Empowering Your Exchange Server 2010 Journey with Expert Interview Questions and Answers
Unlock the secrets of Exchange Server 2010 with our comprehensive interview questions and answers. Master the key concepts in just a few clicks!
📌📌We have categorized Microsoft Exchange Server 2010 interview questions and answers in different levels as below:
Freshers
Intermediate Level
Experienced
Advanced Level
📌📌 Learn Exchange Server 2019 + Hybrid deployment. A complete free course on our YouTube channel.Top 10 frequently asked Microsoft Exchange Server 2010 interview questions and answers
- What is Microsoft Exchange Server 2010?
- What are the key features of Exchange Server 2010?
- What is a mailbox database in Exchange Server 2010?
- Explain Microsoft Exchange Server 2010 roles?
- What is the purpose of the Client Access Server role?
- How can you configure email address policies in Exchange Server 2010?
- Explain the concept of transport rules in Exchange Server 2010?
- What is the difference between Microsoft Exchange Server 2010 and 2013?
- What is the purpose of the Exchange Management Shell?
- How can you monitor Exchange Server 2010 using the Exchange Management Console?
Microsoft Exchange Server 2010 interview questions and answers for freshers
1. What is Microsoft Exchange Server 2010?
Microsoft Exchange Server 2010 is a messaging and collaboration platform developed by Microsoft. It is a server software that provides email, calendar, contact, and task management capabilities to users within an organization. Exchange Server 2010 enables efficient communication and collaboration, with features such as email routing, mailbox management, mobile device synchronization, and advanced security measures.
2. What are the key features of Exchange Server 2010?
Exchange Server 2010 offers several key features that enhance communication and collaboration within an organization. Some of the prominent features include:
- Email Management: Exchange Server 2010 provides robust email management capabilities, including support for large mailboxes, improved message tracking, and integrated voice mail.
- Calendar and Scheduling: Users can efficiently manage their schedules with features such as shared calendars, resource booking, and meeting management.
- Mobile Device Access: Exchange Server 2010 enables seamless synchronization of emails, calendars, and contacts with mobile devices, allowing users to stay connected on the go.
- Data Protection and Security: The server includes built-in measures to protect sensitive information, including data loss prevention (DLP) policies, message encryption, and anti-spam/anti-malware filters.
- Collaboration Tools: Exchange Server 2010 facilitates collaboration through features like shared contacts, distribution lists, public folders, and team-based communication tools.
- Unified Messaging: It offers voicemail integration with email, allowing users to access and manage their voicemails directly from their inbox.
- High Availability: Exchange Server 2010 provides high availability options, such as database availability groups (DAGs) and database replication, ensuring continuous access to email services.
- Archiving and Compliance: Organizations can meet regulatory and compliance requirements with features like mailbox archiving, legal hold, and retention policies.
3. What is a mailbox database in Exchange Server 2010?
In Exchange Server 2010, a mailbox database is a logical unit that stores all the email messages, calendar items, contacts, tasks, and other mailbox-related data for Exchange users. It is essentially a storage container for individual user mailboxes within the Exchange environment.
A mailbox database holds the actual mailbox data files on disk and is managed by the Exchange Server. Each mailbox database can accommodate multiple user mailboxes, and the data within it is organized in a structured manner for efficient access and retrieval.
Mailbox databases provide a centralized location for storing and managing user mailboxes, enabling features such as email delivery, message tracking, indexing for fast searching, and various administrative tasks. They also play a crucial role in implementing high availability and disaster recovery solutions, as mailbox databases can be replicated across multiple servers for redundancy and fault tolerance.
Administrators have control over mailbox databases, allowing them to create, configure, and manage various aspects such as size limits, backup and recovery settings, retention policies, and database-level security.
4. Explain Microsoft Exchange Server 2010 roles?
In Microsoft Exchange Server 2010, roles refer to distinct server roles or roles-based deployments that serve specific functions within an Exchange organization. These roles are responsible for performing different tasks and services to ensure the smooth operation of the Exchange environment. Exchange Server 2010 has 5 roles:
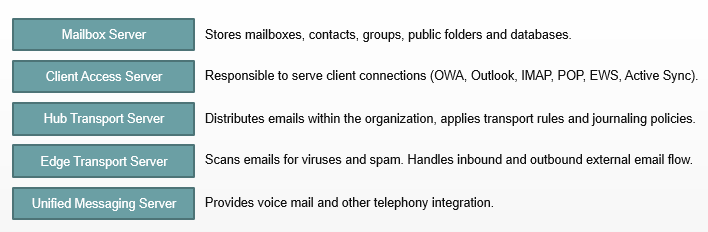
- Mailbox Role: The Mailbox role hosts and manages user mailboxes, public folders, and related services. It stores mailbox data, handles message routing, and provides access to client applications for email retrieval and management.
- Client Access Role: The Client Access role enables client connectivity to Exchange services, including Outlook Web App, Exchange ActiveSync, Outlook Anywhere (formerly known as RPC over HTTP), and Exchange Web Services. It handles client requests and provides the necessary protocols and services for client access.
- Hub Transport Role: The Hub Transport role facilitates email flow within the Exchange organization. It routes messages between mailboxes and handles message delivery, transport rules, message categorization, and content inspection. The Hub Transport role is responsible for enforcing email policies and applying transport-related settings.
- Edge Transport Role: The Edge Transport role is optional and is typically deployed in the perimeter network or as a separate server outside the organization’s internal network. It provides enhanced security and protection against spam, viruses, and other external threats. The Edge Transport role handles message filtering, anti-spam measures, and inbound/outbound message routing.
- Unified Messaging Role: The Unified Messaging role integrates voice messaging with Exchange Server. It enables features such as voicemail, auto-attendant, and speech recognition. The Unified Messaging role allows users to access and manage their email, voice messages, and faxes through various clients or devices.
5. What is the purpose of the Client Access Server role?
The Client Access Server (CAS) role in Microsoft Exchange Server is responsible for handling client connections and facilitating client access to Exchange services. The CAS role acts as a front-end server, serving as the entry point for various client applications and protocols. Its main purpose is to provide connectivity and access to Exchange services for users, regardless of their location or device.
The key functions of the Client Access Server role include:
- Client Connectivity: The CAS role allows clients to connect to Exchange services, including Outlook, Outlook Web App (OWA), Exchange ActiveSync, Exchange Web Services (EWS), and POP/IMAP protocols. It provides the necessary endpoints and services for clients to establish connections and interact with their mailboxes.
- Authentication and Authorization: The CAS role performs authentication and authorization processes to verify user identities and grant access to their mailboxes. It enforces security measures, such as SSL encryption, and supports various authentication methods, including username/password, smart card, and certificate-based authentication.
- Client Protocol Support: The CAS role supports a wide range of client protocols, enabling users to access their mailboxes from different devices and platforms. It handles protocol-specific requests and ensures compatibility and functionality across various clients, such as Outlook for Windows, Outlook for Mac, mobile devices, and web browsers.
- Proxying and Redirection: In a multi-server or multi-site Exchange environment, the CAS role can proxy client requests to the appropriate backend server or redirect clients to access their mailboxes hosted on other servers. This helps distribute the load, optimize performance, and ensure efficient mailbox access for users.
- Web-based Access: The CAS role hosts Outlook Web App (OWA), which allows users to access their mailboxes through web browsers. It provides a web-based interface for email, calendar, contacts, and other Exchange features, offering a similar experience to using Outlook desktop client.
6. How can you configure email address policies in Exchange Server 2010?
To configure email address policies in Exchange Server 2010, you can follow these steps:
- Launch the Exchange Management Console (EMC) on the Exchange Server.
- Navigate to the “Organization Configuration” node and select “Hub Transport.”
- In the “Hub Transport” pane, click on the “Email Address Policies” tab.
- Right-click on “Email Address Policies” and choose “New Email Address Policy” from the context menu.
- Provide a name for the new email address policy and click “Next.”
- On the “Conditions” page, you can define conditions to target specific recipients or recipient types. For example, you can specify criteria based on organizational units (OU), recipient types, or custom attributes. Configure the conditions as desired and click “Next.”
- On the “Email Addresses” page, you can add and modify the email address formats for the selected recipients. Click “Add” to add a new email address format.
- In the “New E-mail Address” dialog box, select the email address type (e.g., SMTP, X.400) and specify the email address format using variables and attributes. You can use variables such as %g (given name), %s (surname), and %d (department). Customize the email address format according to your requirements and click “OK.”
- If desired, you can add additional email address formats by clicking “Add” again and repeating the previous step. You can set the priority of email address formats using the arrows.
- Once you have added all the required email address formats, click “Next” to proceed.
- On the “Schedule” page, you can specify when the email address policy should be applied. You can choose to apply it immediately or set a custom schedule. Make the appropriate selection and click “Next.”
- Review the summary of the new email address policy settings and click “New” to create the policy.
The new email address policy will be created and applied to the specified recipients based on the defined conditions. You can verify and manage the email address policies in the “Email Address Policies” tab of the Exchange Management Console.
7. Explain the concept of transport rules in Exchange Server 2010?
Transport rules in Exchange Server 2010 are a set of policies that allow administrators to control and manipulate email messages as they pass through the Exchange transport pipeline. These rules provide a flexible mechanism to enforce organizational policies, apply actions, and apply conditions based on specific criteria.
The concept of transport rules revolves around three key components: conditions, actions, and exceptions.
- Conditions: Conditions define the criteria that must be met for a transport rule to be applied to a particular message. These conditions can be based on various attributes such as sender, recipient, message content, message size, attachment properties, and more. Administrators can create rules to target specific types of messages or specific senders/recipients.
- Actions: Actions define the actions to be taken when a message matches the specified conditions. Exchange Server 2010 provides a wide range of actions that can be applied, including adding a disclaimer, forwarding the message to another recipient, redirecting the message, deleting the message, modifying message properties, or applying message classification. These actions allow administrators to enforce policies, implement routing rules, or add custom metadata to messages.
- Exceptions: Exceptions allow administrators to define conditions under which a transport rule should not be applied, even if the message meets the specified conditions. Exceptions help to exclude specific scenarios or recipients from the rule’s actions.
By defining transport rules, administrators can automate various processes, enforce compliance policies, implement security measures, and streamline email management within the organization. For example, a transport rule can be created to add a standardized email disclaimer to all outgoing messages, redirect specific messages to a designated mailbox for review, block messages with certain sensitive information, or enforce encryption for specific recipients.
Transport rules in Exchange Server 2010 can be managed using the Exchange Management Console (EMC) or the Exchange Management Shell (EMS). Administrators can create, modify, enable, disable, and prioritize transport rules to achieve the desired email handling and policy enforcement within the Exchange environment.
8. What is the difference between Microsoft Exchange Server 2010 and 2013?
Microsoft Exchange Server 2010 and 2013 are two different versions of the Exchange Server platform, each introducing various enhancements and new features. Here are some key differences between Exchange Server 2010 and 2013:
- Architecture: Exchange Server 2010 follows a traditional server role architecture, where each role is installed on a separate server. In contrast, Exchange Server 2013 introduces a simplified architecture called the “Exchange Server 2013 Managed Availability” model, which consolidates multiple roles onto fewer servers for improved manageability and resiliency.
