What is a Spoof Email and how to stop Spoof email in Office 365
In this blog we will learn what is a spoof email, how to identity a spoof email, what is display name spoofing and domain name spoofing, and how to stop spoof email in Office 365.
Table of Contents
What is a Spoof Email
A spoof email is a deceptive email that appears to be from a legitimate source but is actually sent by someone else with malicious intent. It might mimic the design and content of a real email from a trusted organization or person, aiming to trick recipients into revealing personal information, clicking on harmful links, or downloading malicious attachments. Spoof emails often try to create a sense of urgency or exploit emotions to manipulate people into taking actions that could compromise their security or privacy.
How to identity a spoof email
You can identity a spoof email using the email header analyzer. Please refer to this link to learn how to analyze an email header.
Identifying spoofed emails in the email header requires examining specific information that can reveal inconsistencies or irregularities that indicate potential spoofing. Here’s how to identify spoofed emails by analyzing the email header:
- View the Email Header: Most email clients allow users to view the full email header, which contains detailed information about the email’s origin, routing, and authentication. Check the Return-Path and From Address in the email header. This address is used by the mail server to handle bounce-back messages. If these addresses don’t match, it could indicate spoofing.
- Check SPF, DKIM, and DMARC Authentication Results: Look for entries related to SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) in the email header. These authentication mechanisms help verify the sender’s identity. Check if the SPF, DKIM, and DMARC authentication results indicate a pass or fail status.
Types of email spoofing
There are 2 types of email spoofing that can occur in Office 365/Exchange Online or in any email service. Display Name Spoofing and Domain Name Spoofing.
Display Name Spoofing
Display name spoofing in Office 365 refers to a type of email spoofing where the sender’s display name is manipulated to appear as if it’s from a trusted source, even though the actual email address may be different or entirely unrelated. In this type of spoofing, the attacker crafts an email with a deceptive display name that looks familiar or legitimate to the recipient.
For example, a malicious actor might send an email with a display name such as “Microsoft Support” or “Your IT Administrator,” making it seem like the email is coming from a trusted entity like Microsoft or the recipient’s own IT department. However, upon closer inspection, the actual email address may be from a suspicious or unrelated domain.
Domain Name Spoofing
Domain name spoofing in Office 365 refers to a type of email spoofing where attackers manipulate the domain name in email addresses to make them appear as if they come from a trusted domain associated with Office 365 services. This type of spoofing is a common tactic used by cybercriminals to deceive recipients and increase the likelihood of their phishing emails being successful.
How to stop spoof email in Office 365
There are multiple ways to stop spoof email in Office 365.
Important: Before you follow below steps to stop domain name spoofing or display name spoofing, make sure SPF, DKIM, and DMARC records are updated for your domain. These 3 DNS records help to improve the authenticity of the emails sent from your domains and reduces the chances of legitimate emails from being marked as spam/spoof/phish.
Stop Domain Name spoofing
To stop domain name spoofing in Office 365, administrators can create a mail flow rule (mail transport rule) in Exchange Online.
Go to Exchange Admin Center, click Mail Flow, click Rules, and click Add a rule.
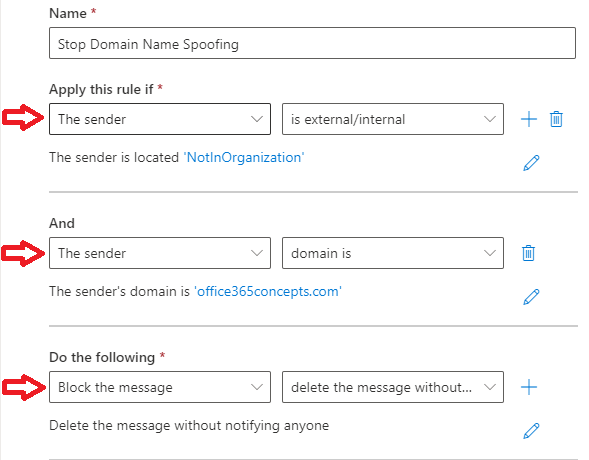
- Give the rule a relevant name, such as Stop Domain Name Spoofing.
- Under Apply this rule if select The sender, and then The sender is internal/external. Select the location to outside the organization.
- Add another condition and choose The sender’s domain is and type your organization’s email domain. You can add multiple domains under this section.
- Choose action of the mail flow rule as per your security requirement. If you would like to automatically delete messages, choose Block the message, and select delete the message without notifying anyone.
- If you have an application or a website that relays emails on your domain’s behalf, you can add the IP address of the application or the website under Except if section. Select Sender’s IP address is in any of these ranges or exactly matches, and add the IP address or the IP address range.
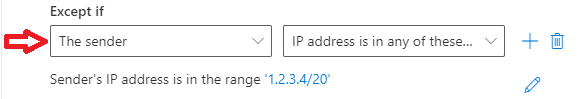
The above mail flow rule will delete emails those are sent to your Microsoft 365 tenant from outside world using your organization’s domains, but it will not take any action on the emails those are sent to your tenant using your domains from the IP addresses mentioned under exception.
Prevent Display Name spoofing Office 365
To prevent display name spoofing in Office 365, administrators can create a mail flow rule (mail transport rule) in Exchange Online.
Go to Exchange Admin Center, click Mail Flow, click Rules, and click Add a rule.
- Give the rule a relevant name, such as Stop Domain Name Spoofing.
- Under Apply this rule if select The sender, and then The sender is internal/external. Select the location to outside the organization.
- Add another condition and select The message headers and then select include any of these words. Type From and type the display name of the users that you want to cover under this transport rule.
- Under Do the following select Block the message and then select delete the message without notifying anyone.
- If you have an application or a website that relays emails on behalf of a user account, you can add the IP address of the application or the website under Except if section. Select Sender’s IP address is in any of these ranges or exactly matches, and add the IP address or the IP address range.

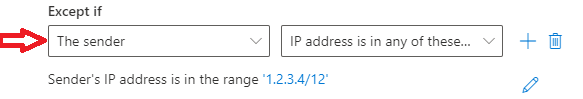
The above mail flow rule will delete emails those are sent to your Microsoft 365 tenant from outside world using your organization’s users display names, but it will not take any action on the emails those are sent to your tenant on behalf of your users from the IP addresses mentioned under exception.
Important: You can also use Impersonation settings anti-phishing policies in Microsoft Defender for Office 365 for user impersonation protection and domain impersonation protection.
Conclusion
In this blog you learnt what is a spoof email, how to identity a spoof email using email header, and how to prevent display name spoofing and domain name spoofing in Office 365.
You might like our other articles on Microsoft Purview Message Encryption and High Risk Delivery Pool (HRDP).
If you found this article helpful and informative, please share it within your community and do not forget to share your feedback in the comments below. Please join us on YouTube for the latest videos on the Cloud technology and join our Newsletter for the early access of the blogs and updates.
Happy Learning!!
