze the content of email messages and apply actions based on specific criteria. It helps protect against spam, malware, phishing, and other types of unwanted or harmful content by examining the message content, attachments, and URLs.
Advanced Threat Protection (ATP): Advanced Threat Protection (ATP) refers to an additional security feature provided by Microsoft to enhance the protection against advanced email-based threats. ATP in Exchange Online Protection offers several security capabilities to safeguard email communications.
- Safe Attachments: ATP scans email attachments in real-time using advanced machine learning and behavioral analysis techniques. It detects and blocks malicious attachments before they reach the recipient’s mailbox, reducing the risk of malware infections.
- Safe Links: ATP inspects links embedded in emails and performs real-time analysis to identify and block malicious URLs. It provides protection against phishing attacks, malicious websites, and other forms of harmful links. If a user clicks on a potentially dangerous link, they may be warned or redirected to a safe page.
Once email passes all the above checks, it is finally delivered to the recipient’s mailbox.
3. How does Exchange Online Protection handle email security?
Exchange Online Protection (EOP) handles email security through a combination of advanced technologies and techniques designed to detect and mitigate email-based threats. Here’s how EOP handles email security:
- Connection Filtering: Exchange Online Protection (EOP) starts by filtering incoming email connections. It checks the reputation of the sending IP address and domain to identify known sources of spam, malware, or other malicious activity. Suspicious or malicious connections are blocked at this stage, preventing further email processing.
- Anti-Malware Protection: EOP employs multiple layers of anti-malware protection to detect and block email-borne viruses, worms, and other types of malware. It uses real-time scanning and signature-based detection methods, as well as heuristic analysis and machine learning algorithms to identify and block malicious attachments or links within emails.
- Spam Filtering: EOP’s anti-spam filters use various techniques, such as content analysis, sender reputation checks, and machine learning algorithms, to identify and block spam emails. These filters assess the content, structure, and metadata of incoming emails to determine their spam likelihood. Emails identified as spam are either quarantined or sent directly to the users’ junk email folder.
- Phishing Protection: EOP employs advanced heuristics and machine learning algorithms to detect and block phishing emails. It analyzes email content, URLs, and sender behavior to identify characteristics commonly associated with phishing attempts. EOP can recognize and block suspicious emails that impersonate legitimate organizations, preventing users from falling victim to phishing attacks.
- Data Loss Prevention (DLP): Exchange Online Protection (EOP) offers built-in Data Loss Prevention capabilities to prevent the unauthorized sharing of sensitive information through email. Administrators can create DLP policies that scan the content of outgoing emails for specific patterns, keywords, or confidential data. If a policy violation is detected, EOP can block, quarantine, or encrypt the email to prevent data leakage.
- Encryption and Transport Layer Security (TLS): Exchange Online Protection (EOP) supports email encryption and Transport Layer Security (TLS) to protect the confidentiality and integrity of email communications. It can enforce TLS encryption when communicating with other email servers that support it. Additionally, EOP can encrypt outbound emails to ensure secure transmission and prevent unauthorized interception or access.
By combining these features and techniques, Exchange Online Protection helps organizations effectively mitigate email-based threats, secure sensitive data, and maintain a high level of email security.
4. What are the different types of threats that Exchange Online Protection protects against?
Exchange Online Protection (EOP) is a cloud-based email filtering service provided by Microsoft for organizations using Exchange Online or Exchange Server. It helps protect against various types of threats targeting email communications. Here are some of the common threats that Exchange Online Protection safeguards against:
- Spam: EOP identifies and filters out unsolicited bulk emails or spam messages, which can clog up email inboxes and waste resources.
- Phishing: EOP analyzes incoming emails to detect phishing attempts, where malicious actors impersonate trusted entities to deceive recipients into revealing sensitive information like passwords, credit card details, or login credentials.
- Malware: EOP scans email attachments and links for known malware signatures or suspicious behavior. It blocks emails containing malicious attachments such as viruses, ransomware, trojans, or other types of malware.
- Spoofing: EOP helps prevent domain spoofing by verifying the authenticity of the sender’s email address using various techniques like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
- Zero-day attacks: EOP employs advanced threat intelligence and machine learning algorithms to identify new and emerging threats that have not been previously detected. It helps protect against zero-day attacks by analyzing patterns and behaviors to identify potentially malicious emails.
- Data loss prevention (DLP): EOP offers features to prevent accidental or intentional data leakage through email. It can detect and block emails containing sensitive information such as credit card numbers, social security numbers, or confidential company data.
These are some of the primary threats that Exchange Online Protection protects against. It aims to provide a comprehensive and layered defense to ensure the security and integrity of email communications for organizations.
5. Can you explain the anti-spam features and capabilities of Exchange Online Protection?
Exchange Online Protection (EOP) provides several anti-spam features and capabilities to help organizations combat unsolicited and unwanted email messages. Here are some of the key components and functionalities of EOP’s anti-spam features:
- Content filtering: Exchange Online Protection (EOP) applies content filtering techniques to analyze the content and structure of incoming emails. It checks for specific patterns, keywords, or characteristics commonly associated with spam messages. Based on the configured policies, EOP assigns a spam confidence level (SCL) to each email, allowing administrators to define actions based on the SCL score.
- IP block lists and allow lists: EOP maintains a set of IP block lists and allow lists. IP block lists contain known sources of spam, such as IP addresses associated with spamming activities. EOP checks the incoming emails against these block lists and can block or flag emails originating from listed IP addresses. Conversely, allow lists can be used to ensure that emails from trusted senders or specific IP addresses are not marked as spam.
- Real-time block lists (RBLs): EOP utilizes real-time block lists, such as the Spamhaus project, to identify and block emails from IP addresses known for sending spam. These RBLs are regularly updated to include new sources of spam, ensuring timely protection against known spamming sources.
- Sender reputation analysis: Exchange Online Protection (EOP) assesses the reputation of email senders to determine the likelihood of their emails being spam. It considers factors like past email sending behavior, feedback from recipients, and adherence to industry best practices. If a sender’s reputation is poor, EOP may increase the spam confidence level or block their emails altogether.
- Connection filtering: EOP employs connection filtering to analyze the characteristics of the connection made by the sending server. It checks for anomalies, such as a high number of connections from a single IP address or unusual connection patterns. These filters help detect and block spammers who try to distribute spam from multiple sources or use botnets.
- Bulk mail detection: EOP includes mechanisms to identify bulk email messages. It analyzes factors like message content, sending patterns, and recipient behavior to differentiate between legitimate bulk email (e.g., newsletters) and unsolicited spam. Administrators can define policies based on the classification of bulk mail to handle them accordingly.
- Advanced machine learning: Exchange Online Protection (EOP) leverages machine learning algorithms to continuously improve its anti-spam capabilities. By analyzing vast amounts of email data, it learns to recognize patterns and characteristics of spam messages, adapting to new spamming techniques and evolving threats.
These features work in tandem to provide robust protection against spam emails. EOP’s anti-spam capabilities are customizable, allowing administrators to configure policies, adjust filtering levels, and define actions based on the SCL score to suit their organization’s needs and reduce the impact of unwanted messages on user mailboxes.
6. How does Exchange Online Protection handle malware and phishing attacks?
Exchange Online Protection (EOP) is a cloud-based email filtering service provided by Microsoft for organizations using Microsoft Exchange Online or Office 365. EOP incorporates various mechanisms to handle malware and phishing attacks effectively. Here’s an overview of how EOP tackles these threats:
1. Malware Protection: Exchange Online Protection (EOP) employs multiple layers of malware protection to detect and block malicious attachments and links in emails. It uses the following techniques:
a. Signature-based Scanning: EOP maintains a vast database of known malware signatures. It scans email attachments and compares them against these signatures to identify and block known malware.
b. Heuristic Analysis: Exchange Online Protection (EOP) uses advanced algorithms to analyze the behavior and characteristics of email attachments and identify potentially malicious patterns. This helps in detecting new or previously unknown malware.
c. Real-time Threat Intelligence: Microsoft has a vast network of threat intelligence sources, including the Microsoft Intelligent Security Graph, which constantly monitors global email traffic. EOP leverages this intelligence to identify emerging threats and take proactive measures.
2. Safe Attachments: EOP’s Safe Attachments feature provides an additional layer of protection by opening potentially malicious attachments in a sandbox environment for analysis. If an attachment is found to be malicious, it is blocked, and the recipient is notified.