- Database Availability Groups (DAGs): Exchange Server 2010 uses database-level replication known as Database Availability Groups (DAGs) for high availability. In Exchange Server 2013, DAGs are further enhanced with the introduction of Managed Availability, which automates monitoring and recovery processes for improved availability.
- Outlook Web App (OWA): Exchange Server 2013 introduces a redesigned and more feature-rich version of Outlook Web App, offering a modern and responsive web-based interface for accessing mail, calendar, and other Exchange features. The OWA in Exchange 2013 provides a more seamless experience across different devices.
- Data Loss Prevention (DLP): Exchange Server 2013 includes built-in Data Loss Prevention (DLP) capabilities, allowing organizations to create and enforce policies to prevent sensitive information from being shared or leaked via email. Exchange 2010 does not have native DLP functionality.
- Exchange Administration Center (EAC): Exchange Server 2013 introduces a new web-based administration interface called the Exchange Administration Center (EAC). It provides a unified and intuitive interface for managing Exchange features, replacing the Exchange Management Console (EMC) used in Exchange Server 2010.
- Public Folders: In Exchange Server 2013, public folders are completely re-architected, leveraging the mailbox database infrastructure for improved scalability and performance. Exchange Server 2010 uses a separate public folder database.
- Integration with Office 365: Exchange Server 2013 offers improved integration and coexistence capabilities with Office 365, Microsoft’s cloud-based productivity suite. This enables organizations to have a hybrid deployment, combining on-premises Exchange with Office 365 services.
These are just a few of the key differences between Microsoft Exchange Server 2010 and 2013. Each version introduces additional enhancements, performance improvements, and security features, catering to the evolving needs of organizations for email communication, collaboration, and management.
9. What is the purpose of the Exchange Management Shell?
The Exchange Management Shell is a command-line management interface in Microsoft Exchange Server that provides administrators with powerful tools for managing and configuring Exchange server environments. It is built on Windows PowerShell, a scripting and automation framework.
The purpose of the Exchange Management Shell is to enable administrators to perform various administrative tasks efficiently and programmatically, using a command-line interface. Some key purposes and capabilities of the Exchange Management Shell include:
- Administrative Control: The Exchange Management Shell allows administrators to have granular control over Exchange server configuration, settings, and objects. It provides access to a vast array of cmdlets (commands) specifically designed for Exchange Server management.
- Automation and Scripting: With the Exchange Management Shell, administrators can automate repetitive or complex administrative tasks by creating scripts or batch files. PowerShell scripting capabilities allow for the automation of various tasks, such as user provisioning, mailbox management, message tracking, and more.
- Configuration and Monitoring: The Exchange Management Shell enables administrators to configure and monitor various aspects of the Exchange environment, including mailboxes, databases, transport rules, connectors, address lists, and more. It provides the flexibility to modify settings quickly and efficiently, ensuring optimal performance and adherence to organizational policies.
- Exchange Organization Management: The Exchange Management Shell allows administrators to manage Exchange organizations, including creating and managing recipient objects (users, mailboxes, distribution groups), managing permissions, configuring mailbox policies, and implementing messaging and transport rules.
- Troubleshooting and Diagnostics: The Exchange Management Shell provides access to diagnostic and troubleshooting cmdlets that assist in identifying and resolving issues within the Exchange environment. Administrators can perform tasks such as message tracking, mailbox and database health checks, and viewing and analyzing server logs.
10. How can you monitor Exchange Server 2010 using the Exchange Management Console?
Monitoring Exchange Server 2010 using the Exchange Management Console (EMC) involves utilizing the built-in monitoring features and tools available within the console. Here are the steps to monitor Exchange Server 2010 using the EMC:
- Launch the Exchange Management Console on the Exchange Server.
- In the console tree, navigate to the “Organization Configuration” node and select “Mailbox.”
- In the “Work pane,” click on the “Database Management” tab.
- Here, you will find a list of mailbox databases in your Exchange organization. Select the mailbox database that you want to monitor.
- Right-click on the selected mailbox database and choose the “Properties” option from the context menu.
- In the database properties window, go to the “Maintenance” tab.
- On the “Maintenance” tab, you will find various options for monitoring the mailbox database. These options include:
- Background database maintenance: This option allows you to configure the schedule and settings for background database maintenance tasks, such as online database defragmentation, checksumming, and page repair.
- Database backup and restore: You can configure and monitor the database backup and restore operations for the selected mailbox database. This includes specifying the backup location, scheduling backups, and monitoring the status of backup and restore operations.
- Circular Logging: Circular logging is a feature that helps manage transaction log files. You can enable or disable circular logging for the selected mailbox database.
- Maintenance schedule: You can set a schedule for maintenance tasks, such as online database defragmentation and online maintenance.
- Configure the desired monitoring settings and schedules based on your requirements.
- Click “OK” to save the changes.
By monitoring the mailbox database through the EMC, you can keep track of maintenance activities, backup and restore operations, and overall database health. The EMC provides a convenient graphical interface for managing and monitoring these aspects of Exchange Server 2010. Additionally, you can also utilize other monitoring tools, such as Performance Monitor (Perfmon) and Exchange Management Shell cmdlets, for more in-depth monitoring and troubleshooting.
Microsoft Exchange Server 2010 interview questions and answers for intermediate level
11. How to configure outlook with exchange server 2010?
To configure Microsoft Outlook with Exchange Server 2010, you can follow these steps:
- Open Microsoft Outlook on the client machine.
- When prompted, select “Yes” to configure an email account, or you can go to the “File” tab and click on “Add Account.”
- In the “Add Account” window, select the option to manually configure server settings or additional server types, and click “Next.”
- Choose the “Microsoft Exchange or compatible service” option, and click “Next.”
- In the “Microsoft Exchange Settings” window, provide the following information:
- Server: Enter the name of your Exchange Server. This can be the fully qualified domain name (FQDN) or the IP address of the server.
- User Name: Enter the user’s name or email address.
- More Settings: Click on this button to open the “Microsoft Exchange” window.
- In the “Microsoft Exchange” window, go to the “Connection” tab.
- Check the box that says “Connect to Microsoft Exchange using HTTP.”
- Click on the “Exchange Proxy Settings” button.
- In the “Exchange Proxy Settings” window, provide the following information:
- Proxy Server: Enter the FQDN or IP address of your Exchange Server.
- Check the box that says “Connect using SSL only.”
- Under the “Proxy authentication settings” section, select the appropriate authentication method (usually “Basic Authentication”).
- Click “OK” to close the “Exchange Proxy Settings” window.
- Back in the “Microsoft Exchange Settings” window, click “Next.”
- Outlook will now attempt to establish a connection with the Exchange Server and verify your account settings. If everything is configured correctly, you will see a “Congratulations!” message.
- Click “Finish” to complete the configuration process.
Outlook will now be configured to connect to your Exchange Server 2010. It will start synchronizing your mailbox, and you will be able to send and receive emails, access calendars, contacts, and other Exchange features through Outlook.
12. How does Exchange Server 2010 handle high availability and site resilience?
Exchange Server 2010 provides various features and mechanisms to achieve high availability (HA) and site resilience, ensuring that email services remain accessible and operational even in the event of server or site failures. Here are some key aspects of how Exchange Server 2010 handles high availability and site resilience:
- Database Availability Groups (DAGs): DAGs are a core component of Exchange Server 2010’s high availability architecture. DAGs allow multiple Exchange servers to host copies of mailbox databases, providing automatic database-level replication and failover. Each database copy within a DAG is continuously synchronized with the other copies, allowing for seamless failover and mailbox access in the event of a server or database failure.
- Continuous Replication: Exchange Server 2010 uses continuous replication technology to maintain multiple copies of mailbox databases within a DAG. There are two types of continuous replication:
- Database Availability Group (DAG) Replication: This is the built-in replication mechanism within DAGs. It ensures that mailbox database copies are synchronized and updated across multiple servers within the DAG.
- Log Shipping: Exchange Server 2010 also uses log shipping to replicate transaction logs between mailbox database copies. Transaction logs are continuously shipped to other database copies to maintain data consistency.
- Automatic Failover: In the event of a server or database failure, Exchange Server 2010 automatically triggers a failover process within the DAG. The active mailbox database copy is switched to another server, and client connections are redirected to the new server, allowing users to continue accessing their mailboxes with minimal downtime or interruption.
- Database Reseeding: If a mailbox database copy becomes corrupt or outdated, Exchange Server 2010 supports database reseeding. This process involves re-copying the database from a healthy copy to restore data integrity and bring the copy up to date.
- Database Mobility: Exchange Server 2010 allows for seamless database mobility, enabling administrators to move mailbox database copies between servers within a DAG. This flexibility provides the ability to perform maintenance tasks, load balancing, or site resilience operations without disrupting user access to mailboxes.
- Datacenter Activation Coordination (DAC) Mode: DAC Mode is a feature introduced in Exchange Server 2010 to prevent split-brain scenarios during datacenter failovers. It ensures that only a single datacenter is active at a time to avoid conflicts and inconsistencies.
- Site Resilience and Datacenter Failover: Exchange Server 2010 allows organizations to achieve site resilience by deploying multiple DAGs across different physical locations or datacenters. This enables the automatic failover of mailbox databases and client access to a secondary site in the event of a datacenter or site failure.
13. What is a DAG (Database Availability Group) in Exchange Server 2010?
In Exchange Server 2010, a DAG stands for Database Availability Group. It is a high-availability and resilience feature introduced by Microsoft to enhance the availability and reliability of mailbox databases. A DAG is a group of up to 16 Exchange Mailbox servers that work together to provide automatic database-level recovery from failures.
The primary purpose of a DAG is to ensure that mailbox databases are continuously accessible to clients, even in the event of server or database failures. It achieves this by creating database copies and synchronizing them across multiple servers within the DAG. Each database copy is stored on a separate server known as a database server.
Here are some key points about DAG in Exchange Server 2010:
- High Availability: A DAG provides automatic database-level failover in case of a server or database failure. If one server hosting a database becomes unavailable, the active mailbox database copy automatically switches over to another server in the DAG, minimizing downtime.
- Database Replication: Database copies within a DAG are continuously replicated using a technology called Continuous Replication. It synchronizes the transaction log files between database copies to keep them up to date.
- Load Balancing: DAG provides load balancing capabilities by distributing the active mailbox database copies across multiple servers. This helps in optimizing resource utilization and ensuring efficient client connectivity.
- Automatic Database Activation: If a server fails or a database copy becomes unavailable, Exchange Server 2010 automatically activates a passive copy of the database on another server, making it the active copy accessible to clients.
- Data Protection: DAG provides built-in data protection by maintaining multiple copies of mailbox databases. This protects against hardware failures, disk corruptions, and other unexpected issues that can impact the availability of the mailbox data.
By implementing a DAG in Exchange Server 2010, organizations can significantly improve the availability and reliability of their email infrastructure, ensuring continuous access to mailbox databases for users.
14. Explain the process of upgrading from a previous version of Exchange to Exchange Server 2010?
The process of upgrading from a previous version of Exchange to Exchange Server 2010 involves several steps. Here’s a general outline of the process:
- Review System Requirements: Before upgrading, ensure that your environment meets the system requirements for Exchange Server 2010, including hardware, operating system, and software prerequisites. Review Microsoft’s documentation for the specific requirements.
