Demystifying Exchange Online Protection (EOP)
In this article you will learn how email headers are stamped by Exchange Online Protection (EOP), and how Exchange Online Protection scans incoming and outgoing emails. This article is going to be a deep dive session on Exchange Online Protection architecture.
Table of Contents
Watch the video
Please watch this video to learn how email flow works step by step in Exchange Online and how EOP scans the emails.
How Email works step by step
Before we understand how Exchange Online Protection works and how to bypass it, let’s first take a deeper look at how email works step by step in Exchange Online.
Email operates through a series of steps involving both the sender’s and recipient’s email servers. Let’s assume a user (John) who is using Gmail, wants to send an email to a user (Bob) whose mailbox is hosted in Exchange Online.
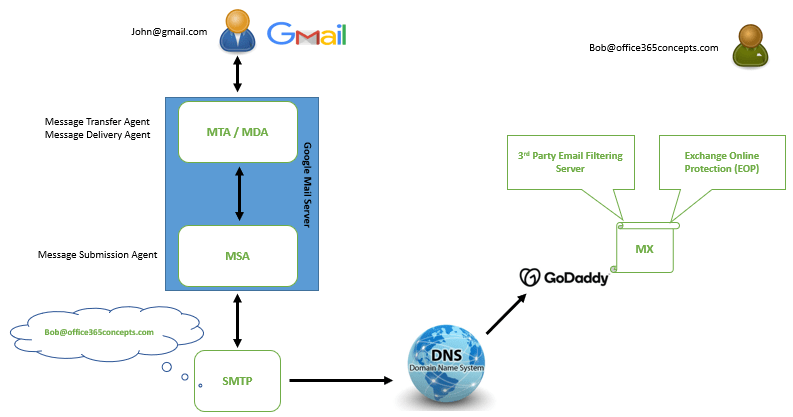
John will login to his Gmail account, will compose an email, and in TO field he will type Bob’s email address Bob@office365concepts.com.
Note: Every mailbox provider has an email server that is responsible to process the emails. For example, Exchange server, Exchange Online Protection (EOP), Gmail, Yahoo mail server and so on. In this example, emails sent from Gmail, or received in the Gmail mailbox, will be processed by Google Mail Server.
As soon as John will send email from his Gmail account, that email will picked up by Message Transfer Agent (MTA) and will handover it to Message Submission Agent (MSA). Message Transfer Agent and Message Submission Agent are the services that run on the email servers. These services are responsible to pick the emails from the client applications and send these emails for further processing.
Then SMTP service will pick that email from Message Submission Agent. Now….. SMTP service knows that i need to deliver this email to Bob@office365concepts.com. But it doesn’t know where this user is. SMTP service doesn’t know who is Bob. It only knows that if I find office365concepts.com domain, I will find the user also.
SMTP service will reach out to the DNS (Domain Name Service), and will ask for this domain information. DNS will consult its own internal servers, like, Root Server, Top Level Domain server, Authoritative Nameserver, and will route the SMTP service to the domain provider where this domain is hosted. From the domain provider portal, SMTP service will find the MX record for this domain. Now SMTP service knows how it can reach this domain.
Important: MX record is used to receive emails. MX record tells the email servers where to route the emails for a particular domain.
Now there can be 2 scenarios. We can point MX record for this domain to a 3rd party email filtering server like, Barracudda or Sophos, or we can point it to Exchange Online Protection (EOP).
Let’s assume the MX record for office365concepts.com is pointed to a 3rd party email filtering server, like Sophos. When we integrate an email filtering server with Exchange Online Protection, we create one Inbound connector in Exchange Online (EXO) that accepts the emails from the server, and we create one outbound connector that sends emails from Exchange Online to email filtering server.
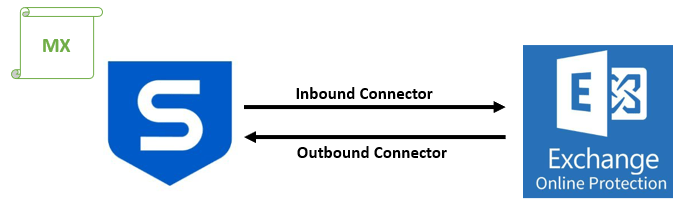
So with the help of MX record, email will be delivered to Sophos. And with the help of Inbound Connector, this email will be routed to Exchange Online Protection (EOP). And if MX record is pointed to Exchange Online Protection, then email will be delivered to EOP directly.
Now let’s understand how Exchange Online Protection will scan this email.