3. Safe Links: EOP’s Safe Links feature protects users from clicking on malicious URLs by rewriting the links within emails. When a user clicks on a link, it is first redirected to a Microsoft security service, where it is checked against a continuously updated list of known malicious URLs. If a link is determined to be malicious, the user is warned or blocked from accessing the site.
4. Anti-Phishing Protection: Exchange Online Protection (EOP) employs various techniques to identify and block phishing attacks, which attempt to trick users into providing sensitive information or visiting fraudulent websites. These techniques include:
a. Email Authentication: EOP verifies the authenticity of incoming emails using standards like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance). These protocols help detect and block spoofed emails.
b. Machine Learning: EOP utilizes machine learning algorithms to analyze email content, sender reputation, and other factors to identify phishing emails accurately. It learns from patterns and user feedback to improve its detection capabilities continuously.
c. User Education: Exchange Online Protection (EOP) includes customizable warning messages that alert users when they receive emails with suspicious content or potential phishing attempts. This helps educate users about the risks and encourages them to be cautious.
Overall, Exchange Online Protection combines multiple layers of security measures, including signature-based scanning, heuristic analysis, sandboxing, URL rewriting, and machine learning, to provide robust protection against malware and phishing attacks in email communication.
7. What are the advantages of using Exchange Online Protection over traditional on-premises email security solutions?
Using Exchange Online Protection (EOP) as a cloud-based email security solution offers several advantages over traditional on-premises email security solutions. Here are some of the key benefits:
- Scalability: EOP is a cloud-based service provided by Microsoft, which means it can effortlessly scale to accommodate the needs of organizations of any size. Whether you have a small business or a large enterprise, EOP can handle the volume of email traffic and adapt to your requirements without the need for additional hardware or infrastructure.
- Cost-effectiveness: Exchange Online Protection (EOP) eliminates the need for on-premises hardware, software, and maintenance costs associated with traditional email security solutions. As a cloud-based service, EOP operates on a subscription model, allowing organizations to pay for what they use. This can result in significant cost savings, especially for smaller businesses that may not have the resources to invest in and maintain their own email security infrastructure.
- Reliability and Availability: With EOP, Microsoft manages the infrastructure and ensures high availability and reliability of the service. Microsoft operates data centers across the globe, employing robust security measures, redundancy, and disaster recovery capabilities. This means you can rely on EOP to provide consistent and uninterrupted email protection.
- Advanced Threat Detection: EOP leverages Microsoft’s extensive threat intelligence network, which constantly monitors global email traffic and gathers insights from millions of users. This allows EOP to stay updated with the latest threats and provide effective protection against emerging malware and phishing attacks. Additionally, EOP incorporates advanced technologies like machine learning and behavior analysis to detect and mitigate sophisticated threats.
- Integration with Microsoft Ecosystem: If your organization already uses Microsoft Exchange Online or Office 365, EOP seamlessly integrates with these platforms. This integration ensures smooth email flow and maximizes the effectiveness of security measures. EOP also integrates with other Microsoft security solutions like Microsoft Defender for Endpoint, Azure Active Directory, and Microsoft Cloud App Security, providing a comprehensive security ecosystem.
- Easy Deployment and Management: Setting up and configuring EOP is straightforward, as it is a cloud-based service. It requires minimal on-premises infrastructure and can be managed through a centralized web-based console. This makes it easier for IT administrators to monitor and manage email security settings, apply policies, and track threats across the organization.
- Continuous Updates and Enhancements: Microsoft continuously updates and enhances EOP to address new security challenges and stay ahead of emerging threats. These updates are automatically applied to the service, ensuring that your organization benefits from the latest security features without any manual intervention or additional costs.
Overall, Exchange Online Protection offers the advantages of scalability, cost-effectiveness, reliability, advanced threat detection, seamless integration, easy deployment and management, and continuous updates. These benefits make it an attractive choice for organizations looking to enhance their email security while reducing the complexity and cost of on-premises solutions.
8. Can you explain the integration process of Exchange Online Protection with Office 365?
Exchange Online Protection (EOP) integrates seamlessly with Office 365, as both services are part of the Microsoft cloud ecosystem. Here’s an overview of the integration process:
- Activate Exchange Online Protection: To begin the integration, you need to activate Exchange Online Protection for your Office 365 tenant. This involves subscribing to the appropriate Office 365 plan that includes EOP or adding EOP as an add-on service to your existing Office 365 subscription.
- Verify Domain Ownership: Before you can start using EOP with Office 365, you need to verify your domain ownership. This ensures that you have administrative control over the domain you want to protect with EOP. The verification process typically involves adding a DNS record or creating a text file on your domain’s DNS settings. Microsoft provides detailed instructions for domain verification.
- Set up MX Records: Once your domain ownership is verified, you need to configure your domain’s Mail Exchanger (MX) records to route incoming email traffic through EOP. MX records specify the email server responsible for accepting incoming email for a domain. You will need to update the MX records for your domain to point to the EOP endpoints provided by Microsoft.
- Configure EOP Policies and Settings: After the MX records are updated, you can access the Exchange Admin Center (EAC) or the Microsoft 365 Security & Compliance Center to configure EOP policies and settings. This includes defining spam filtering rules, malware protection settings, and configuring anti-phishing measures such as Safe Attachments and Safe Links.
- Customize Filtering and Protection: Exchange Online Protection (EOP) allows you to customize the email filtering and protection settings based on your organization’s needs. You can specify the level of aggressiveness for spam filtering, adjust the sensitivity of malware detection, and define policies for handling suspected phishing emails. EOP provides a wide range of configuration options to match your security requirements.
- Monitor and Manage EOP: Once EOP is integrated with Office 365, you can monitor and manage the email security settings through the EAC or the Microsoft 365 Security & Compliance Center. These management consoles provide a user-friendly interface for tracking email flow, reviewing quarantined messages, adjusting policies, and monitoring threat protection statistics.
9. How can we disable Exchange Online Protection (EOP)?
Exchange Online Protection (EOP) cannot be entirely disabled, as it is a fundamental part of Microsoft’s email security infrastructure for Office 365. However, you can bypass filtering for specific scenarios or domains. Here’s how you can bypass filtering in EOP:
- Access the Exchange Admin Center (EAC) or Microsoft 365 admin portal: Sign in to your admin account and navigate to the EAC or Microsoft 365 admin portal.
- Go to the Exchange Online Protection settings: In the EAC or admin portal, locate the Exchange Online Protection settings section.
- Manage connection filtering bypass: Connection filtering helps block spam and malicious emails based on IP addresses. To bypass connection filtering for specific IP addresses or IP ranges, you can add them to the Connection Filtering IP Allow List. This ensures that emails from these sources are not subjected to connection filtering.
- Manage transport rules bypass: Transport rules in EOP allow you to apply custom actions based on specific conditions. To bypass filtering for certain emails based on specific transport rules, you can create exceptions or modify the rules to exclude certain criteria or domains from being processed by the rule.
- Manage safe sender and safe recipient bypass: Exchange Online Protection (EOP) allows you to create lists of trusted senders (Safe Senders) and trusted recipients (Safe Recipients). Emails from these senders or to these recipients are typically exempt from certain filtering checks. You can add specific email addresses or domains to the Safe Senders and Safe Recipients lists to bypass filtering for those addresses or domains.
It’s important to exercise caution when bypassing filtering in EOP, as disabling or bypassing security measures can expose your organization to increased risks. Bypassing filtering should only be done after careful consideration and when there is a valid reason or specific requirement to allow certain emails or domains to bypass the filtering process.
10. What is the difference between Advanced Threat Protection (ATP) and Exchange Online Protection (EOP)?
Advanced Threat Protection (ATP) and Exchange Online Protection (EOP) are two different services provided by Microsoft to enhance the security of email communication. While both services contribute to email security, they serve distinct purposes and offer different features. Here’s a breakdown of the key differences between ATP and EOP:
Exchange Online Protection (EOP):
- Email Filtering: Exchange Online Protection (EOP) is primarily an email filtering service that provides protection against spam, malware, and known phishing attacks. It uses various techniques, including signature-based scanning, heuristic analysis, and real-time threat intelligence, to detect and block malicious emails before they reach the recipient’s inbox.
- Default Email Security: EOP is included as the default email security service in Microsoft 365 and Exchange Online subscriptions. It provides baseline protection for inbound and outbound emails.