- Plan the Upgrade: Create a comprehensive upgrade plan that includes a timeline, backup strategy, and considerations for coexistence with the existing Exchange environment during the upgrade process. Determine the appropriate migration strategy based on your current Exchange version and environment.
- Prepare the Environment: Prepare the existing Exchange environment by ensuring that it is up to date with the latest service packs and updates. This may involve applying any required updates or hotfixes to the existing Exchange servers.
- Install Exchange Server 2010: Begin the installation of Exchange Server 2010 on new servers that meet the hardware and software requirements. Follow the recommended installation steps provided by Microsoft, which typically involve running the setup program, configuring server roles, and selecting appropriate options.
- Configure Coexistence: Set up coexistence between Exchange Server 2010 and the existing Exchange environment. This involves configuring connectors, certificates, and other necessary settings to enable communication between the two environments.
- Migrate Mailboxes: Move user mailboxes from the previous Exchange version to Exchange Server 2010. This can be done using various migration methods, such as mailbox moves within the Exchange organization, PST exports/imports, or third-party migration tools. Ensure proper testing and validation of mailbox migrations before proceeding.
- Redirect Services and Client Access: Update DNS records, firewall configurations, and load balancer settings to direct incoming client connections to the new Exchange Server 2010 infrastructure. Update any necessary email client settings, such as Outlook profiles, to connect to the new server.
- Decommission Previous Exchange Servers: Once all mailboxes and services have been successfully migrated to Exchange Server 2010 and thoroughly tested, decommission the previous Exchange servers following the recommended procedures. This may involve removing server roles, uninstalling Exchange software, and performing any required cleanup tasks.
- Test and Monitor: After the upgrade, thoroughly test the functionality of Exchange Server 2010 to ensure all services, features, and client connectivity are working as expected. Implement proper monitoring and maintenance processes to ensure the ongoing health and performance of the new Exchange environment.
15. How can you configure message tracking in Exchange Server 2010?
To configure message tracking in Exchange Server 2010, follow these steps:
- Open the Exchange Management Console (EMC).
- Navigate to the “Organization Configuration” section.
- Click on “Hub Transport” to manage the hub transport settings.
- In the “Actions” pane, click on “Enable Message Tracking…”.
- The “Message Tracking Properties” window will appear. In the “General” tab, specify the following settings:
- Log path: Choose the folder where message tracking logs will be stored. It is recommended to use a dedicated disk or partition with sufficient storage.
- Maximum log age (days): Set the number of days after which the message tracking logs will be deleted automatically.
- Maximum log directory size (MB): Specify the maximum size for the message tracking log directory. When this size is reached, the oldest logs will be deleted to make room for new ones.
- Maximum log file size (KB): Set the maximum size for each individual message tracking log file. If a file reaches this size, a new file will be created.
- In the “Summary” section, review the configuration settings and click on “New” to save the changes.
- The process of enabling message tracking will take a few moments to complete.
Once message tracking is enabled, Exchange Server 2010 will start generating logs for all message activity in your organization. These logs can be used to track message flow, troubleshoot delivery issues, and analyze email traffic patterns.
To search and analyze message tracking logs, you can use the Get-MessageTrackingLog cmdlet in the Exchange Management Shell (EMS). This cmdlet allows you to specify various parameters, such as sender, recipient, subject, time range, and event types, to filter and retrieve specific message tracking information.
Note: Message tracking logs can consume a significant amount of disk space over time, so it’s important to regularly monitor and manage log retention and disk usage to prevent log files from filling up the disk.
16. What are the different types of mailboxes supported by Exchange Server 2010?
Exchange Server 2010 supports several types of mailboxes, each designed to serve different purposes. Here are the different types of mailboxes supported by Exchange Server 2010:
- User Mailbox: A user mailbox is the most common type and is associated with an individual user in an organization. It contains email messages, calendar items, contacts, tasks, and other personal data.
- Room Mailbox: A room mailbox represents a meeting location or a physical resource, such as a conference room or a projector. It allows users to book the room for meetings and manages scheduling conflicts.
- Equipment Mailbox: An equipment mailbox represents a non-human resource, such as a company car or a portable projector. It enables users to reserve and manage the availability of equipment for specific events or activities.
- Linked Mailbox: A linked mailbox is associated with a user in a separate Active Directory forest. It allows users in different forests to access their mailboxes while keeping the Exchange organizations separate.
- Archive Mailbox: An archive mailbox is an additional mailbox that provides users with extra storage for older or less frequently accessed email. It helps in managing mailbox sizes and optimizing server performance.
- Public Folder Mailbox: A public folder mailbox stores public folders in Exchange Server 2010. Public folders are used to share information, such as calendars, contacts, and documents, among multiple users.
- Discovery Mailbox: A discovery mailbox is used for performing eDiscovery searches in Exchange Server. It stores search results and allows authorized users to access and export the discovered data.
17. How can you perform mailbox moves in Exchange Server 2010?
In Exchange Server 2010, you can perform mailbox moves using the Exchange Management Console (EMC) or the Exchange Management Shell (EMS). Here’s how you can perform mailbox moves using both methods:
Using the Exchange Management Console (EMC):
- Open the Exchange Management Console on the server running Exchange Server 2010.
- Navigate to the “Recipient Configuration” section.
- Expand the “Mailbox” node and select the mailbox you want to move.
- In the “Actions” pane, click on “New Local Move Request”. The “New Local Move Request” wizard will open.
- On the “Introduction” page, review the information and click “Next”.
- Select the target mailbox database or specify a mailbox database on a different server, and click “Next”.
- Configure the move settings:
- Specify the move request name.
- Choose the “Suspend the move request if the source mailbox is locked” option if desired.
- Select the “Automatically complete the move request” option to have the move automatically completed or choose to manually complete the move request later.
- Review the move configuration summary and click “New” to start the mailbox move process.
Using the Exchange Management Shell (EMS):
- Open the Exchange Management Shell on the server running Exchange Server 2010.
- Use the following command to start a mailbox move request:
New-MoveRequest -Identity <MailboxIdentity> -TargetDatabase <TargetDatabase>Replace<MailboxIdentity>with the identity of the mailbox you want to move (e.g., user’s email address or username), and<TargetDatabase>with the name of the target mailbox database. - Depending on your requirements, you can add additional parameters to the command, such as
-BadItemLimit,-AcceptLargeDataLoss, or-SuspendWhenReadyToComplete, to customize the move request behavior. - Press Enter to execute the command and initiate the mailbox move.
Once the mailbox move request is initiated, Exchange Server 2010 will begin moving the mailbox from the source database to the target database. The progress of the move can be monitored using the EMC or EMS, and you can view detailed status information, completion percentages, and any errors encountered during the move process.
18. Explain the process of configuring Outlook Anywhere in Exchange Server 2010.
To configure Outlook Anywhere in Exchange Server 2010, follow these steps:
- Ensure that Exchange Server 2010 is installed and properly configured, including the Client Access Server (CAS) role.
- Open the Exchange Management Console (EMC) on the server running Exchange Server 2010.
- Navigate to the “Server Configuration” section.
- Select the Client Access Server (CAS) where you want to configure Outlook Anywhere.
- In the “Actions” pane, click on “Enable Outlook Anywhere”. The “Enable Outlook Anywhere” wizard will open.
- On the “Introduction” page, review the information and click “Next”.
- Specify the external host name to be used for Outlook Anywhere. This should be the publicly accessible FQDN (Fully Qualified Domain Name) that clients will use to connect to Exchange externally.
- Choose the authentication method for Outlook Anywhere. You can select one of the following options:
- Basic Authentication: Provides secure authentication over HTTPS, but requires clients to enter their credentials each time they connect.
- NTLM Authentication: Allows seamless authentication using the user’s Windows credentials, eliminating the need to enter credentials repeatedly.
- Specify the Client Authentication Method. You can select one of the following options:
- Basic Authentication: Allows clients to use basic authentication to connect to Exchange.
- Digest Authentication: Provides a more secure option by hashing the user’s credentials.
- Choose whether to use SSL offloading, which allows SSL encryption and decryption to be performed at a load balancer instead of the Client Access Server.
- Review the configuration summary and click “Enable” to apply the changes.
- After the configuration is completed, you may need to configure firewall rules and port forwarding to allow external access to the Outlook Anywhere service. Ensure that TCP port 443 (HTTPS) is open and directed to the Client Access Server.
Once Outlook Anywhere is configured, clients can connect to Exchange Server 2010 using Microsoft Outlook from outside the organization’s network. They can use Outlook as if they were connected directly to the internal network, benefiting from features such as email, calendar, contacts, and tasks.
It’s important to ensure that the external host name is correctly resolved to the public IP address of the Client Access Server and that appropriate SSL certificates are installed to secure the communication between Outlook clients and the Exchange Server.
19. What is the purpose of the Edge Transport server role in Exchange Server 2010?
The Edge Transport server role in Exchange Server 2010 serves as the first line of defense for an organization’s messaging environment. Its primary purpose is to provide secure and efficient mail flow between the organization’s internal network and the external Internet.
Here are the main purposes and functionalities of the Edge Transport server role:
- Message Filtering: The Edge Transport server performs various message filtering tasks to protect the organization from spam, malware, and other email-based threats. It applies anti-spam agents, content filtering, and attachment filtering to identify and block unsolicited and malicious messages before they reach the internal network.
- Connection Filtering: The Edge Transport server examines incoming connections from external sources and applies connection filtering to block or allow connections based on IP addresses, IP reputation, or other specified criteria. This helps in reducing the impact of spam and malicious traffic on the organization’s network.
- Sender and Recipient Filtering: The Edge Transport server allows administrators to define sender and recipient filtering rules to control email delivery based on specific criteria. This can include blocking or allowing specific senders or recipients, blocking certain domains, or applying restrictions on message size or content.
- Message Hygiene: The Edge Transport server role contributes to maintaining message hygiene by performing tasks such as virus scanning, attachment blocking, and content filtering. It helps prevent the distribution of infected or harmful content within the organization.
- Secure Mail Flow: The Edge Transport server establishes secure mail flow between the internal Exchange organization and external entities.
20. How can you configure public folders in Exchange Server 2010?
To configure public folders in Exchange Server 2010, you can follow these steps:
- Open the Exchange Management Console (EMC) on the server running Exchange Server 2010.
- Navigate to the “Organization Configuration” section.
- Select the “Mailbox” node.
- In the “Actions” pane, click on “New Public Folder Database”. The “New Public Folder Database” wizard will open.
- On the “Introduction” page, review the information and click “Next”.
- Specify a name for the public folder database and choose a server where the database will be hosted. You can also specify a custom path for the database and log files if desired.
- Configure the public folder database settings, such as the log file prefix, log file size, and mounting behavior.
- Review the configuration summary and click “New” to create the public folder database.
- Once the public folder database is created, you can create public folders and manage their properties. To do this, navigate to the “Toolbox” section in the EMC and click on “Public Folder Management Console”.
- In the Public Folder Management Console, you can perform various tasks related to public folders, such as creating new folders, setting permissions, configuring replication settings, and managing folder content.
- To create a new public folder, right-click on the “Default Public Folders” node and choose “New Public Folder”. Specify a name and other properties for the folder and click “OK”.