Exchange Online Mail Flow diagram
Let’s dive deep into the Exchange Online mail flow architecture and let’s understand how Exchange Online Protection (EOP) scans incoming and outgoing emails.
Exchange Online Protection Architecture / How EOP works
Exchange Online Protection (EOP) is a cloud-based email filtering service provided by Microsoft. It is designed to help protect your organization’s email environment against spam, malware, viruses, phishing attacks, and other threats. Exchange Online Protection is integrated with Microsoft Exchange Online, which is part of Microsoft 365 (formerly Office 365), but it can also be used with on-premises Exchange Server deployments. Exchange Online Protection (EOP) runs on a world wide network of datacenters to provide high availability. If one datacenter becomes unavailable, the emails are routed through another datacenter without interruption.
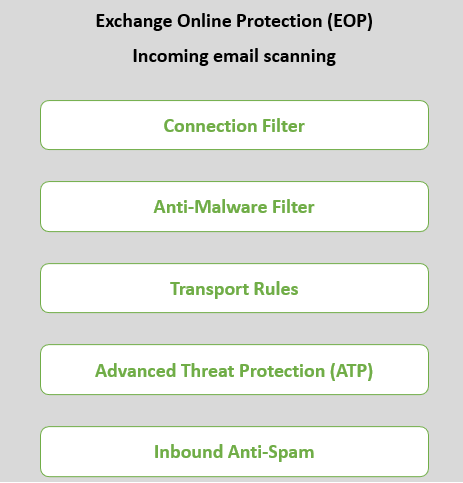
Exchange Online Protection (EOP) uses multiple email filters to scan the emails. These filters are Connection Filter, Anti-malware filter, Transport rules (mail flow rules), Advanced Threat Protection (ATP) / Microsoft Defender for Office 365, Anti-spam (Content Filtering), and Zero-hour auto purge (ZAP).
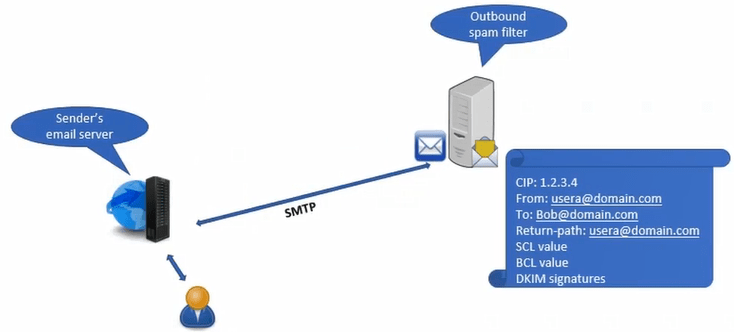
When an email server processes an email, it adds some information within the email header of that particular email, like, Connecting IP Address, Mail-FROM address, TO address and Return-Path. This email header will play a big role when this email will be scanned by Exchange Online Protection, or by any email filtering solution.
Important: To learn how to analyze email header and learn the components of email header, please refer to this link.
After adding necessary information within the email header, email server will forward that email to their outbound spam filtering server. Outbound spam filtering server will perform checks as per the configuration done within outbound filtering policies, and during this process, outbound server will add some more values within the email header. For example, SCL value, BCL value, and DKIM signatures.
Connection Filter
As soon as this email reaches Exchange Online Protection (EOP), Connection Filter runs few checks on this email. Connection Filter adds the Connecting IP address to the X-Forefront-Antispam-Report section within the email header. (This IP address can be added within the allow list or block list of connection filtering policy, if we want to allow or block email from this IP address).
Then Connection Filter performs Directory Based Edge Blocking (DBEB) checks. During this check, if the recipient address is not found within Azure Active Directory, the email will be dropped and the sender will receive Non Delivery Report (NDR) with error code 550 5.1.10 RecipientNotFound.
In the next step, Connection Filter checks the Allow list and Block list of the connection filter policy. If the connecting IP address matches an entry in the connection filter block list, email will be dropped. If the connecting IP address matches an allow list entry within connection filter policy, then the IPV value in the message header will be set to IPV:CAL.
Important: IPV:CAL indicates that the message skipped spam filtering because the source IP address was in the IP Allow List of the Connection Filter policy.
In the next step, Connection Filter performs Safe List checks. In Connection Filter policy there is an option called Turn on Safe List that is maintained by Microsoft using third-party sources of trusted senders.