- Anti-Spam and Anti-Malware: Exchange Online Protection (EOP) offers robust anti-spam and anti-malware features to filter out unwanted and potentially harmful emails. It helps reduce the risk of users falling victim to phishing attacks or downloading malicious attachments.
- Basic URL Protection: EOP includes basic URL protection capabilities, such as rewriting URLs to redirect through Microsoft’s security service and scanning for known malicious URLs.
Advanced Threat Protection (ATP):
- Advanced Threat Detection: ATP goes beyond the capabilities of EOP by providing advanced threat detection and response features. It offers additional layers of protection against sophisticated and evolving threats.
- Safe Attachments: ATP includes the Safe Attachments feature, which opens email attachments in a virtual sandbox environment to analyze their behavior and detect potential malware. If a malicious attachment is identified, it is blocked before it reaches the recipient’s mailbox.
- Safe Links: ATP introduces the Safe Links feature, which helps protect users from clicking on malicious URLs within emails. URLs are rewritten and checked in real-time to determine if they lead to known malicious sites. If a malicious URL is detected, users are warned or blocked from accessing the site.
- Reporting and Tracking: ATP provides advanced reporting and tracking capabilities, allowing administrators to gain insights into email threats and monitor the effectiveness of security measures. It offers detailed reports and analytics on detected threats, including information on user clicks, attachments, and URLs.
In summary, EOP focuses on baseline email filtering, anti-spam, and anti-malware protection, while ATP provides advanced threat detection and response capabilities with features like Safe Attachments, Safe Links, and enhanced reporting. ATP is an add-on service to EOP and provides an additional layer of security for organizations that require more advanced protection against sophisticated email threats.
11. What is Exchange Online Protection license?
Exchange Online Protection (EOP) is not a separate license on its own. Instead, EOP is included as a built-in component of several Microsoft subscription plans, primarily those that include Exchange Online or Office 365 services. When you subscribe to a plan that includes Exchange Online or Office 365, EOP is automatically provided as part of the package.
EOP’s email filtering and security features are integrated into the Exchange Online service, providing protection against spam, malware, and known phishing attacks for your organization’s email communication. EOP is typically included in the following subscription plans:
- Microsoft 365 Business Basic: This plan includes Exchange Online for email services and EOP for email filtering and protection.
- Microsoft 365 Business Standard: Along with Exchange Online, this plan includes EOP for enhanced email filtering and security.
- Office 365 Enterprise E1: EOP is included as part of this plan, offering email filtering and protection features.
- Office 365 Enterprise E3: This plan includes both Exchange Online and EOP for comprehensive email services and security.
- Office 365 Enterprise E5: EOP is also included in this plan, which provides the most advanced features and capabilities for Exchange Online and email security.
12. Is Exchange Online Protection enough to protect your emails from external threats?
Exchange Online Protection (EOP) provides a solid foundation for protecting emails from external threats, but it is not a standalone solution. While EOP offers robust email filtering, anti-spam, anti-malware, and basic anti-phishing features, there are additional security measures you should consider to enhance email protection. Here are a few factors to keep in mind:
- Advanced Threat Protection (ATP): Consider adding ATP as an add-on service to EOP. ATP provides advanced threat detection and response capabilities, including features like Safe Attachments and Safe Links, which offer enhanced protection against sophisticated threats.
- User Awareness and Training: Educating your users about email security best practices, such as avoiding suspicious links and attachments, can significantly reduce the risk of falling victim to phishing attacks. Training programs and regular awareness campaigns can help strengthen the human factor in email security.
- Multi-Factor Authentication (MFA): Enabling MFA for email accounts adds an extra layer of protection by requiring additional verification beyond just a password. This helps prevent unauthorized access even if login credentials are compromised.
- Email Encryption: Depending on your organization’s needs, you may want to consider implementing email encryption solutions to protect sensitive information and ensure secure communication.
- Data Loss Prevention (DLP): Implementing DLP policies can help prevent the accidental or intentional leakage of sensitive data through emails. DLP policies allow you to define rules and actions to identify and protect sensitive information.
- Email Backup and Recovery: While EOP provides some level of email protection, having a reliable backup and recovery solution ensures that your emails are backed up and can be restored in the event of data loss or system failures.
- Security Monitoring and Incident Response: Implementing robust security monitoring and incident response processes allows you to detect and respond to potential threats or breaches effectively. This includes monitoring email traffic, analyzing logs, and promptly addressing any security incidents.
By combining Exchange Online Protection with additional security measures like ATP, user training, MFA, encryption, DLP, backup solutions, and incident response processes, you can create a comprehensive email security strategy that significantly enhances protection against external threats.
13. What is the role of Exchange Online Protection (EOP) in data loss prevention (DLP)?
Exchange Online Protection (EOP) is a cloud-based email filtering service provided by Microsoft that helps protect organizations against spam, malware, and other email-based threats. While EOP primarily focuses on email security, it does have some features related to data loss prevention (DLP).
DLP is a set of strategies and technologies designed to prevent sensitive information from being leaked or lost. It helps organizations safeguard their data by identifying and monitoring sensitive information and applying appropriate security policies to prevent unauthorized disclosure.
Within the context of EOP, its role in data loss prevention primarily involves the following:
- Content Filtering: EOP includes content filtering capabilities that allow organizations to define policies to detect and prevent the transmission of sensitive data via email. These policies can be configured to identify specific types of sensitive information, such as social security numbers, credit card numbers, or confidential documents. When an email matches the defined criteria, EOP can take actions like blocking, quarantining, or encrypting the message to prevent data loss.
- Transport Rules: EOP enables the creation of transport rules that allow administrators to define conditions and actions for inbound and outbound email messages. These rules can be used to enforce DLP policies, such as preventing the transmission of sensitive information outside the organization, adding disclaimers to messages, or encrypting specific types of communications.
- Policy Tips: EOP provides policy tips, which are informative messages that appear to users in real-time as they compose emails. Policy tips can inform users about potential policy violations, such as sending an email with sensitive information to an external recipient. This feature helps raise awareness among users and encourages them to follow established data protection guidelines.
- Reporting and Auditing: EOP offers reporting and auditing capabilities that allow organizations to monitor and analyze email traffic, including DLP-related events. These reports provide insights into email activities, policy violations, and potential data loss incidents, enabling organizations to refine their DLP policies and respond to any identified risks.
Exchange online protection interview questions for experienced
14. How does Exchange Online Protection handle email encryption and secure communication?
Exchange Online Protection (EOP) includes several features that contribute to email encryption and secure communication within organizations. Here are the key components and mechanisms provided by EOP:
- Transport Layer Security (TLS): EOP supports TLS encryption for secure communication between email servers. When both the sender and recipient organizations have TLS enabled, emails are transmitted over an encrypted connection, protecting the message content from interception and tampering while in transit.
- Opportunistic TLS: EOP uses opportunistic TLS, which means it attempts to establish a secure TLS connection whenever possible. If the receiving email server supports TLS, EOP automatically initiates a secure connection to ensure the confidentiality and integrity of the email transmission.
- Message Encryption: EOP provides the capability to encrypt individual email messages. This feature, called Office 365 Message Encryption (OME), allows users to send encrypted emails to both internal and external recipients. The encryption is achieved by applying strong encryption algorithms to the email content, and the recipient is provided with a secure method to access and read the encrypted message.
- Rights Management Service (RMS) Integration: EOP integrates with Azure Rights Management Service (RMS), which enables organizations to apply Information Rights Management (IRM) protection to sensitive emails. IRM protection allows organizations to define access rights and restrictions for email messages, including preventing recipients from forwarding, printing, or copying the email content.
- Secure Email Gateways: EOP acts as a secure email gateway, scanning incoming and outgoing messages for spam, malware, and other email-based threats. By blocking malicious emails and attachments, EOP helps protect users from potential security risks.
- Anti-Phishing and Anti-Spoofing: EOP includes anti-phishing and anti-spoofing mechanisms to detect and prevent fraudulent emails. It employs various techniques, such as sender authentication (e.g., SPF, DKIM, DMARC), reputation analysis, and machine learning algorithms to identify and block phishing attempts and spoofed emails.
- Data Loss Prevention (DLP): While not directly related to encryption, EOP’s DLP features play a role in securing communication by detecting and preventing the transmission of sensitive information. By applying DLP policies, organizations can enforce encryption requirements for emails containing sensitive data, ensuring that such information is protected during transit.