- To set permissions on a public folder, select the folder in the Public Folder Management Console, right-click, and choose “Manage Settings”. In the “Permissions” tab, you can add users or groups and assign appropriate access rights to the folder.
- To configure replication for a public folder, select the folder in the Public Folder Management Console, right-click, and choose “Manage Settings”. In the “Replication” tab, you can add replica servers and specify replication settings to ensure data consistency across multiple servers.
21. What are the best practices for securing Exchange Server 2010?
Securing Exchange Server 2010 is crucial to protect your organization’s email infrastructure and sensitive data. Here are some best practices to enhance the security of Exchange Server 2010:
- Keep Exchange Server Updated: Regularly apply the latest updates, security patches, and service packs provided by Microsoft to address any known vulnerabilities and ensure the server is up to date.
- Secure Physical Access: Limit physical access to Exchange Server hardware by placing it in a secured location with restricted access. Implement safeguards to protect against unauthorized physical tampering.
- Use Secure Network Connections: Ensure that Exchange Server is deployed in a trusted network environment with appropriate firewalls, network segmentation, and secure network protocols (such as TLS/SSL) for client connections and communication between Exchange servers.
- Implement Role-Based Access Control (RBAC): Use RBAC to assign specific administrative roles and permissions to Exchange Server administrators. Grant administrative privileges only to authorized personnel based on their job responsibilities.
- Harden Operating System and Applications: Follow security best practices to harden the underlying operating system (e.g., Windows Server) and any additional applications installed on the Exchange Server. Disable unnecessary services, apply security configurations, and regularly review and update security settings.
- Protect Authentication: Enforce strong password policies for user accounts, encourage the use of multi-factor authentication (MFA) for accessing Exchange Server, and implement account lockout policies to mitigate brute-force attacks.
- Enable Anti-Malware Protection: Install and configure anti-malware software on the Exchange Server to scan inbound and outbound email for viruses, malware, and other malicious content.
- Implement Message Encryption: Use Transport Layer Security (TLS) or other encryption methods to secure communication channels between Exchange servers and external email systems. Consider implementing email encryption solutions for sensitive or confidential email communications.
- Enable Auditing and Monitoring: Enable auditing features in Exchange Server to track and log critical events, user activity, and changes to configurations.
Interview questions on Exchange Server 2010 for experienced
22. How can you troubleshoot performance issues in Exchange Server 2010?
When troubleshooting performance issues in Exchange Server 2010, there are several steps you can take to identify and resolve the problems. Here’s a general troubleshooting approach:
- Identify the symptoms: Start by gathering information about the performance issues. This includes understanding the specific symptoms reported by users or system monitoring tools. Common symptoms may include slow email delivery, delays in accessing mailboxes, high CPU or memory usage, or disk latency.
- Review system resources: Check the overall health of your Exchange Server by monitoring system resources such as CPU, memory, disk usage, and network bandwidth. Use performance monitoring tools like Performance Monitor (PerfMon) or third-party solutions to gather data and identify any resource bottlenecks.
- Analyze Exchange Server logs: Review the Exchange Server event logs for any error messages or warnings related to performance. Look for specific events that indicate problems or provide clues about the underlying issues.
- Measure database performance: Check the performance of Exchange Server databases by using the Exchange Management Console (EMC) or Exchange Management Shell (EMS). Analyze metrics like RPC latency, I/O latency, and database cache usage. Identify any databases experiencing high latency or excessive I/O operations.
- Review hardware and infrastructure: Evaluate the hardware and infrastructure supporting your Exchange Server. Ensure that the server hardware meets the recommended specifications for Exchange Server 2010. Check network connectivity, switches, routers, and firewalls for any configuration or performance issues.
- Verify antivirus and backup solutions: Antivirus and backup software can sometimes interfere with Exchange Server performance. Ensure that the antivirus software is Exchange-aware and configured correctly to exclude Exchange-specific directories and processes. Similarly, check the backup solution to ensure it’s not causing excessive resource usage during backups.
- Check for rogue processes or mailboxes: Identify any rogue processes or mailboxes that may be causing performance issues. Look for processes consuming excessive CPU or memory resources. Investigate large mailboxes or mailbox databases that may be impacting performance.
- Apply Exchange Server updates and patches: Ensure that Exchange Server 2010 is up to date with the latest service packs, cumulative updates, and patches. Microsoft regularly releases updates to address performance issues and improve the overall stability of Exchange Server.
- Optimize Exchange Server settings: Review and fine-tune Exchange Server settings to improve performance. This includes adjusting the throttling policy, optimizing the database maintenance schedule, configuring mailbox quotas, and adjusting ActiveSync or Outlook Web App settings as per your organization’s requirements.
- Consult Microsoft resources and community: If you encounter complex or persistent performance issues, consult official Microsoft documentation, knowledge base articles, and community forums for Exchange Server. Microsoft provides detailed guidance and troubleshooting steps for various performance-related scenarios.
23. Explain the architecture of Exchange Server 2010?
Exchange Server 2010 has a multi-tier architecture that consists of several components working together to provide email communication and collaboration services. Here’s an overview of the key components and their roles:
- Client Access Server (CAS): The CAS role provides client access to Exchange Server. It handles client protocols such as Outlook Web App (OWA), Exchange ActiveSync, Outlook Anywhere (RPC over HTTP), and POP/IMAP. CAS servers accept client connections, authenticate users, and proxy requests to other Exchange components.
- Hub Transport Server: The Hub Transport role is responsible for message routing within the Exchange organization. It receives incoming messages from the Internet or other mail servers, performs message categorization and content inspection, and then routes the messages to the appropriate mailbox server or external destination.
- Mailbox Server: The Mailbox role hosts mailbox databases and handles all mailbox-related operations. It stores email messages, calendar items, contacts, and other mailbox data. The mailbox server also provides services such as unified messaging, public folders, and mailbox access via Outlook clients or other protocols.
- Edge Transport Server: The Edge Transport role is optional and is typically deployed in the perimeter network to provide enhanced security and message hygiene. It acts as a secure gateway for incoming and outgoing email traffic, applying anti-spam filtering, antivirus scanning, and other transport rules.
- Unified Messaging Server: The Unified Messaging (UM) role integrates voice messaging and telephony features into Exchange Server. It enables users to access their email, voice messages, and faxes from a single inbox. UM servers handle tasks like call answering, auto-attendant, and voice message storage.
- Active Directory: Exchange Server 2010 relies on Active Directory (AD) for user authentication, configuration information, and directory services. Exchange servers interact with AD to retrieve user and mailbox information, authenticate users, and store configuration data.
- Database Availability Group (DAG): DAG is a high-availability feature in Exchange Server 2010 that provides database-level replication and failover. Multiple mailbox servers can be configured in a DAG, allowing for automatic database failover and continuous mailbox availability in case of server or database failures.
These components work together to enable email communication and collaboration in an Exchange Server 2010 environment. The CAS handles client connectivity, the Hub Transport routes messages, the Mailbox servers store and manage mailbox data, the Edge Transport ensures secure email flow, the UM servers integrate voice messaging, and Active Directory provides the underlying infrastructure for user and configuration management.
24. Explain Exchange Server 2010 transport pipeline?
The transport pipeline in Exchange Server 2010 is a critical component responsible for processing and routing email messages as they flow through the Exchange organization. It consists of a series of stages, each performing specific actions on the messages. Here’s an overview of the Exchange Server 2010 transport pipeline stages:
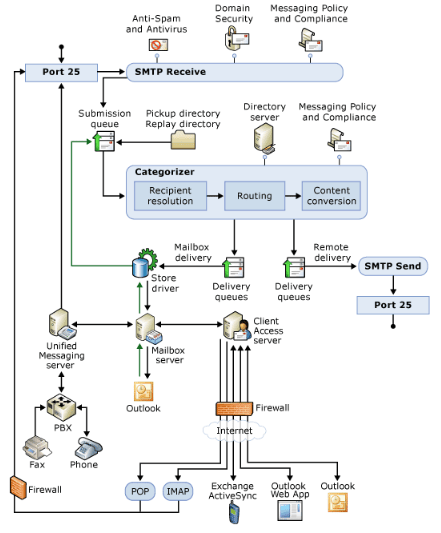
- Receive: The Receive stage is the first stage of the transport pipeline. It receives incoming messages from external sources or other Exchange servers. Messages are initially received by the Receive connector, which acts as a gateway for inbound email traffic. During this stage, the transport server performs basic checks, including message format validation and sender/recipient resolution.
- Preprocess: In the Preprocess stage, the transport server performs additional checks and manipulations on the incoming message. It applies transport rules, which are configured to enforce policies, perform message classifications, apply disclaimers, or apply content filtering. This stage allows for the application of organizational policies before further processing.
- Agent: The Agent stage is a customizable stage where third-party or custom-built agents can be installed to perform additional processing on messages. These agents can be used for various purposes such as antivirus scanning, anti-spam filtering, data loss prevention (DLP), or custom message manipulation. Agents have the ability to modify the message properties or take specific actions based on defined rules.
- Routing: The Routing stage determines the next hop for the message based on the recipient’s email address and the organization’s routing configuration. This stage ensures that messages are correctly routed to the appropriate destination, whether it’s a local mailbox server, a remote Exchange organization, or an external email server. Routing decisions are based on recipient resolution, delivery group membership, and connector configuration.
- Categorizer: The Categorizer stage is responsible for final recipient resolution, message delivery, and message tracking. It resolves distribution groups, expands dynamic distribution lists, and determines the mailbox server hosting the recipient’s mailbox. The Categorizer assigns delivery status and tracks the message through the delivery process.
- Delivery: The Delivery stage is where the message is handed off to the appropriate mailbox server for final delivery to the recipient’s mailbox. If the mailbox is located on the local server, the message is delivered directly. If the mailbox is located on a different server within the organization, the message is sent over the internal transport infrastructure. For external recipients, the message is routed through the Edge Transport server or external connectors.
- Transport Dumpster: The Transport Dumpster is a feature that protects against data loss in case of server or network failures. It stores a copy of the message in a highly available location, allowing for message recovery in the event of a failure. The Transport Dumpster is used in conjunction with the database-level redundancy provided by Database Availability Groups (DAGs) to ensure message resiliency.
- DSN (Delivery Status Notification): The DSN stage generates delivery status notifications, commonly known as bounce or non-delivery reports (NDRs). If a message cannot be delivered successfully, a DSN is generated and sent back to the original sender, providing information about the delivery failure.
Each stage in the Exchange Server 2010 transport pipeline plays a crucial role in processing, routing, and delivering email messages. The pipeline allows for various customization options, ensuring that organizations can implement policies, apply security measures, and perform additional processing based on their specific requirements.
25. Explain the process of managing mailbox permissions in Exchange Server 2010?
In Exchange Server 2010, managing mailbox permissions involves granting or revoking access rights to a mailbox for users or groups. These permissions determine what actions individuals can perform on the mailbox, such as reading, sending, or deleting messages. Here’s a step-by-step process for managing mailbox permissions in Exchange Server 2010:
- Open the Exchange Management Console (EMC): Launch the EMC on the Exchange Server or on a computer with the Exchange Management Tools installed.
- Navigate to the Recipient Configuration: In the EMC, expand the “Recipient Configuration” node, and click on “Mailbox” to view a list of mailboxes in the organization.