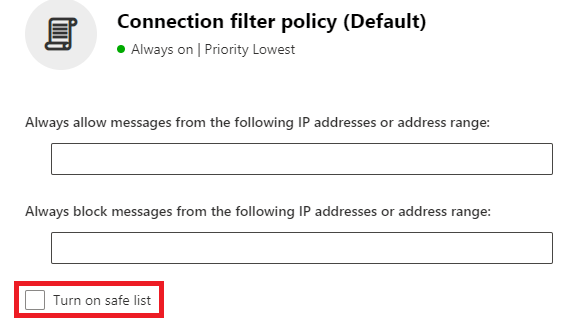
Enabling this feature means, the emails sent from the trusted senders (added within the Safe List) are not marked as SPAM. If the connecting IP address of the sender matches an entry in the Microsoft IP safe list, the IPV value is set to IPV:CAL, and SCL will be set to SCL = -1, and SFV will be set to SFV:SKN.
The last step which is performed within Connection Filter is, Reputation Block. Microsoft maintains a reputation list of IP addresses, that helps to determine if the email was sent from a bad reputation IP address or not. If the email is sent from a bad reputation IP address, the email will be dropped. The sender can go to sender.office.com and can delist the IP address from this portal (provided the IP address is listed in Microsoft servers). If the sender’s IP address is not listed in Microsoft reputation list, Connection Filter will stamp IPV value to IPV:NLI within X-Forefront-Antispam-Report. IPV:NLI means the IP address was not listed on any reputation list.
Anti-Malware
The next email filter in Exchange Online Protection (EOP) is Anti-Malware. Anti-Malware policies protects the email messages from 3 types of malware:
- Viruses: Viruses infect other programs and data, and spread through your computer or network looking for programs to infect.
- Spyware: Spyware gathers your personal information, such as sign-in information and personal data, and sends it back to its author.
- Ransomware: Ransomware encrypts your data and demands payment to decrypt it. Anti-malware doesn’t decrypt the encrypted files, but it can detect the malware associated with the ransomware.
Anti-Malware policy scans the email message attachments and the body, and if malware is found, emails are quarantined. By default, messages that were quarantined due to malware can only be viewed and released by the admins.
Important: If you want to find out if Malware Filter Agent processed an email, analyze Extended Message Trace (EMT) and look for S:AMA value in the Custom Data section.
Transport Rules (Mail Flow Rules)
If the email passes Anti-Malware checks, it is then evaluated against the transport rules (mail flow rules). Transport rules are the policies that define and enforce mail flow settings within an organization. These rules allow administrators to control the flow of email messages based on the specific conditions, such as sender, recipient, message content, and more.
Important: If you want to find out if Transport Rules (Mail Flow rules) processed an email, look for S:TRA value in Extended Message Trace (EMT).
Advanced Threat Protection (ATP)
After all this checks, the emails are scanned against Advanced Threat Protection (ATP) policies. Microsoft Defender for Office 365 provides extra layer of security by scanning the URLs and attachments within the emails. By default, ATP policies are not available with Exchange Online Protection. To use Advanced Threat Protection (ATP), you need supported subscription.
Note: Microsoft Defender for Office 365 is available with Plan1 and Plan 2. Microsoft Defender for Office 365 Plan 2 is included in Office 365 E5 license, Office 365 A5, Microsoft 365 E5 Security, and Microsoft 365 E5 license. Microsoft Defender for Office 365 plan 1 is included in Microsoft 365 Business Premium subscription.
Office 365 Advanced Threat Protection uses a multi-layered solution to protect mailboxes, files, online storage, and application against a wide range of threats. Advanced Threat Protection (ATP) includes Safe Attachments and Safe links features that protect customers from unknown email threats in real-time by using intelligent systems that inspect attachments and links for malicious contents.
Safe Attachments: Safe Attachments in Office 365 Advanced Threat Protection provides an additional layer of protection for email attachments that have already been scanned by anti-malware protection policies.
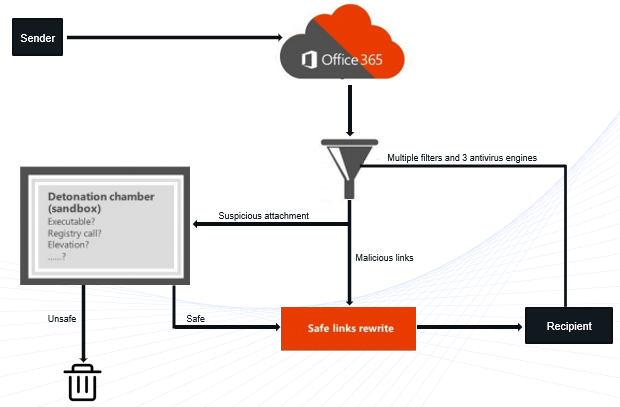
As soon as an email reaches ATP, this email is moved to a virtual environment where attachments are scanned. This virtual environment is called Detonation Chamber or Sandbox. Safe attachments detonates the attachments that are common targets for malicious contents, such as Office documents, PDFs, executable files, and flash files. If an attachment is found unsafe, that attachment is rejected, and if attachment is safe, both the email and the attachments are delivered to the recipient inbox.