15. How does Exchange Online Protection handle email hygiene and filtering?
Exchange Online Protection (EOP) offers robust email hygiene and filtering capabilities to help organizations protect against spam, malware, and other email-based threats. Here’s how EOP handles email hygiene and filtering:
- Spam Filtering: EOP utilizes various techniques to identify and block spam emails. It employs machine learning algorithms, reputation analysis, and heuristics to analyze email content, sender reputation, and other factors to determine the probability of a message being spam. EOP maintains a comprehensive spam signature database and continually updates it to enhance its spam detection capabilities.
- Malware Protection: EOP includes built-in antivirus and antimalware scanning to detect and block email attachments that contain malicious code or malware. It scans email attachments in real-time and takes appropriate actions, such as quarantining or deleting the infected attachments to prevent the spread of malware.
- IP Allow/Block Lists: EOP allows administrators to create IP allow and block lists. These lists enable organizations to specify trusted IP addresses or domains from which they want to accept or reject email messages. IP allow/block lists can be used to whitelist trusted senders or block emails originating from suspicious or known malicious sources.
- Connection Filtering: EOP employs connection filtering techniques to block or allow email messages based on the reputation of the sending server. It checks the IP address of the connecting server against various reputation databases and takes action based on the configured policies. This helps block emails from known spam sources and compromised servers.
- Content Filtering: EOP provides content filtering capabilities that allow organizations to define policies to detect and block specific types of content or attachments in email messages. Content filtering can be based on keywords, file types, or specific data patterns. Organizations can define custom content filtering rules to prevent the transmission of sensitive information, enforce compliance, or block specific types of attachments.
- Advanced Threat Protection (ATP): EOP offers Advanced Threat Protection as an add-on service. ATP enhances email security by providing features such as Safe Links, Safe Attachments, and Spoof Intelligence. Safe Links protects users from malicious URLs by scanning and rewriting them to redirect through Microsoft’s servers, which perform real-time analysis. Safe Attachments opens suspicious email attachments in a sandboxed environment to detect and prevent the execution of malware. Spoof Intelligence helps identify and block email spoofing attempts, reducing the risk of phishing attacks.
- Quarantine and Reporting: EOP provides a quarantine feature where suspicious or potentially harmful email messages are held for review. Administrators can access the quarantine to review, release, or delete the quarantined messages. Additionally, EOP offers reporting capabilities that provide insights into email activities, spam detection rates, malware threats, and other statistics for administrators to monitor and analyze the email flow and security posture.
16. Can you discuss the reporting and monitoring capabilities of Exchange Online Protection?
Exchange Online Protection (EOP) provides reporting and monitoring capabilities to help organizations gain insights into their email traffic, security threats, and compliance. These features allow administrators to monitor the effectiveness of their email security measures and make informed decisions. Here are the key reporting and monitoring capabilities of EOP:
- Message Trace: EOP offers the Message Trace feature, which allows administrators to track the delivery of individual email messages within their organization. It provides detailed information about the message flow, including delivery status, time stamps, and recipient details. Message Trace helps administrators troubleshoot email delivery issues, investigate potential security incidents, and track the path of specific messages.
- Mail Flow Dashboard: The Mail Flow Dashboard provides a visual overview of the email flow within the organization. It displays real-time information about the volume of incoming and outgoing emails, the top senders and recipients, and other mail flow statistics. Administrators can use this dashboard to monitor the overall health of email traffic, identify any abnormalities, and track trends.
- Threat Protection Reports: EOP generates various threat protection reports to provide insights into the email security threats faced by the organization. These reports include details about spam detection rates, malware threats, blocked attachments, and false positives. Administrators can analyze these reports to understand the effectiveness of EOP’s security measures and fine-tune their email security policies.
- Quarantine Reports: EOP generates quarantine reports that provide a summary of the messages held in quarantine. These reports list the email messages that have been quarantined due to suspected spam, malware, or other policy violations. Administrators can review the reports, release legitimate messages, and take action against malicious or unwanted emails.
- Data Loss Prevention (DLP) Reports: If DLP policies are implemented in EOP, organizations can access DLP reports. These reports provide information about policy matches, incidents, and policy violations related to the transmission of sensitive information via email. Administrators can use these reports to monitor compliance with data protection policies and identify areas where additional measures may be necessary.
- Advanced Threat Protection (ATP) Reports: If an organization has ATP enabled, EOP generates ATP reports that provide insights into detected threats, Safe Links usage, Safe Attachments scans, and other ATP-related activities. These reports help administrators understand the impact of advanced threats and assess the effectiveness of ATP features.
These reporting and monitoring capabilities enable administrators to assess the effectiveness of their email security measures, identify potential issues, and take proactive steps to protect their organization’s email environment.
17. What is the role of transport rules in Exchange Online Protection (EOP)?
Transport rules play a crucial role in Exchange Online Protection (EOP) as they allow administrators to define conditions and actions for inbound and outbound email messages. These rules are used to enforce policies, automate actions, and control the flow of email traffic within an organization. Here’s an overview of the role of transport rules in EOP:
- Policy Enforcement: Transport rules are used to enforce various policies related to email security, compliance, and organizational guidelines. Administrators can create rules that define specific conditions based on message attributes, such as sender, recipient, subject, or message content. When a message matches the defined conditions, the transport rule triggers specific actions to be taken.
- Data Loss Prevention (DLP): Transport rules can be utilized to implement DLP policies within EOP. Organizations can define rules that inspect the content of email messages to identify sensitive information, such as social security numbers, credit card numbers, or confidential documents. When a message contains sensitive data, transport rules can trigger actions such as blocking, quarantining, or encrypting the message to prevent data loss.
- Encryption and Rights Management: Transport rules can be used to enforce encryption requirements for specific types of email communications. Administrators can create rules that identify messages containing sensitive information and automatically apply encryption or Information Rights Management (IRM) protection using Azure Rights Management Service (RMS). This ensures that sensitive data is secured during transit and only accessible to authorized recipients.
- Email Routing: Transport rules enable administrators to control the routing of email messages within their organization. For example, rules can be created to redirect messages to specific mailboxes or distribution lists based on certain conditions. This allows organizations to implement custom routing scenarios and streamline email distribution based on their specific requirements.
- Compliance and Legal Requirements: Transport rules help organizations meet compliance and legal requirements by enforcing email retention policies, adding disclaimers to outgoing messages, or implementing email archiving. Administrators can create rules that add specific text or legal disclaimers to email messages based on sender, recipient, or message content.
- Automated Actions: Transport rules enable administrators to automate various actions based on predefined conditions. For instance, rules can be created to automatically forward or redirect messages, automatically reply to specific senders or during specific time periods, or delete messages that meet certain criteria. These automated actions help streamline email processing and reduce manual intervention.
- Customization and Flexibility: Transport rules provide a high degree of customization and flexibility, allowing administrators to tailor email processing based on their organization’s specific needs. Multiple rules can be created and prioritized to ensure that the desired actions are taken in the appropriate order when messages meet multiple conditions.
Overall, transport rules in EOP empower administrators to define granular policies, automate actions, and control the flow of email messages to enhance security, compliance, and productivity within their organization.
18. How does Exchange Online Protection handle email routing and delivery?
Exchange Online Protection (EOP) plays a significant role in handling email routing and delivery for organizations. As a cloud-based email filtering service, EOP processes inbound and outbound email messages, applies various security checks, and routes them to their intended recipients. Here’s how EOP handles email routing and delivery:
- Inbound Email Routing: When an email is sent to a domain protected by EOP, the message first reaches the EOP servers. EOP performs various security checks, including anti-spam and anti-malware scanning, to ensure the email is safe and free from threats. Once the email passes these checks, EOP routes it to the intended recipient’s mailbox within the organization.
- Outbound Email Routing: When a user sends an email from within the organization, the email is routed through EOP before being delivered to the recipient. EOP applies security checks and policies, such as data loss prevention (DLP) and content filtering rules, to ensure the email complies with organizational guidelines and security requirements. Once the email is deemed safe, EOP routes it to the appropriate recipient’s email server.
- Smart Host Configuration: EOP allows organizations to configure their email infrastructure to use EOP as a smart host. With this configuration, all outbound email traffic from the organization’s mail servers is sent to EOP for processing and delivery. EOP scans the outbound emails, applies security checks, and delivers them to the intended recipients either within the organization or to external recipients.