- Select the mailbox: Locate and select the mailbox for which you want to manage permissions from the list of mailboxes.
- Manage Full Access Permissions: To grant or revoke full access permissions, right-click the selected mailbox, choose “Manage Full Access Permission,” and select either “Add” or “Remove” to manage the list of users or groups with full access to the mailbox. You can search for users or groups by name or browse through the Active Directory.
- Manage Send As Permissions: To grant or revoke the “Send As” permission, right-click the mailbox, choose “Manage Send As Permission,” and use the “Add” or “Remove” buttons to manage the list of users or groups that can send messages on behalf of the mailbox.
- Manage Send on Behalf Permissions: To grant or revoke the “Send on Behalf” permission, right-click the mailbox, choose “Manage Send on Behalf Permission,” and use the “Add” or “Remove” buttons to manage the list of users or groups that can send messages on behalf of the mailbox.
- Manage Folder-Level Permissions: To manage permissions for specific folders within a mailbox, right-click the mailbox, choose “Manage Full Access Permission,” and select the “Folder Rights” button. In the folder permissions dialog box, you can add or remove users or groups and define their access rights to individual folders.
- Apply the changes: After making the desired permission changes, click “OK” to apply the changes. The changes will be propagated to the mailbox server and take effect shortly.
26. What is the process of configuring database maintenance in Exchange Server 2010?
Configuring database maintenance in Exchange Server 2010 involves setting up scheduled maintenance tasks to ensure the health and performance of mailbox databases. These tasks include online database maintenance, online defragmentation, and database backups. Here’s a step-by-step process to configure database maintenance:
- Open the Exchange Management Console (EMC): Launch the EMC on the Exchange Server or on a computer with the Exchange Management Tools installed.
- Navigate to the Organization Configuration: In the EMC, expand the “Organization Configuration” node, and click on “Mailbox” to view the mailbox-related configuration options.
- Select the Database Management tab: In the Organization Configuration pane, click on the “Database Management” tab to access the mailbox database management settings.
- Configure Online Maintenance: In the Database Management tab, select the mailbox database for which you want to configure maintenance tasks. Right-click the database and choose “Properties.” In the database properties window, go to the “Maintenance” tab.
- Enable Online Maintenance: Check the box for “Enable Circular Logging” if you want to enable online maintenance for the selected database. Circular logging allows for continuous database maintenance by automatically overwriting transaction logs. Note that circular logging should only be enabled for non-production or specific scenarios, as it limits the ability to recover data from transaction logs.
- Configure Online Defragmentation: In the database properties window, under the “Maintenance” tab, you can adjust the settings for online defragmentation. Online defragmentation reclaims whitespace in the database, reducing its physical size. Specify the schedule for when online defragmentation should run, such as during non-peak hours.
- Configure Database Backup: Regularly backing up Exchange mailbox databases is crucial for data protection and recovery. In the database properties window, under the “Maintenance” tab, click the “Browse” button next to the “Backup” option. Select the backup solution and schedule that suits your organization’s requirements. Follow the backup solution’s instructions to configure the backup schedule and destination.
- Apply the changes: After configuring the desired database maintenance settings, click “OK” to apply the changes.
27. How to configure Microsoft Exchange Server 2010?
Configuring Microsoft Exchange Server 2010 involves several steps to set up and customize the server for your organization’s email communication and collaboration needs. Here’s a high-level overview of the process:
- Prepare the Environment:
- Ensure that the server hardware meets the system requirements for Exchange Server 2010.
- Install the required operating system (typically Windows Server) and ensure it’s fully updated.
- Install any prerequisite software and components, such as the .NET Framework, Windows Remote Management (WinRM), and PowerShell.
- Install Exchange Server 2010:
- Launch the Exchange Server installation wizard and follow the on-screen instructions.
- Choose the appropriate installation option, such as a new installation or upgrading from a previous version.
- Specify the installation location and configure the organization and administrative settings, including the organization name, domain, and administrator account.
- Configure Server Roles:
- Determine the server roles you want to deploy, such as Mailbox, Client Access, Hub Transport, and Unified Messaging.
- Use the Exchange Management Console (EMC) or Exchange Management Shell (EMS) to assign the appropriate roles to each server in your organization.
- Configure server settings and role-specific features, such as email address policies, virtual directories, and transport rules.
- Configure Mailbox Databases:
- Create and configure mailbox databases using the EMC or EMS.
- Specify database settings, such as the database name, location, size limits, and database maintenance schedule.
- Consider implementing Database Availability Groups (DAGs) for high availability and database replication.
- Configure Client Access:
- Configure client access protocols, such as Outlook Web App (OWA), Outlook Anywhere, Exchange ActiveSync, and POP/IMAP.
- Set up certificates for secure client access and configure SSL settings.
- Customize the OWA appearance and user experience, if desired.
- Configure Transport Settings:
- Set up Send and Receive connectors to control mail flow between Exchange servers and external systems.
- Configure transport rules to apply email policies, content filtering, or routing conditions.
- Implement anti-spam and antivirus protection by configuring filtering agents and third-party software integration.
- Configure Unified Messaging (optional):
- Install and configure the Unified Messaging (UM) role if you plan to integrate voice messaging and telephony features.
- Configure UM dial plans, auto attendants, and voicemail settings.
- Test and Verify Configuration:
- Validate the Exchange Server installation and configuration by sending test emails, accessing mailboxes, and performing basic tasks.
- Monitor system health and performance using built-in tools, such as Exchange Management Console, Exchange Management Shell, and performance monitoring tools.
- Implement Backup and Disaster Recovery:
- Set up regular backups of Exchange databases and critical system components.
- Create a disaster recovery plan and test the recovery process to ensure data and service availability in case of failures.
- Configure Additional Features and Customizations:
- Explore and configure additional features, such as public folders, journaling, retention policies, and information rights management (IRM).
- Customize settings and policies based on your organization’s requirements and compliance needs.
28. How can you configure journaling in Exchange Server 2010?
Journaling in Exchange Server 2010 allows you to record a copy of all email communications within your organization for compliance, legal, or archival purposes. Here’s a step-by-step guide on how to configure journaling in Exchange Server 2010:
- Open the Exchange Management Console (EMC): Launch the EMC on the Exchange Server or on a computer with the Exchange Management Tools installed.
- Navigate to the Organization Configuration: In the EMC, expand the “Organization Configuration” node, and click on “Hub Transport” to access the Hub Transport configuration settings.
- Select the Hub Transport Server: In the Organization Configuration pane, select the Hub Transport server where you want to configure journaling.
- Configure Journaling Rules:
- In the Actions pane, click on “New Journal Rule” to start the New Journal Rule wizard.
- Enter a descriptive name for the journaling rule.
- Select the Scope of the rule. You can choose to journal messages sent to and from specific users, distribution groups, or all messages within the organization.
- Specify the Journal Recipient, which is the mailbox or mail-enabled user that will receive the journal reports. This mailbox should be dedicated to storing journal reports and should have appropriate access permissions.
- Choose the Journal Messages with Recipient Types option. You can select either Internal or External, or both, depending on your requirements.
- Set the Journal Messages for the following Senders option to All Senders or Specific Senders as needed.
- Select the Enable Rule checkbox to activate the journaling rule.
- Configure Journaling Report Options:
- In the New Journal Rule wizard, click on “Browse” next to the Journal Report NDR Recipient field to select the mailbox or user who will receive non-delivery reports (NDRs) for journal reports that cannot be delivered.
- Choose the Format of the journal reports. You can select either Envelope Journal Report or Standard Journal Report, depending on your preferences and compliance requirements.
- Specify the Maximum Message Size for journal reports.
- Set the options for the journal report’s MAPI properties and message class, if needed.
- Review and Complete the Configuration: Review the settings you have configured in the New Journal Rule wizard. If everything is accurate, click “New” to create the journaling rule.
- Verify the Journaling Configuration: After creating the journaling rule, it’s essential to verify that it’s working as expected. Send test emails and check if the journal reports are being generated and delivered to the designated journaling recipient mailbox.
29. What is the process of configuring message archiving in Exchange Server 2010?
In Exchange Server 2010, message archiving can be configured to help manage mailbox sizes, improve performance, and meet compliance and regulatory requirements. Here’s a step-by-step process to configure message archiving in Exchange Server 2010:
- Determine Archiving Requirements: Identify the archiving policies and requirements for your organization, including retention periods, storage capacity, and compliance regulations.
- Enable Archiving Mailbox Database:
- Open the Exchange Management Console (EMC).
- Navigate to the Organization Configuration, select the Mailbox node, and click on the “Database Management” tab.
- Select the mailbox database for which you want to enable archiving.
- Right-click the database and choose “Properties.”
- In the database properties window, go to the “Maintenance” tab.
- Check the “Enable Single Item Recovery” checkbox to enable archiving on the database.
- Create Archiving Policies:
- In the EMC, navigate to the Organization Configuration and select the Mailbox node.
- Go to the “Retention Policies” tab.
- Right-click in the area and choose “New Retention Policy.”
- Give the policy a name and description.
- Add retention tags to the policy, specifying the retention period and action (archive or delete) for each tag.
- Configure the default policy to apply to mailboxes that don’t have a specific policy assigned.
- Save the policy.
- Assign Archiving Policies to Mailboxes:
- In the EMC, navigate to the Recipient Configuration and select the Mailbox node.
- Locate and select the mailbox for which you want to assign the archiving policy.
- Right-click the mailbox and choose “Properties.”
- Go to the “Mailbox Settings” tab.
- Double-click on “Messaging Records Management.”
- Check the “Enable” checkbox to enable MRM (Messaging Records Management) for the mailbox.
- Choose the archiving policy you want to assign from the “Retention Policy” dropdown menu.
- Save the changes.
- Verify and Test Archiving:
- Monitor the mailbox usage and verify that messages are being automatically moved to the archive mailbox based on the assigned policy.
- Test the archiving functionality by sending and receiving emails, ensuring that messages are properly archived according to the configured retention settings.
- Configure Storage for Archive Mailboxes:
- Plan and allocate sufficient storage capacity to accommodate the archived messages.
- Consider implementing a separate storage solution, such as Exchange Online Archiving (EOA) or a third-party archiving system, for long-term storage and advanced archiving capabilities if required.
30. Explain the concept of resource mailboxes in Exchange Server 2010?
In Exchange Server 2010, resource mailboxes are a type of mailbox that represents a non-human, physical or virtual resource within an organization. These mailboxes are used to schedule and manage resources such as conference rooms, equipment, or other shared resources. Resource mailboxes help facilitate the efficient and organized booking of these resources for meetings, events, or other activities. Here are key aspects of resource mailboxes in Exchange Server 2010:
- Purpose and Functionality: Resource mailboxes serve as a central entity for managing and scheduling resources. They allow users to book and reserve resources for specific time slots, ensuring their availability and avoiding conflicts. Resource mailboxes help optimize resource utilization and streamline the process of reserving shared resources.
- Resource Scheduling: Users can create meeting requests or book resources by including the resource mailbox as an attendee or by directly inviting the resource mailbox to the meeting. Exchange Server’s scheduling functionality checks the availability of the resource mailbox and provides users with information on its availability during the requested time slot. This helps prevent double bookings and conflicts.