When an attachment enters the safe attachment sandbox environment, a detonation chamber analyses the attachment and determines whether this attachment is safe or not. This process takes up to 30 minutes to scan the attachment depending on the file size. With Dynamic Delivery of safe attachments this delay is eliminated by sending the body of the email to the recipient, and the actual attachment undergoes the safe attachments scan. While the attachment is being scanned, the users can read and reply to the email. If attachment is found safe, it is attached with the email in the user’s mailbox, and if the attachment is found unsafe, it is rejected.
Safe Links: Safe Links is a feature of Advanced Threat Protection that provides URL scanning and rewriting of URLs within the emails. Safe Links scanning occurs in addition to the regular anti-spam and anti-malware policies within Exchange Online Protection (EOP).
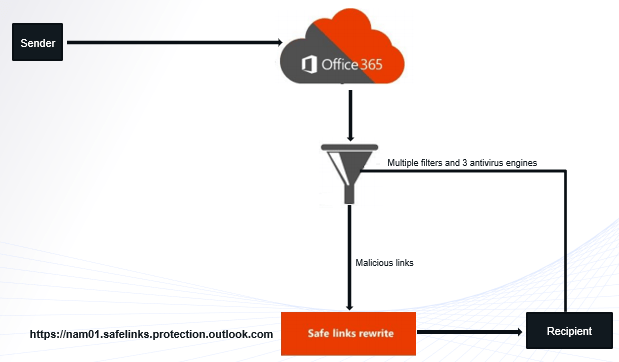
Safe Links scans incoming email for known malicious hyperlinks. Every scanned URLs are rewritten using the Microsoft standard URL prefix. This URL is added as a prefix to the every URL that is found within the emails.
When a user opens an email in his mailbox and clicks on a URL, Safe links immediately check the URL before opening the website. If the URL is included in the Block the following URL list of Safe Links policy, user will see Blocked URL warning page. If the URL points to a website that has been determined to be malicious, a malicious website warning page will open.
Important: If you want to find out if ATP Safe Attachments or Safe Links has processed an email, look for X-MS-Exchange-Organization-SafeAttachmentProcessing and X-MS-Exchange-Organization-SafeLinksProcessing within in the email header.
Anti-Spam (Content Filtering)
After email successfully passes Connection Filter policies, Anti-Malware policies, Transport Rules, and Advanced Threat Protection (ATP) checks, it is scanned by Spam Filter Agent (SFA). Anti-spam policies help protect organizations from receiving SPAM emails. Exchange Online Protection (EOP) uses Spam filtering technologies to identify and separate junk email from legitimate email. If email is an incoming email, this email will be processed by Anti-Spam inbound policies, and if email is an outgoing email, it is processed by Anti-spam outbound policies.
When Spam Filter Agent (SFA) scan an email, it stamps SCL (Spam Confidence Level) values and SPAM Filtering Verdict (SFV) within the email header of that particular email.
Important: If you want to find out if Spam Filter Agent processed an email, analyze Extended Message Trace (EMT) and look for S:SFA value in the Custom Data section.
When spam filter scans any email, it adds an SCL value in the X-Forefront-AntiSpam-Report section of each email header during the filtering process. These SCL values are as shown below:
SCL -1: SCL -1 indicates this email was sent within the organization (internal email). SCL -1 also indicates that the spam filtering was skipped on the email because the sender was added within the allow list of Spam Filter policies or due to a Transport Rule to bypass spam filtering.
SCL 0 to 1: Email is not a spam email (NSPM).
SCL 5 to 6: Spam email.
SCL 9: Indicates email is marked as High Spam (HSPM).
During the email scanning process, Anti-spam filters also add SFV (Spam Filtering Verdict) values. Few of the Spam Filtering Verdicts are shown below:
SFV:NSPM – Not a spam email.
SFV:BLK – The email was blocked because the sender was added within the recipient’s blocked sender list.