- Delivery Status Notifications: EOP generates delivery status notifications (DSNs) to provide information about the status of email delivery. DSNs are sent to the original sender to indicate whether an email was successfully delivered, delayed, bounced, or rejected. These notifications help users track the progress of their sent emails and identify any delivery issues.
- Message Throttling and Queuing: EOP incorporates message throttling mechanisms to manage the flow of email messages. Throttling helps maintain a balanced and efficient delivery process by preventing email floods and managing resource utilization. In cases of high email volumes, EOP may queue the messages for delivery, ensuring a smooth and controlled email flow.
- Fault Tolerance and Redundancy: EOP is designed with fault tolerance and redundancy in mind. Microsoft operates multiple data centers globally to ensure high availability of the service. If one data center experiences an issue, EOP can route email traffic to an alternate data center, ensuring continuous email delivery and minimizing service disruptions.
- Delivery Reports and Tracking: EOP provides reporting and tracking capabilities that allow administrators to monitor the delivery of email messages. Delivery reports provide insights into the status of sent emails, delivery times, and any delivery-related issues. Administrators can use these reports to investigate email delivery problems, troubleshoot issues, and ensure reliable message routing.
Through these mechanisms, Exchange Online Protection ensures secure and efficient email routing and delivery, safeguarding organizations from threats and ensuring reliable communication within and outside the organization.
19. Can you explain the process of managing quarantined messages in Exchange Online Protection?
Exchange Online Protection (EOP) provides administrators with the ability to manage quarantined messages, allowing them to review, release, or take further action on potentially suspicious or unwanted email messages. Here’s an overview of the process of managing quarantined messages in EOP:
- Accessing the Quarantine: Administrators can access the quarantine management interface through the EOP portal or the Security & Compliance Center in Microsoft 365. The quarantine interface provides a centralized view of all email messages that have been quarantined due to suspected spam, malware, or policy violations.
- Viewing Quarantined Messages: In the quarantine management interface, administrators can view a list of quarantined messages. The list typically includes information such as sender, recipient, subject, date, and reason for quarantine (e.g., spam, malware). Administrators can sort, filter, or search the list to locate specific messages.
- Reviewing Message Details: Administrators can select a quarantined message to view its details. This includes the message content, attachments, and any additional information about the reason for quarantine. By reviewing the message details, administrators can assess whether the message is legitimate or requires further action.
- Taking Action on Quarantined Messages: EOP offers several actions that administrators can take on quarantined messages:
a. Release: If a quarantined message is determined to be legitimate, administrators can release it from quarantine. This action delivers the message to the intended recipient’s mailbox.
b. Delete: Administrators can choose to delete a quarantined message if it is identified as spam, contains malicious content, or violates organizational policies. Deleting the message permanently removes it from the quarantine.
c. Report as Not Junk: If a quarantined message is mistakenly identified as spam, administrators can mark it as “not junk.” This action helps train the spam filters to improve future detection accuracy.
d. Safe Sender/Recipient: If a quarantined message is from a trusted sender or recipient, administrators can mark it as a safe sender or recipient. This ensures that future emails from the marked sender or to the marked recipient are not quarantined.
e. Take No Action: Administrators may choose to take no action on certain quarantined messages if they require further investigation or if there is uncertainty about their legitimacy. These messages remain in the quarantine until further action is taken.
5. Customizing Quarantine Settings: EOP allows administrators to customize quarantine settings to fit their organization’s needs. They can define how long quarantined messages are retained, set up notifications to alert administrators about new quarantined messages, and configure policies for automatic release or deletion based on specific criteria.
By managing quarantined messages in Exchange Online Protection, administrators can ensure that legitimate email messages are delivered while maintaining control over potentially harmful or unwanted content. This helps organizations maintain a secure and efficient email environment.
20. What are the available options for configuring Exchange Online Protection for outbound email?
Exchange Online Protection (EOP) provides several options for configuring outbound email settings to enhance security, compliance, and control. These options allow organizations to customize their outbound email handling according to their specific requirements. Here are the available options for configuring EOP for outbound email:
- Content Filtering: EOP enables administrators to define content filtering policies for outbound email messages. Content filtering allows organizations to prevent the transmission of sensitive or inappropriate content, enforce compliance with regulatory requirements, and protect against data loss. Administrators can create rules based on keywords, file types, or specific data patterns to scan outgoing messages and take appropriate actions, such as blocking, quarantining, or encrypting emails.
- Data Loss Prevention (DLP): EOP integrates with Microsoft Data Loss Prevention (DLP) capabilities, allowing organizations to implement policies that identify and prevent the transmission of sensitive information via email. Administrators can create DLP policies to detect and block email messages containing confidential data, such as credit card numbers, social security numbers, or intellectual property. When a DLP policy is triggered, actions like blocking, encrypting, or notifying the sender can be taken to prevent data leakage.
- Message Encryption: EOP supports message encryption to ensure secure communication and protect sensitive information. Administrators can configure encryption rules to automatically encrypt outgoing emails that contain specific keywords, meet certain criteria, or are sent to specific recipients. Encrypted messages can only be decrypted by authorized recipients, providing an extra layer of security during transit.
- Outbound Spam Filtering: EOP includes outbound spam filtering to prevent the organization’s email system from being used to send spam or unsolicited bulk emails. EOP applies various techniques, including reputation analysis, content analysis, and behavior monitoring, to detect and block outbound spam. Administrators can customize the spam filtering settings and actions to ensure that legitimate emails are delivered while preventing the sending of spam.
- Transport Rules: Transport rules in EOP allow administrators to define specific conditions and actions for outbound email messages. These rules can be used to enforce policies, automate actions, and control the flow of outbound email traffic. Administrators can create rules based on sender, recipient, subject, or message content to apply actions such as adding disclaimers, routing messages to specific destinations, or applying message encryption.
- Smart Host Configuration: Organizations can configure their on-premises mail servers or other email infrastructure to use EOP as a smart host. With this configuration, outbound email traffic is directed to EOP for processing and delivery. EOP applies security checks, such as spam filtering and content scanning, before delivering the messages to their intended recipients. Smart host configuration ensures that outbound emails are filtered and secured by EOP before leaving the organization’s network.
By leveraging these configuration options, organizations can customize Exchange Online Protection for outbound email to ensure compliance, protect sensitive information, prevent spam, and enforce security measures that align with their specific needs and policies.
21. What are the considerations for implementing Exchange Online Protection (EOP) in a hybrid environment?
Implementing Exchange Online Protection (EOP) in a hybrid environment, where some mailboxes are hosted on-premises while others are in Exchange Online, requires careful planning and consideration. Here are some key considerations for implementing EOP in a hybrid environment:
- Mail Flow Configuration: In a hybrid environment, you need to configure the mail flow between your on-premises Exchange servers and Exchange Online. This involves setting up connectors and ensuring proper routing of inbound and outbound email traffic between the two environments. EOP can be configured as the smart host for outbound email from your on-premises servers, allowing it to scan and filter outbound messages before delivery.
- Hybrid Mail Flow and Message Tracking: It’s essential to ensure that mail flow and message tracking between on-premises and Exchange Online mailboxes function seamlessly. This includes configuring connectors, message routing, and ensuring that message tracking logs are synchronized and accessible for end-to-end visibility of email delivery.
- Directory Synchronization: In a hybrid environment, you typically have directory synchronization in place to ensure that user accounts and attributes are synchronized between your on-premises Active Directory and Azure Active Directory (AAD). This synchronization is crucial for maintaining a unified address book, recipient management, and consistent email routing.
- Centralized Management: Implementing EOP in a hybrid environment requires a centralized management approach. You need to determine how you will manage EOP settings and policies for both on-premises and Exchange Online mailboxes. This may involve using Exchange Online PowerShell, Exchange Admin Center (EAC), or a combination of both to configure and manage EOP settings.
- Message Protection and Compliance: Consider how you will handle message protection and compliance in a hybrid environment. EOP provides features like anti-spam, anti-malware scanning, and data loss prevention (DLP). You need to ensure consistent application of these features across on-premises and Exchange Online mailboxes to maintain security and compliance standards.
- User Experience and Authentication: In a hybrid environment, users may have different experiences based on whether their mailbox is on-premises or in Exchange Online. Consider how you will manage authentication, single sign-on (SSO), and user experience to provide a seamless email experience regardless of the mailbox location.