- Auto-Accept and Auto-Decline: Resource mailboxes can be configured with specific policies to automatically accept or decline meeting requests based on availability and predefined booking rules. Auto-acceptance allows resource mailboxes to automatically accept meeting requests and add them to the resource’s calendar. Auto-decline can be set up to decline meeting requests that conflict with existing bookings or violate certain rules.
- Resource Booking Delegates: Resource mailboxes can have designated delegates who can manage and schedule bookings on behalf of the resource. Delegates can accept or decline meeting requests, modify booking details, and manage the resource mailbox’s calendar. This delegation feature allows for centralized management of resource bookings and eases the burden on individual resource owners.
- Resource Policies and Customization: Resource mailboxes can have specific policies and custom settings configured. These settings include booking window limits, maximum duration for bookings, and other parameters to define resource usage and availability. Administrators can enforce policies to control how resources are booked and to ensure fair and efficient resource utilization.
- Viewing Resource Availability: Users can view the availability of a resource mailbox by checking its calendar through the scheduling assistant in Outlook or other Exchange clients. The calendar displays existing bookings and availability information, helping users make informed decisions when scheduling meetings or events.
31. How can you configure anti-spam and anti-malware features in Exchange Server 2010?
To configure anti-spam and anti-malware features in Exchange Server 2010, you can use the built-in tools and features available. Here’s a step-by-step guide:
- Enable the Anti-Spam and Anti-Malware Agents:
- Open the Exchange Management Console (EMC) on the Exchange Server.
- Navigate to the Organization Configuration node and select the Hub Transport role.
- In the Work pane, click on the “Anti-Spam” tab.
- Enable the anti-spam agents by right-clicking on “Anti-Spam Settings” and selecting “Enable Anti-Spam Features.”
- Configure Content Filtering:
- In the Anti-Spam tab, click on “Content Filtering” under the Anti-Spam features section.
- Configure the content filtering settings, such as the SCL (Spam Confidence Level) threshold, which determines how aggressively emails are marked as spam.
- Specify the actions to take for messages that exceed the SCL threshold, such as rejecting, quarantining, or stamping them with a spam tag.
- Consider adjusting the settings for specific actions, such as the quarantine mailbox or the NDR (non-delivery report) options.
- Enable Sender Filtering:
- In the Anti-Spam tab, click on “Sender Filtering” under the Anti-Spam features section.
- Enable sender filtering to block or allow messages based on specific senders or domains.
- Configure the sender filtering settings, including adding blocked senders or allowed senders/domains.
- Configure Recipient Filtering:
- In the Anti-Spam tab, click on “Recipient Filtering” under the Anti-Spam features section.
- Enable recipient filtering to block messages sent to specific recipients or domains that don’t exist in your organization.
- Configure the recipient filtering settings, including the options to block messages to unknown recipients or to generate NDRs for blocked recipients.
- Enable and Configure the Sender ID Agent:
- In the Anti-Spam tab, click on “Sender ID” under the Anti-Spam features section.
- Enable the Sender ID agent to validate the sender’s email address against the SPF (Sender Policy Framework) record of the sending domain.
- Configure the Sender ID agent settings, such as the action to take for failed Sender ID checks, like rejecting or marking the messages.
- Enable and Configure the Content Filtering Agent:
- In the Anti-Spam tab, click on “Content Filtering” under the Transport Rules section.
- Enable the Content Filtering agent to scan the content of messages for potential spam or malware.
- Configure the Content Filtering agent settings, such as the actions to take for detected spam or malware, such as rejecting, deleting, or quarantining the messages.
- Update Anti-Spam and Anti-Malware Definitions:
- Ensure that you have regular updates for the anti-spam and anti-malware definitions in Exchange Server 2010.
- Configure automatic updates to keep the definitions up to date and maintain the effectiveness of the protection.
- Test and Monitor:
- Test the anti-spam and anti-malware features by sending test messages with known spam or malware content.
- Monitor the effectiveness of the anti-spam and anti-malware features and make adjustments as needed based on the performance and organization’s requirements.
By configuring these anti-spam and anti-malware features, you can enhance the security of your Exchange Server 2010 environment and protect against unwanted and malicious email content.
32. What is the process of implementing message retention and deletion policies in Exchange Server 2010?
In Exchange Server 2010, you can implement message retention and deletion policies using a feature called “Messaging Records Management” (MRM). MRM allows you to define policies that automatically manage the lifecycle of messages in your Exchange environment, including retention, deletion, and archiving.
Here is a general process for implementing message retention and deletion policies in Exchange Server 2010:
- Plan your retention policy: Determine your organization’s requirements and regulatory compliance obligations regarding message retention. Consider factors such as how long messages should be retained, which mailboxes or users are subject to the policy, and any legal or industry-specific requirements.
- Configure retention tags: Retention tags are used to specify the retention settings for different message types. You can create different retention tags based on your requirements. For example, you may have a tag to retain messages for seven years, another tag to retain messages for 30 days, and so on.
- Create retention policies: A retention policy is a collection of retention tags that are applied to mailboxes. You can create retention policies based on different criteria, such as department, role, or legal requirements. For example, you may have a retention policy for all employees and a separate policy for executives.
- Apply retention policies to mailboxes: Once you have created the retention policies, you can apply them to the relevant mailboxes. You can assign policies to individual mailboxes or use recipient filters to apply policies to multiple mailboxes at once.
- Configure default folder policy: The default folder policy defines the retention settings for default folders like Inbox, Sent Items, and Deleted Items. You can configure the default folder policy to apply specific retention tags to these folders.
- Test and monitor: After applying the retention policies, it’s important to test their effectiveness and monitor their implementation. Ensure that messages are being retained or deleted as intended and review any exceptions or issues that may arise.
- Train users and communicate: Inform users about the retention policies and explain any changes or expectations regarding message retention and deletion. Provide guidance on how to organize and manage their mailbox content effectively.
33. How can you troubleshoot mail flow issues in Exchange Server 2010?
Troubleshooting mail flow issues in Exchange Server 2010 involves identifying and resolving problems that prevent the smooth flow of emails. Here are some steps you can take to troubleshoot mail flow issues:
- Check server connectivity: Ensure that the Exchange Server is properly connected to the network and can communicate with other servers and devices. Verify network connectivity, DNS resolution, and firewall settings.
- Review message queues: Use the Exchange Management Console or Exchange Management Shell to check the status of message queues on the Exchange Server. Look for any backlogs or queues with a large number of messages. Investigate and resolve any issues causing message delays or failures.
- Test internal mail flow: Send test emails between mailboxes within the Exchange Server organization. If internal mail flow is working correctly, it suggests that the issue lies with external mail flow.
- Test external mail flow: Send test emails from external email accounts to your Exchange Server mailboxes. If external emails are not being received, check DNS records (MX, SPF, PTR) to ensure they are correctly configured. Verify that your firewall is allowing incoming SMTP traffic to the Exchange Server.
- Analyze message tracking logs: Enable message tracking on the Exchange Server and review the message tracking logs. These logs provide detailed information about the path of an email message and can help identify any issues or errors encountered during delivery.
- Check transport and receive connectors: Verify the configuration of transport and receive connectors on the Exchange Server. Ensure that the connectors are correctly configured to accept incoming connections and deliver outgoing emails. Review settings such as port numbers, IP address restrictions, authentication, and TLS encryption.
- Review anti-spam and antivirus software: If you have anti-spam or antivirus software installed on the Exchange Server, check its configuration. Ensure that the software is not blocking legitimate emails or causing delays in mail delivery.
- Monitor server resources: Check the server’s CPU, memory, and disk usage to ensure that it has sufficient resources to handle mail flow. Insufficient resources can impact the performance of the Exchange Server and result in mail flow issues.
- Test mail flow using telnet: Use the Telnet command to manually connect to the Exchange Server’s SMTP port (usually port 25) from a remote computer. This can help diagnose issues with the SMTP service and validate connectivity.
- Consult Exchange Server logs: Examine the Exchange Server logs, including event logs, for any error messages or warnings that might indicate underlying issues affecting mail flow. Take appropriate action based on the information provided in the logs.
34. How do you install Exchange Server 2010?
Installing Exchange Server 2010 involves several steps to ensure a successful deployment. Here’s a general outline of the installation process:
- Prepare the server:
- Ensure that the server meets the hardware and software requirements specified by Microsoft for Exchange Server 2010.
- Install the required operating system (e.g., Windows Server 2008 or later) and any necessary updates or service packs.
- Join the server to the appropriate Active Directory domain.
- Install the required prerequisites:
- Install the necessary Windows features and components required by Exchange Server 2010, such as the .NET Framework, Windows Remote Management (WinRM), and Windows PowerShell features.
- Run the Exchange Server 2010 Readiness Check, which verifies if the server meets all the prerequisites.
- Obtain and prepare the installation media:
- Download the Exchange Server 2010 installation files from the Microsoft website or insert the installation DVD into the server.
- Extract the installation files to a local drive or a network share accessible from the server.
- Install Exchange Server 2010:
- Launch the Exchange Server 2010 installation wizard by running the Setup.exe file.
- Follow the installation wizard’s prompts, including accepting the license agreement, specifying the installation location, and selecting the server roles to be installed (e.g., Mailbox, Client Access, Hub Transport).
- Provide the necessary organization and administrative information when prompted.
- Configure Exchange Server 2010:
- After the installation completes, you can use the Exchange Management Console or Exchange Management Shell to configure various settings, such as creating mailboxes, configuring email address policies, and setting up connectors for mail flow.
- Configure client access and connectivity:
- Depending on your environment, you may need to configure external access and connectivity options, such as configuring DNS records, setting up SSL certificates, and configuring firewall rules to allow traffic to the Exchange Server.
- Test and verify functionality:
- Test mail flow by sending and receiving emails to and from both internal and external recipients.
- Verify that clients can connect to Exchange Server 2010 and access their mailboxes using various client applications, such as Outlook, Outlook Web App (OWA), and mobile devices.
35. How do you uninstall Microsoft exchange server 2010?
To uninstall Microsoft Exchange Server 2010, you can use the following steps:
- Open the Control Panel on the server where Exchange Server 2010 is installed.
- Click on “Programs” or “Programs and Features” (depending on your Windows version).
- Locate “Microsoft Exchange Server 2010” in the list of installed programs and select it.
- Click on the “Uninstall” or “Change” button at the top of the list.
- The Exchange Server 2010 Setup wizard will launch. Select the option to “Remove” or “Uninstall” Exchange Server 2010 and click “Next”.
- On the “Server Role Selection” page, select the server roles you want to remove. By default, all server roles will be selected. If you want to completely uninstall Exchange Server 2010, ensure that all roles are selected.
- Click “Next” to proceed to the readiness checks. The wizard will perform a series of checks to ensure that the server is ready for uninstallation. Address any issues that are flagged before continuing.
- Review the installation summary and click “Remove” to start the uninstallation process.
- The uninstallation process will begin, and you will see a progress bar indicating the status. Allow the process to complete.
- Once the uninstallation is finished, you will see a completion screen. Review the summary information, and if desired, click “Finish” to close the wizard.
- Restart the server to complete the uninstallation process.
It’s important to note that uninstalling Exchange Server 2010 will remove all Exchange-related components from the server. Before proceeding with the uninstallation, ensure that you have a proper backup of your Exchange data and that you have planned for any necessary migration or transition to a different email solution if needed.