SFV:SKA – Filtering was skipped on the email, because the sender was added within the allowed domain list of anti-spam policy.
SFV:SFE – Filtering was skipped and the message was allowed because it was sent from an address in a user’s Safe Senders list.
SFV:SKB – The message was marked as spam because it matched a sender in the blocked senders list or blocked domains list in an anti-spam policy.
SFV:SKQ – The message was released from the quarantine and was sent to the intended recipients.
SFV:SPM – The message was marked as spam by spam filtering.
During the scanning process, Anti-spam filters stamps Phishing Confidence Level (PCL) values in the X-MS-Exchange-Organization-PCL section of the email header, and Bulk Complaint Level (BCL) in the X-Microsoft-Antispam section of the email header. These values are shown below:
Phishing Confidence Level 1 to 3: Email is not a phishing email.
Phishing Confidence Level 4 to 8: Email is marked as Phishing email
Bulk Complaint Level 0: Email is not a bulk email.
Bulk Complaint Level 1,2,3: Moderate bulk email
Bulk Complaint Level 4,5,6,7: Indicates bulk emails that generates a mixed number of complaints.
Bulk Complaint Level 8,9: Indicates email is from a bulk sender that generates high level of complaints.
So once email is processed by Spam Filter Agents (SFA), the action is taken on the emails basis on the spam filter policies configured on the recipient side.
After these values are stamped by Spam Filter Agent, it validates SPF, DKIM, and DMARC on the recipient side, and updates the values within the ARC-Authentication-Results and Authentication-Results sections in the email header.
Finally, if email passes all the above checks, EOP routes it to Exchange Online, and it gets delivered to the Bob’s mailbox. But wait! There is one more check that will run on this email.
Zero-hour Auto Purge (ZAP)
Zero-hour auto purge (ZAP) in Microsoft Defender for Office 365 is a feature designed to help protect your organization against harmful messages that may have already been delivered to users’ mailboxes. ZAP works by automatically removing malicious emails from users’ mailboxes even after they have been delivered. Here’s how ZAP works:
- Detection: Microsoft Defender for Office 365 continuously monitors incoming emails for signs of malicious content, such as phishing attempts, malware, or other types of threats.
- Identification: When a potentially harmful email is identified, Microsoft Defender for Office 365 marks it as malicious and takes action to prevent further harm.
- Removal: Even if a malicious email manages to bypass initial detection and is delivered to a user’s mailbox, ZAP steps in. It periodically reviews delivered emails for newly discovered threats.
- Automatic Purge: If an email is identified as malicious after it has been delivered, ZAP automatically removes it from the user’s mailbox. This helps prevent users from inadvertently interacting with dangerous content.
Important: To identity if ZAP has taken action on the email, look for X-Microsoft-Antispam-ZAP-Message-Info in the email header. This header includes a log string of characters.
When email is sent from Exchange Online to Internet, it is scanned by Anti-Spam outbound policies. During this check, email is scanned against the settings and restrictions configured within Anti-Spam outbound policies.
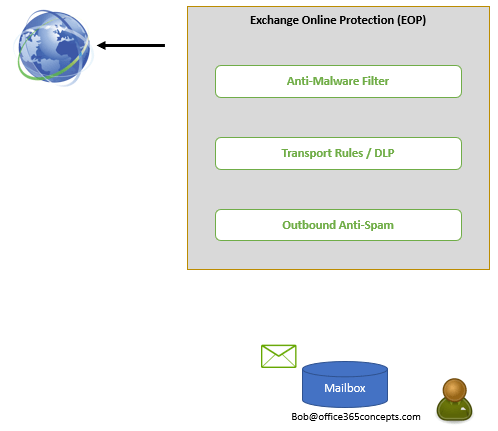
Post this scan, if you have configured Data Loss Prevention (DLP) policies or any other email encryption methods, all these policies are applied on the email. Also, on this level, this email is scanned for the transport rules.
When this email passes above checks, it is scanned by the Anti-Malware engines, and EOP will routes that email to the Internet.
Conclusion
In this blog you learnt how Exchange Online mail flow works, Exchange Online Protection works, how EOP email filters scan emails, and how these filters stamp email headers.
You might like our other article on Bypass ATP Safe Attachments and Safe Links and How to stop Spoof Emails in Office 365.
If you found this article helpful and informative, please share it within your community and do not forget to share your feedback in the comments below. Join us on our YouTube channel for the latest videos on the cloud technology and join our Newsletter for the early access of the blogs and updates.
Happy Learning!!