- Coexistence and Migration: If you are migrating mailboxes from on-premises to Exchange Online, ensure that coexistence is properly configured during the migration process. This includes setting up hybrid configuration, configuring free/busy and calendar sharing, and managing mailbox moves to minimize disruption and ensure a smooth transition.
- Reporting and Monitoring: Consider how you will monitor and report on the performance, security, and compliance aspects of your hybrid environment. EOP provides reporting and monitoring capabilities that you can leverage to gain insights into email traffic, threat detection, and compliance status.
Implementing EOP in a hybrid environment requires a comprehensive understanding of both on-premises and Exchange Online environments, careful planning, and proper configuration to ensure smooth mail flow, consistent security, and compliance across the hybrid infrastructure. Microsoft provides detailed documentation and best practices to guide organizations through the implementation process.
22. Can you explain the process of troubleshooting common issues in Exchange Online Protection (EOP)?
Troubleshooting common issues in Exchange Online Protection (EOP) involves a systematic approach to identify and resolve problems related to email delivery, security, or configuration. Here’s a general process to help troubleshoot common issues (troubleshooting steps may vary depending on the specific issue) in EOP:
- Gather Information: Start by gathering relevant information about the issue. This may include details about the affected users, specific error messages or symptoms, and any recent changes or events that may have triggered the problem. Check if the issue is affecting all users or specific mailboxes or domains.
- Check Service Health: Verify the service health status of Exchange Online and EOP by checking the Microsoft 365 Service Health dashboard. It provides information about any ongoing service disruptions or known issues that may be causing the problem.
- Review Message Tracking Logs: Utilize the message tracking feature in EOP to track the flow of specific email messages and identify any issues. Review the logs to determine if the messages are being delivered, rejected, or delayed. This can help pinpoint where the problem is occurring in the mail flow.
- Validate DNS Configuration: Verify that your DNS records, such as MX (Mail Exchange) and SPF (Sender Policy Framework) records, are correctly configured. Ensure that your domain’s DNS settings are pointing to the correct EOP endpoints and that SPF records are properly set to allow EOP to send email on behalf of your domain.
- Check Connection and Connectivity: Ensure that your network connectivity is stable and that there are no issues with your internet connection. Test the connectivity between your on-premises environment (if applicable) and Exchange Online. Verify that firewalls, proxies, or other network devices are not blocking any necessary ports or protocols.
- Review Exchange Online Protection Policies: Check your EOP policies, including anti-spam, anti-malware, and content filtering policies. Ensure that the policies are properly configured and not inadvertently blocking or quarantining legitimate email messages.
- Analyze NDRs and Delivery Status Notifications: Non-Delivery Reports (NDRs) and Delivery Status Notifications (DSNs) provide valuable information about email delivery failures. Analyze the content of NDRs or DSNs received by users to identify specific error codes or reasons for delivery failures.
- Review Quarantine: Check the EOP quarantine for any false positives or legitimate emails that may have been mistakenly quarantined. Release or manage quarantined messages as necessary.
23. How does Exchange Online Protection handle bulk email and mailing lists?
Exchange Online Protection (EOP) includes features and mechanisms to handle bulk email and mailing lists effectively while maintaining email security and preventing abuse. Here’s how EOP handles bulk email and mailing lists:
- Anti-Spam Filtering: EOP applies robust anti-spam filtering mechanisms to identify and block unsolicited bulk email (spam). It uses various techniques, such as content analysis, reputation-based filtering, and real-time blacklists, to detect and block spam messages. This helps ensure that bulk email messages that are considered spam are intercepted and prevented from reaching recipients’ inboxes.
- Content Filtering Policies: Administrators can create content filtering policies in EOP to apply specific rules and actions to inbound and outbound email messages. These policies can be used to control the flow of bulk email and mailing lists. For example, administrators can define rules to block or quarantine messages with certain characteristics commonly associated with bulk email, such as specific keywords, large recipient lists, or excessive message size.
- Bulk Email Thresholds: EOP allows administrators to set thresholds for bulk email detection. These thresholds help distinguish between legitimate bulk email (such as newsletters or announcements) and unsolicited spam. By setting appropriate thresholds, organizations can customize the handling of bulk email based on their specific needs. For example, messages that surpass the threshold can be flagged for further review or subjected to additional scrutiny.
- Recipient and Sender Limits: EOP provides options to configure recipient and sender limits to control the volume and frequency of email messages. These limits help prevent abuse by limiting the number of recipients per message or the rate at which messages can be sent. By enforcing these limits, EOP ensures that bulk email or mailing list activity does not overwhelm the system or affect the performance of email delivery.
- Safelisting and Blocklisting: EOP allows administrators to maintain safelists and blocklists to manage trusted senders and known spammers. Administrators can add trusted sources (such as legitimate mailing lists) to the safelist to ensure that messages from those sources are not incorrectly identified as spam. Conversely, known spammers or sources of unsolicited bulk email can be added to the blocklist to prevent their messages from reaching recipients.
By implementing these features and practices, EOP effectively handles bulk email and mailing lists. It helps prevent spam, protects users from unsolicited bulk email, and ensures that legitimate bulk email is delivered while maintaining email security and compliance.
24. Can you explain the role of Exchange Online Protection (EOP) in protecting against zero-day attacks?
Exchange Online Protection (EOP) plays a crucial role in protecting against zero-day attacks, which are attacks that exploit vulnerabilities that are unknown to the software vendor and have no available patches or signatures. Here’s how EOP helps mitigate the risks associated with zero-day attacks:
- Real-Time Threat Intelligence: EOP leverages real-time threat intelligence from multiple sources, including Microsoft’s extensive threat intelligence network. This enables EOP to identify and respond to emerging threats, including zero-day attacks. The threat intelligence is continuously updated to detect patterns and indicators of compromise associated with new and evolving threats.
- Advanced Threat Protection (ATP): EOP integrates with Advanced Threat Protection (ATP), which provides additional layers of protection against zero-day attacks. ATP uses machine learning algorithms, behavior analysis, and sandboxing techniques to detect and prevent sophisticated threats that may be unknown or have no known signatures. ATP can analyze email attachments, URLs, and malicious behaviors to identify potential zero-day attacks and block them before they reach users’ inboxes.
- Safe Attachments: EOP’s Safe Attachments feature provides an extra layer of defense against zero-day attacks delivered through email attachments. Safe Attachments uses sandboxing technology to open and analyze suspicious attachments in a secure environment. If the attachment is found to be malicious, it is blocked, preventing potential zero-day exploits from executing on users’ devices.
- Safe Links: EOP’s Safe Links feature helps protect against zero-day attacks delivered through malicious URLs in email messages. Safe Links checks every clicked URL in real-time to determine if it leads to a known malicious website or if it exhibits suspicious behavior. If a URL is identified as malicious or suspicious, Safe Links blocks access to the website, preventing users from being exposed to zero-day exploits or other threats.
- Machine Learning and Behavioral Analysis: EOP incorporates machine learning and behavioral analysis techniques to detect anomalies and patterns associated with zero-day attacks. By analyzing the characteristics of incoming email messages and their behavior, EOP can identify potential zero-day threats even if they lack traditional signatures or indicators. This proactive approach helps protect against emerging and unknown threats.
- Security Updates and Response: Microsoft actively monitors the threat landscape and releases security updates and patches to address vulnerabilities and protect against zero-day attacks. EOP ensures that these security updates are automatically applied to provide the latest protections against known and potential zero-day threats.
25. How does Exchange Online Protection (EOP) handle inbound email throttling and rate limiting?
Exchange Online Protection (EOP) incorporates inbound email throttling and rate limiting mechanisms to manage the flow of incoming email messages. These features help ensure optimal performance, prevent abuse, and protect against email-based attacks. Here’s how EOP handles inbound email throttling and rate limiting:
- Connection Filtering: EOP applies connection filtering to limit the number of simultaneous connections from a single sender or IP address. This helps prevent abuse by malicious senders or compromised systems that attempt to flood the email infrastructure with a high volume of connections. Connection filtering also helps protect against Distributed Denial of Service (DDoS) attacks.