36. Explain the process of implementing mobile device management in Exchange Server 2010?
Exchange Server 2010 includes a feature called “Exchange ActiveSync” (EAS) that enables mobile device management (MDM) capabilities. With Exchange ActiveSync, you can enforce security policies, manage mobile devices, and control access to Exchange mailboxes. Here is an overview of the process of implementing mobile device management in Exchange Server 2010:
- Configure Exchange ActiveSync:
- Ensure that the Exchange ActiveSync service is enabled on the Exchange Server. This service is typically enabled by default.
- Configure the global Exchange ActiveSync settings, such as maximum attachment size, device password requirements, and device encryption requirements. These settings will apply to all mobile devices connecting to Exchange Server.
- Set up device access rules:
- Specify the devices that are allowed or blocked from accessing Exchange Server. You can create access rules based on device type, mobile operating system, or other criteria.
- Define whether devices need to be approved before they can connect to Exchange Server.
- Enable device partnerships:
- Decide whether you want to allow mobile devices to synchronize with Exchange Server without requiring device partnerships, or if you want to enforce device partnerships for additional control and management.
- If you choose to enforce device partnerships, configure the partnership settings, such as the maximum number of partnerships per user or the maximum number of devices per partnership.
- Configure security policies:
- Define security policies to enforce on mobile devices. These policies may include requirements for device passwords, minimum password length, password complexity, device encryption, and remote wipe capabilities.
- Specify whether devices should be automatically wiped after a certain number of failed login attempts or after a specified period of inactivity.
- Test and monitor:
- Connect mobile devices to Exchange Server using Exchange ActiveSync and verify that the security policies and access rules are being applied correctly.
- Monitor the Exchange Server logs and device synchronization activities to ensure proper functioning and troubleshoot any issues that arise.
- Educate users:
- Inform users about the mobile device management policies and guidelines in place.
- Provide instructions on how to configure their mobile devices to connect to Exchange Server using Exchange ActiveSync.
- Educate users on security best practices and how to protect their mobile devices and Exchange data.
Interview questions on Exchange Server 2010 for advanced level
37. Explain the process of configuring database availability and site resilience using multiple datacenters.
Configuring database availability and site resilience using multiple datacenters involves implementing measures to ensure high availability and disaster recovery for Exchange Server databases across multiple locations. Here is a general process for configuring database availability and site resilience:
- Plan your architecture:
- Determine the number and locations of datacenters that will host Exchange Server databases.
- Consider factors such as network connectivity, hardware requirements, and disaster recovery objectives.
- Configure Active Directory Sites:
- Create and configure Active Directory Sites to represent the physical locations of your datacenters.
- Associate appropriate subnets with each site to establish network connectivity and optimize data replication.
- Deploy Exchange Server:
- Install Exchange Server in each datacenter according to Microsoft’s recommended guidelines.
- Configure server roles such as Mailbox, Client Access, and Hub Transport based on your requirements.
- Create Database Availability Groups (DAGs):
- Configure Database Availability Groups (DAGs) to provide high availability for Exchange databases.
- Add Mailbox servers in each datacenter to the DAG, ensuring that each database has multiple copies across multiple locations.
- Configure Database Replication:
- Enable continuous replication of Exchange databases between servers within the DAG.
- Use technologies like Database Availability Group (DAG) and Exchange Database Mobility to ensure database copies are synchronized.
- Implement Database Activation Preference:
- Set database activation preferences to prioritize which database copies should be activated in case of a failure.
- Define activation preferences based on factors such as datacenter location, network bandwidth, or performance considerations.
- Configure Load Balancers:
- Deploy load balancers to distribute client traffic across multiple Client Access servers in each datacenter.
- Configure load balancing rules to ensure optimal performance and availability.
- Implement Site Resilience Measures:
- Establish disaster recovery measures such as geo-redundant storage, backup solutions, and off-site backups to protect Exchange Server data.
- Implement mechanisms for replicating Active Directory and DNS services across datacenters.
- Test and Monitor:
- Regularly test failover and failback scenarios to ensure that database availability and site resilience mechanisms are functioning as expected.
- Monitor the health and performance of Exchange servers, databases, and network connectivity using built-in tools or third-party monitoring solutions.
- Document and Update:
- Document the configuration, procedures, and recovery steps for database availability and site resilience.
- Keep the documentation up to date as your infrastructure evolves or new datacenters are added.
38. How can you configure federation trust and sharing in Exchange Server 2010?
In Exchange Server 2010, you can configure federation trust and sharing to enable secure collaboration and sharing of resources with external organizations. Federation trust establishes a trust relationship between Exchange organizations, allowing users to share calendar information, free/busy data, and contact details. Here is an overview of the process to configure federation trust and sharing in Exchange Server 2010:
- Prepare for Federation Trust:
- Obtain the necessary information from the external organization, such as the federation endpoint URL, certificate requirements, and authentication methods.
- Ensure that the Exchange Server has a valid SSL certificate that matches the namespace used for federation.
- Configure Organization Relationships:
- Create an organization relationship with the external organization using the Exchange Management Console (EMC) or Exchange Management Shell (EMS).
- Specify the external organization’s federated domain and the type of sharing relationship (e.g., CalendarSharingFreeBusyOnly, FullAccess).
- Configure Federation Trust:
- Create a Federation Trust with the external organization using the EMC or EMS.
- Provide the federation endpoint URL, certificate details, and authentication settings obtained from the external organization.
- Complete the trust configuration process by following the prompts and reviewing the summary information.
- Test Federation Trust:
- Validate the federation trust by performing test operations, such as sharing calendar information, checking free/busy data, and verifying contact details with users from the external organization.
- Manage Organization Relationships:
- Modify or remove organization relationships as needed using the EMC or EMS.
- Adjust the sharing settings, access levels, or domain settings based on the requirements and agreements with the external organization.
- Monitor and Troubleshoot:
- Monitor federation trust activity and track any issues related to sharing and collaboration.
- Use Exchange logs, event viewer, and message tracking tools to troubleshoot and diagnose any problems encountered during the federation process.
39. What is the process of implementing unified messaging in Exchange Server 2010?
Implementing unified messaging in Exchange Server 2010 allows users to access voicemail, email, and calendar information through a single interface. Here is an overview of the process to implement unified messaging:
- Prepare the Exchange Server:
- Ensure that the Exchange Server 2010 is installed and configured correctly with the necessary server roles, such as Mailbox, Client Access, and Unified Messaging (UM).
- Configure the Exchange Server to integrate with the telephony infrastructure, such as IP-PBX or SIP trunking.
- Configure Unified Messaging Role:
- Enable the Unified Messaging role on the Exchange Server using the Exchange Management Console (EMC) or Exchange Management Shell (EMS).
- Configure the UM settings, such as the dial plan, auto attendant, and UM mailbox policies.
- Configure Dial Plans:
- Create dial plans to define the numbering scheme, call routing, and language settings for the unified messaging system.
- Specify parameters like country/region codes, extension lengths, and voice recognition settings.
- Configure Auto Attendants:
- Create auto attendants to provide automated call handling and routing options to callers.
- Define the greeting messages, menu options, key mappings, and call transfer settings for the auto attendant.
- Configure UM Mailbox Policies:
- Create UM mailbox policies to define the settings for UM-enabled mailboxes.
- Specify parameters such as PIN policies, call answering rules, playback settings, and voicemail greeting requirements.
- Assign UM Policies to Mailboxes:
- Associate the appropriate UM mailbox policies with user mailboxes to enable unified messaging functionality.
- Set the necessary UM-specific settings for each mailbox, such as language preferences and call answering rules.
- Enable UM Features:
- Configure the Exchange Server to integrate with the telephony infrastructure, such as connecting to IP-PBX or configuring SIP trunking settings.
- Enable UM features, such as Call Answering, Voicemail, and Calendar Integration, to provide unified messaging capabilities.
- Test and Validate:
- Test unified messaging functionality by making test calls, leaving voicemails, and accessing voicemail from both internal and external phone lines.
- Verify that users can access voicemail messages through their email clients or other supported interfaces.
- User Training and Support:
- Provide training and documentation to users on how to access and utilize the unified messaging features.
- Address any user questions or issues related to unified messaging and provide ongoing support as needed.
40. How can you configure role-based access control (RBAC) in Exchange Server 2010?
Role-Based Access Control (RBAC) in Exchange Server 2010 allows you to control and manage permissions and access rights for administrators and users. RBAC provides a granular approach to granting permissions based on predefined roles. Here’s an overview of the process to configure RBAC in Exchange Server 2010:
- Understand RBAC Components:
- Familiarize yourself with the RBAC components in Exchange Server 2010, such as management roles, management role groups, and role assignments.
- Management roles define a set of permissions that can be assigned to administrators or users.
- Management role groups are collections of users who are assigned management roles.
- Role assignments connect management roles with management role groups or individual users.
- Identify Administrative Roles:
- Determine the administrative roles that need to be defined based on your organization’s requirements.
- Consider roles such as Organization Management, Recipient Management, Transport Management, and so on.
- Determine the specific permissions required for each role.
- Create Custom Management Roles (if necessary):
- If the predefined management roles don’t meet your requirements, you can create custom management roles.
- Use the Exchange Management Shell (EMS) to define new management roles and specify the desired permissions for each role.
- Create Management Role Groups:
- Identify groups of administrators or users who require similar sets of permissions.
- Create management role groups using the EMS or Exchange Control Panel (ECP) to associate the appropriate management roles with the groups.
- Examples of default management role groups include Organization Management, Recipient Management, and View-Only Organization Management.
- Assign Roles to Role Groups or Users:
- Assign the appropriate management roles to the management role groups or individual users.
- Use the EMS or ECP to assign roles to the role groups or users based on their responsibilities and required access levels.
- Test and Verify:
- Verify that the assigned roles and permissions are working as expected by logging in with the assigned user accounts and performing relevant administrative tasks.
- Validate that users and administrators have the appropriate level of access based on their assigned roles.
- Regularly Review and Update:
- Regularly review and update the RBAC configuration as your organization’s needs change.
- Remove unnecessary role assignments, add new role assignments, or modify existing roles and role groups based on administrative requirements.
41. Explain the process of implementing hybrid deployment with Office 365 in Exchange Server 2010.
Implementing a hybrid deployment with Office 365 and Exchange Server 2010 allows organizations to integrate on-premises Exchange infrastructure with Exchange Online, enabling a seamless coexistence and migration experience. Here’s an overview of the process to implement a hybrid deployment:
- Review Prerequisites:
- Ensure that your Exchange Server 2010 environment meets the necessary prerequisites for a hybrid deployment, including the required service packs and cumulative updates.
- Verify that your Active Directory infrastructure is healthy and properly configured.
- Set Up and Configure Office 365 Tenant:
- Sign up for an Office 365 subscription and set up your Office 365 tenant.
- Assign the necessary licenses to user accounts that will be migrated to Exchange Online.
- Configure Exchange Hybrid Configuration Wizard (HCW):
- Run the Exchange Hybrid Configuration Wizard (HCW) to automate the configuration process.
- Provide the required information, such as on-premises Exchange server details, Office 365 credentials, and hybrid deployment options.
- HCW will configure the necessary connectors, transport rules, and other settings to enable hybrid functionality.