- Recipient and Sender Rate Limiting: EOP imposes rate limits on the number of messages that can be sent to or from specific recipients or senders within a specified time frame. These rate limits are designed to prevent abuse and protect against email-based attacks such as spam or targeted attacks. By enforcing these limits, EOP ensures that the email infrastructure is not overwhelmed by a high volume of messages from a single source.
- Throttling Policies: Administrators can configure throttling policies in EOP to control the flow of incoming email messages based on various parameters. These policies allow administrators to define specific limits for attributes such as message size, recipient count, or the number of connections from a particular sender. Throttling policies help prevent resource exhaustion and ensure fair usage of system resources.
- IP Reputation and IP Allow/Block Lists: Exchange Online Protection (EOP) incorporates IP reputation filtering to assess the reputation of the sending IP addresses. If an IP address is identified as having a poor reputation due to spamming or other malicious activities, EOP may apply stricter rate limits or block incoming email from that IP address. Administrators can also configure IP allow and block lists to explicitly allow or block specific IP addresses or ranges.
- Bulk Email Thresholds: EOP allows administrators to define thresholds for distinguishing between bulk email and regular email. By setting appropriate thresholds, organizations can apply specific handling or filtering rules to bulk email, such as newsletters or mailing lists, while maintaining optimal performance and security. This helps prevent legitimate bulk email from being incorrectly classified as spam.
- Automatic Throttling and Backpressure: Exchange Online Protection (EOP) incorporates automatic throttling and backpressure mechanisms to dynamically adjust the processing of incoming email based on system load and resource availability. If the system is under heavy load, EOP may temporarily throttle the processing of incoming email to ensure stability and prevent performance degradation.
These inbound email throttling and rate limiting mechanisms in Exchange Online Protection (EOP) help maintain the performance, stability, and security of the email infrastructure. By controlling the flow of incoming email and preventing abuse, EOP ensures that legitimate email is delivered efficiently while mitigating the impact of spam, attacks, and resource exhaustion.
Exchange online protection interview questions and answers for advanced level
26. How does Exchange Online Protection (EOP) handle email spoofing and impersonation attempts?
Exchange Online Protection (EOP) includes features and capabilities to help detect and mitigate email spoofing and impersonation attempts. Here’s how EOP handles these threats:
- Sender Authentication: Exchange Online Protection (EOP) leverages various sender authentication mechanisms, such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC), to validate the authenticity of email senders. These authentication methods help verify that the sending domain is legitimate and prevent spoofed emails from being delivered.
- Spoof Intelligence: EOP utilizes spoof intelligence to detect common spoofing patterns and identify potentially malicious email messages. It examines various attributes of the email, including the sender’s display name, email address, and message headers, to identify signs of spoofing or impersonation attempts. Exchange Online Protection (EOP) employs machine learning algorithms to continuously learn and adapt to evolving spoofing techniques.
- Anti-Phishing Policies: Exchange Online Protection (EOP) allows administrators to create anti-phishing policies to protect against email phishing attacks, which often involve impersonation. These policies can include rules and actions that flag or block email messages based on specific criteria, such as spoofed sender domains or suspicious display names. Administrators can configure policies to apply customized actions, such as quarantining or redirecting suspicious messages.
- Transport Rules: Administrators can create transport rules in Exchange Online Protection (EOP) to apply specific actions based on the characteristics of incoming email messages. These rules can be used to identify and handle spoofed or impersonated messages. For example, rules can be set up to flag or block messages where the sender’s display name matches a specific pattern or where the sender’s email address doesn’t align with the sender’s domain.
27. What are the considerations for managing custom domains and connectors in Exchange Online Protection (EOP)?
When managing custom domains and connectors in Exchange Online Protection (EOP), there are several considerations to keep in mind. Here are some important factors to consider:
- Domain Verification: Before you can start using a custom domain with Exchange Online Protection (EOP), you need to verify ownership of the domain. This involves adding specific DNS records to your domain’s DNS configuration as part of the verification process. Ensure that you have the necessary permissions to modify the DNS settings for your custom domain.
- DNS Configuration: Proper DNS configuration is crucial for the smooth operation of your custom domain with EOP. Ensure that the necessary DNS records, such as MX (Mail Exchange) and SPF (Sender Policy Framework), are correctly configured to direct email traffic to EOP. These records help ensure proper email routing and help prevent email spoofing and abuse.
- Hybrid Environment Considerations: If you have a hybrid environment with both on-premises Exchange servers and Exchange Online, you’ll need to configure connectors to enable seamless mail flow between the two environments. Connectors establish the necessary communication pathways for email delivery. Ensure that the connectors are properly configured to ensure smooth communication between the on-premises and cloud environments.
- Inbound and Outbound Connectors: Exchange Online Protection (EOP) allows you to create inbound and outbound connectors to manage the flow of email for your custom domain. Inbound connectors handle incoming email from external sources, while outbound connectors control the delivery of outbound email from your organization. Configure these connectors based on your organization’s specific requirements and policies.
- Secure Communication: When configuring connectors, consider enabling secure communication using Transport Layer Security (TLS) encryption. TLS helps ensure that email communication between your organization and external entities is encrypted and secure. This is particularly important when transmitting sensitive or confidential information.
- Anti-Spam and Anti-Malware Policies: Ensure that your custom domain is covered by appropriate anti-spam and anti-malware policies in EOP. Configure these policies to protect your organization’s email environment from unsolicited spam and malicious attachments. Regularly review and update these policies to adapt to evolving threats.
- Domain-Based Message Authentication, Reporting, and Conformance (DMARC): Consider implementing DMARC for your custom domain. DMARC helps prevent email spoofing and impersonation by providing policies for email receivers to validate the authenticity of messages originating from your domain. DMARC policies can help protect your domain’s reputation and improve email deliverability.
- Monitoring and Reporting: Regularly monitor the performance and effectiveness of your custom domain configuration in EOP. Leverage the available reporting and monitoring capabilities to track email delivery, identify issues, and ensure the proper functioning of your custom domain.
- Administrative Access and Permissions: Ensure that the appropriate administrative access and permissions are granted to manage custom domains and connectors in Exchange Online Protection (EOP). Assign roles and permissions to administrators responsible for managing these configurations, ensuring they have the necessary privileges to make changes and troubleshoot issues.
By considering these factors, you can effectively manage custom domains and connectors in Exchange Online Protection.
28. How does Exchange Online Protection (EOP) handle email forwarding and redirection?
Exchange Online Protection (EOP) provides features to handle email forwarding and redirection in a secure and controlled manner. Here’s how EOP handles these processes:
- Inbox Rules: Exchange Online Protection (EOP) allows users to create inbox rules to automatically forward or redirect incoming emails to another recipient or external email address. These rules can be set up based on various conditions, such as sender, subject, or content of the email. Users have control over managing their own inbox rules, but administrators can also define organization-wide rules and policies to regulate email forwarding.
- External Recipient Warning: When a user sets up email forwarding or redirection to an external email address, Exchange Online Protection (EOP) can apply a warning message to the email indicating that it has been redirected to an external recipient. This warning helps increase awareness and prevents accidental data leakage or unauthorized email forwarding.
- Transport Rules: Administrators can create transport rules in EOP to enforce policies and restrictions on email forwarding and redirection. Transport rules allow administrators to define conditions and actions that apply to email messages passing through the EOP infrastructure. For example, administrators can create rules to restrict or block specific users or groups from forwarding emails outside the organization.
- Data Loss Prevention (DLP) Policies: Exchange Online Protection (EOP) integrates with Data Loss Prevention policies to help prevent the unauthorized forwarding or redirection of sensitive or confidential information. DLP policies can scan email content for sensitive data, such as credit card numbers or personally identifiable information (PII), and apply actions to prevent forwarding or redirecting such emails.
- Anti-Spoofing Measures: Exchange Online Protection (EOP) incorporates anti-spoofing measures, such as SPF, DKIM, and DMARC, to verify the authenticity of email senders. These mechanisms help prevent malicious actors from spoofing email addresses and redirecting emails to unauthorized recipients.
- Monitoring and Reporting: Exchange Online Protection (EOP) provides monitoring and reporting capabilities to track email forwarding and redirection activities. Administrators can analyze logs and reports to identify any suspicious or unauthorized forwarding behavior, allowing them to take appropriate action to mitigate risks.
29. Can you explain the options for managing user-level spam settings in Exchange Online Protection (EOP)?
In Exchange Online Protection (EOP), there are several options available for managing user-level spam settings. These settings allow users to customize their spam filtering preferences according to their individual needs. Here are the key options for managing user-level spam settings in EOP:
- Junk Email Folder: Exchange Online Protection (EOP) automatically directs suspected spam emails to the user’s Junk Email folder. Users can access this folder to review and manage emails that have been identified as spam. They can manually move messages in and out of the Junk Email folder, mark messages as not junk, or delete them as needed.
- Safe Senders and Recipients: Users can maintain a list of safe senders and recipients. Emails from these trusted sources are not treated as spam and are delivered to the user’s inbox. Users can add email addresses or domains to their safe senders and recipients lists to ensure that important emails from specific sources are not mistakenly classified as spam.
- Blocked Senders: Users can create a list of blocked senders to prevent emails from specific sources from reaching their inbox. Emails from these blocked senders are automatically redirected to the Junk Email folder or completely blocked, depending on the user’s preferences.
- Safe Links: Safe Links is a feature in EOP that helps protect against malicious URLs in email messages. Users can enable or disable Safe Links for their mailbox. When Safe Links is enabled, URLs in incoming emails are scanned and rewritten to redirect through Microsoft’s servers to check for potential threats before allowing access. This provides an additional layer of protection against spam and phishing emails.
- Reporting False Positives and False Negatives: Exchange Online Protection (EOP) allows users to report false positives (legitimate emails marked as spam) and false negatives (spam emails that were not caught). Users can use the “Not Junk” or “Junk” buttons in their email client to report these instances. Reporting false positives and false negatives helps improve the accuracy of the spam filtering system.
- Quarantine Management: Depending on the organization’s configuration, users may have the ability to manage their own quarantine. Quarantine is a temporary holding area where potentially harmful or suspicious emails are placed before being delivered to the user’s inbox or moved to the Junk Email folder. Users can review and release emails from their quarantine if they believe a message was wrongly classified.
30. How does Exchange Online Protection (EOP) handle email authentication protocols such as SPF, DKIM, and DMARC?
Exchange Online Protection (EOP) incorporates email authentication protocols such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to enhance email security and prevent email spoofing and phishing attacks. Here’s how EOP handles these authentication protocols:
- SPF (Sender Policy Framework): SPF is an email authentication protocol that helps verify the authenticity of the sender’s domain. When an email is received, EOP checks the SPF record published in the sender’s domain’s DNS (Domain Name System). SPF records contain a list of authorized IP addresses or domains that are allowed to send email on behalf of the domain. EOP checks if the sending server’s IP address matches the authorized IP addresses listed in the SPF record. If there’s a match, the email passes SPF authentication.
- DKIM (DomainKeys Identified Mail): DKIM is an email authentication method that uses cryptographic signatures to verify the integrity of the email message and its source. When an email is sent from a DKIM-enabled domain, the sending server adds a digital signature to the email headers using a private key. The recipient’s email server, including EOP, can then verify the signature by retrieving the public key from the domain’s DNS records. If the signature is valid, it confirms that the email has not been tampered with during transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC is a policy framework that builds upon SPF and DKIM to provide further protection against email spoofing and phishing attacks. DMARC allows domain owners to publish policies specifying how receivers (such as EOP) should handle emails that fail SPF and DKIM checks. The DMARC policy can instruct the receiver to quarantine or reject emails that fail authentication, or it can provide guidance on how to handle them. DMARC also includes reporting mechanisms that provide visibility into how the domain is being used and whether unauthorized sending activity is taking place.
Exchange Online Protection (EOP) leverages SPF, DKIM, and DMARC to assess the authenticity and legitimacy of incoming email messages. By validating sender domains, checking for DKIM signatures, and analyzing DMARC policies, EOP can make informed decisions about the handling of emails, including identifying and mitigating email spoofing, phishing attempts, and unauthorized use of domain names.
Organizations can configure and manage SPF, DKIM, and DMARC settings in Exchange Online Protection (EOP) through the Exchange Admin Center or PowerShell commands. By properly configuring and monitoring these email authentication protocols, organizations can enhance their email security, reduce the risk of spoofing and phishing attacks, and protect their reputation.
31. How does Exchange Online Protection (EOP) handle email compliance with industry regulations (e.g., GDPR, HIPAA)?
Exchange Online Protection (EOP) includes features and capabilities to help organizations meet email compliance requirements imposed by industry regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Here’s how EOP addresses email compliance:
- Data Loss Prevention (DLP): Exchange Online Protection (EOP) integrates with Data Loss Prevention policies to help prevent the unauthorized disclosure of sensitive information in emails. DLP policies can be configured to detect and take action on emails that contain specific types of sensitive data, such as personally identifiable information (PII), financial data, or healthcare-related information. EOP’s DLP capabilities allow organizations to define and enforce policies that align with GDPR, HIPAA, and other regulatory requirements.
- Transport Rules: Exchange Online Protection (EOP) allows administrators to create transport rules to apply specific actions based on email attributes and content. These rules can be used to enforce compliance requirements by automatically applying actions such as adding confidentiality disclaimers, encrypting emails containing sensitive information, or blocking specific types of attachments that may violate regulations.
- Encryption and Secure Communication: Exchange Online Protection (EOP) supports encryption capabilities to protect sensitive email content during transmission. Administrators can configure Transport Layer Security (TLS) encryption to ensure secure communication between EOP and other email systems. Additionally, EOP integrates with Microsoft Information Protection (MIP) to enable email encryption and rights protection, helping organizations protect sensitive information and comply with data protection regulations.
- Archiving and Retention: EOP integrates with Microsoft 365’s compliance and security features, including Exchange Online Archiving and Microsoft 365 Compliance Center. These features allow organizations to implement email archiving and retention policies to meet regulatory requirements. Organizations can define policies for retaining and managing email data based on specific retention periods, legal holds, or compliance requirements.
- Audit Logging and Reporting: Exchange Online Protection (EOP) provides logging and reporting capabilities that help organizations monitor and track email-related activities to ensure compliance with industry regulations. Administrators can access audit logs and reports to review email flows, investigate incidents, and demonstrate compliance with regulatory requirements.
32. What are the recommended practices for disaster recovery and backup strategies in Exchange Online Protection (EOP)?
When it comes to disaster recovery and backup strategies in Exchange Online Protection (EOP), it’s important to consider the following recommended practices:
- Microsoft 365 Data Retention: EOP is a part of Microsoft 365, and Microsoft provides built-in data redundancy and disaster recovery measures for the services within the Microsoft 365 platform. Microsoft manages data replication, backups, and disaster recovery at the infrastructure level to ensure data resiliency and availability.
- Exchange Online Archiving: Implementing Exchange Online Archiving, which is an optional add-on service to EOP, can provide an additional layer of protection and backup for email data. Exchange Online Archiving provides long-term retention and backup capabilities, allowing organizations to store and protect their email data for compliance and disaster recovery purposes.
- Third-Party Backup Solutions: While Microsoft manages data replication and infrastructure-level backups, organizations may choose to implement third-party backup solutions to have more granular control and additional layers of protection. These solutions can provide point-in-time backups, individual item recovery, and more flexible recovery options.
- Retention Policies and Legal Holds: Utilize retention policies and legal holds in Exchange Online to ensure that critical email data is retained for the required periods, as dictated by compliance regulations. Retention policies help protect against accidental or intentional deletion of emails, while legal holds preserve emails as evidence for legal or regulatory purposes.
- Testing and Validation: Regularly test and validate the effectiveness of your disaster recovery and backup strategies. Conduct mock disaster scenarios to ensure the recoverability of data and verify that backups are functioning as expected. This helps identify any gaps or issues in the backup and recovery processes and allows for necessary adjustments or improvements.
Further resources
Thank you for taking time to read our post on Exchange Online Protection (EOP) interview questions and answers. We welcome you to browse through our other posts on interview questions and answers.
Mastering Exchange Server 2019 Interview Questions and Answers: Ultimate guide.
50+ Exchange Online Mail Flow Interview questions and answers
Empowering Your Exchange Server 2010 Journey with Expert Interview Questions and Answers
50+ Microsoft Exchange Server Interview Questions and Answers
40+ Azure AD Connect Interview Questions and Answers
Top 40+ Azure Active Directory interview questions and answers
Top 50+ Office 365 Interview questions and answers
40+ Exchange Hybrid Interview questions and answers
50+ Microsoft Exchange Online interview questions and answers
Good Luck!