- Plan and Perform Mailbox Migration:
- Determine the migration strategy based on your organization’s requirements, such as a staged, cutover, or hybrid migration.
- Set up migration endpoints to establish the connection between on-premises Exchange Server and Exchange Online.
- Use tools like the Exchange Management Shell (EMS) or Exchange Admin Center (EAC) to migrate mailboxes, public folders, and other resources to Exchange Online.
- Test and Validate the Hybrid Configuration:
- Perform tests to ensure that mail flow, free/busy sharing, and other hybrid functionalities are working as expected.
- Verify that migrated mailboxes can access their data in Exchange Online and that coexistence features, such as shared calendars and GAL synchronization, function correctly.
- Manage and Monitor the Hybrid Environment:
- Use the Exchange Admin Center or Exchange Management Shell to manage and monitor the hybrid environment.
- Monitor the health and performance of servers, mail flow, and hybrid connectors.
- Keep track of any synchronization or migration issues and address them promptly.
- Decommission On-Premises Exchange (optional):
- If desired, you can decommission the on-premises Exchange Server 2010 environment once all mailboxes have been migrated to Exchange Online.
- Ensure that you have appropriate backups and archives of your on-premises Exchange data before decommissioning any servers.
42. What are the different backup and recovery options available for Exchange Server 2010?
Exchange Server 2010 provides several backup and recovery options to protect and restore mailbox data and server configurations. Here are the different options available for backup and recovery in Exchange Server 2010:
- Windows Server Backup:
- Windows Server Backup is a built-in feature of Windows Server 2008 and later versions.
- It can be used to back up and restore Exchange Server 2010 databases, transaction logs, and the server configuration.
- Windows Server Backup creates Volume Shadow Copy Service (VSS) backups, which can be used for granular mailbox or item-level recovery.
- Exchange Server Native Data Protection:
- Exchange Server 2010 includes built-in database-level and item-level recovery features.
- The Exchange Native Data Protection (NDB) feature allows you to use database redundancy and lagged database copies to protect against database failures.
- Database Availability Groups (DAGs) provide high availability and automatic database failover in case of server or database failures.
- Third-Party Backup Solutions:
- Many third-party backup solutions are available that offer advanced features and options for backing up and recovering Exchange Server 2010.
- These solutions often provide granular item-level recovery, faster backup and restore times, and additional management features.
- Popular third-party backup solutions include products from vendors like Veritas, Commvault, Veeam, and Dell EMC.
- Exchange Server Recovery Database (RDB):
- The Recovery Database (RDB) is a special database in Exchange Server 2010 that can be used for recovery purposes.
- It allows you to restore mailbox data from backups directly to the RDB and then extract specific mailbox data using mailbox recovery tools.
- The RDB can be helpful for recovering individual mailboxes or mailbox items in scenarios such as accidental deletion or corruption.
- Deleted Item Recovery:
- Exchange Server 2010 has built-in features for recovering deleted items.
- Users can typically recover deleted items from their Deleted Items folder or recover deleted mailboxes from the disconnected mailboxes feature.
- The retention period for deleted items can be configured to control how long items are kept and recoverable.
43. How can you configure message encryption and digital rights protection in Exchange Server 2010?
Exchange Server 2010 does not natively support message encryption and digital rights protection. These features were introduced in later versions of Exchange Server, such as Exchange Server 2013 and Exchange Server 2016.
However, if you are using Exchange Server 2010 and require message encryption and digital rights protection, you can consider integrating third-party solutions or using add-ons that provide these capabilities. Here are some options:
- Secure/Multipurpose Internet Mail Extensions (S/MIME): S/MIME is a widely used encryption standard for email communication. You can configure S/MIME certificates on client devices and Exchange Server 2010 to enable encryption and digital signing of email messages.
- Third-party encryption solutions: There are various third-party encryption solutions available that can integrate with Exchange Server 2010 to provide message encryption and digital rights protection. These solutions typically involve installing additional software or services on the Exchange Server to enable the desired functionality.
- Information Rights Management (IRM): Although Exchange Server 2010 does not have native IRM support, you can utilize Microsoft Azure Rights Management (Azure RMS) to add digital rights protection to email messages. Azure RMS can be integrated with Exchange Server 2010 to apply rights management policies and encryption to sensitive emails.
44. Explain the process of configuring Outlook Web App (OWA) in Exchange Server 2010?
To configure Outlook Web App (OWA) in Exchange Server 2010, you need to perform the following steps:
- Configure Client Access Server Role: Ensure that the Client Access Server (CAS) role is installed and properly configured on your Exchange Server 2010. The CAS role provides the web services required for OWA.
- Enable Outlook Web App: Open the Exchange Management Console on the Exchange Server and navigate to the “Server Configuration” section. Select the Client Access server on which you want to enable OWA and click on “Enable Outlook Web App” from the action pane. Follow the prompts to complete the configuration.
- Configure OWA Virtual Directory: Open the Internet Information Services (IIS) Manager on the Exchange Server. Expand the server name, go to “Sites,” and locate the “Default Web Site.” Right-click on it and select “Properties.” Go to the “Directory Security” tab and click on “Edit” in the “Authentication and access control” section. Ensure that “Anonymous access” is enabled and “Integrated Windows authentication” is selected.
- Configure SSL Certificate: OWA requires a valid SSL certificate for secure communication. Obtain an SSL certificate from a trusted certificate authority (CA) and install it on the Exchange Server. In the IIS Manager, select the “Default Web Site” and go to “Bindings” in the action pane. Add a new binding for HTTPS, select the installed SSL certificate, and specify the appropriate TCP port (usually 443).
- Test OWA Access: Open a web browser on a client machine and enter the OWA URL in the following format: https://<OWA_URL>/owa. Replace “<OWA_URL>” with the fully qualified domain name (FQDN) or IP address of your Exchange Server. Log in using valid user credentials and verify that OWA loads successfully.
- Configure OWA Features: You can customize various OWA features and settings based on your requirements. To do this, open the Exchange Management Console, navigate to the “Organization Configuration” section, and select “Client Access.” In the action pane, click on “Outlook Web App Mailbox Policies” to create or modify mailbox policies. These policies control the behavior and appearance of OWA for different user groups.
45. What are the best practices for managing and monitoring Exchange Server 2010?
Managing and monitoring Exchange Server 2010 effectively involves following best practices to ensure optimal performance, security, and availability. Here are some recommended best practices for managing and monitoring Exchange Server 2010:
- Regular Patching and Updates: Stay up to date with the latest service packs, cumulative updates, and security patches provided by Microsoft. Regularly apply these updates to ensure the server is secure and benefits from bug fixes and performance improvements.
- Monitor Server Performance: Implement monitoring tools to track the performance of your Exchange Server 2010 environment. Monitor key metrics such as CPU usage, memory utilization, disk I/O, and network traffic. This helps identify performance bottlenecks and potential issues before they impact users.
- Capacity Planning: Monitor server resource utilization trends to forecast future capacity requirements. Analyze data growth, mailbox sizes, and user activity patterns to ensure sufficient storage, memory, and processing power are available. Proactively plan for hardware upgrades or additional server deployments as needed.
- Backup and Disaster Recovery: Implement regular backup and disaster recovery procedures to protect against data loss. Schedule regular backups of mailbox databases, configuration settings, and other critical components. Test the restoration process periodically to ensure backups are reliable and recoverable.
- Security Measures: Implement appropriate security measures to safeguard Exchange Server 2010. This includes using strong passwords, enabling encryption, enforcing secure connections (HTTPS), and implementing firewalls and intrusion detection systems. Regularly review security configurations and access controls to minimize the risk of unauthorized access or data breaches.
- Message Tracking and Logging: Enable message tracking and logging to monitor email flow, track message delivery, and troubleshoot email-related issues. Exchange Server 2010 provides message tracking logs that can be analyzed to investigate message routing, delivery delays, and other email-related problems.
- Regular Database Maintenance: Perform regular database maintenance tasks to optimize performance and reduce the risk of database corruption. These tasks may include defragmenting databases, updating database statistics, and running integrity checks using Exchange utilities like ESEUTIL and ISINTEG.
- Monitoring Mail Flow: Monitor mail flow to ensure smooth delivery and reception of emails. Use Exchange Server tools and message queues to identify and address mail flow issues promptly. Implement spam filters and antivirus software to prevent malicious emails from entering the organization.
- Active Directory Health: Exchange Server relies heavily on Active Directory for user authentication and other services. Regularly monitor and maintain the health of the Active Directory infrastructure to ensure proper integration and functionality with Exchange Server 2010.
46. What are the steps involved in migrating from Exchange Server 2010 to a newer version like Exchange Server 2016 or Exchange Server 2019?
Migrating from Exchange Server 2010 to a newer version like Exchange Server 2016 or Exchange Server 2019 involves several steps. Here’s a general outline of the process:
- Review system requirements: Ensure that your environment meets the hardware, software, and operating system requirements for the new version of Exchange Server. This includes checking compatibility with your existing infrastructure, such as Active Directory and client applications.
- Plan the migration: Develop a comprehensive migration plan that includes the migration strategy, timeline, resource allocation, and potential downtime considerations. Determine the coexistence and migration approach, whether it’s a hybrid deployment or a cutover migration.
- Prepare the infrastructure: Update your existing Exchange Server 2010 environment by installing the latest service packs, cumulative updates, and any required hotfixes. Verify that the Active Directory forest and domain are functioning properly and at the required functional levels.
- Set up the new Exchange Server: Deploy the new Exchange Server environment (Exchange Server 2016 or 2019) according to your migration plan. This involves installing Exchange Server on new servers, configuring the necessary roles (such as mailbox, client access, and transport), and setting up certificates, namespaces, and virtual directories.
- Configure coexistence: If you opt for a hybrid deployment or a phased migration, configure coexistence between Exchange Server 2010 and the new version. This enables smooth mailbox and client access during the migration process. Configure connectors, certificates, and URL redirection as per your migration plan.
- Migrate mailboxes: Start migrating user mailboxes from Exchange Server 2010 to the new version. You can use various methods depending on your chosen migration strategy, such as move requests, batch migration, or third-party tools. Monitor the migration progress and ensure data integrity.
- Redirect services and update clients: Update DNS records, firewall rules, and load balancers to redirect services to the new Exchange Server environment. Update client configurations, including Outlook profiles, mobile devices, and any other email clients used within your organization.
- Decommission the old Exchange Server: Once all mailboxes have been successfully migrated and you have verified the functionality of the new environment, decommission the Exchange Server 2010 servers. This involves removing them from the organization, uninstalling Exchange Server, and performing the necessary cleanup tasks.
- Verify and finalize the migration: Validate the functionality of the new Exchange Server environment. Test various scenarios, such as sending and receiving emails, accessing mailboxes, and utilizing additional features and services. Address any issues or discrepancies that may arise during this verification phase.
47. How can you troubleshoot and resolve database corruption issues in Exchange Server 2010?
Troubleshooting and resolving database corruption issues in Exchange Server 2010 involves several steps. Here’s a general guide on how to approach this process:
- Identify the issue: Monitor your Exchange environment for any signs of database corruption. Common indicators include error messages in the event logs, issues with mailbox access, or abnormal behavior in Exchange services. Use tools like Exchange Best Practices Analyzer (ExBPA) and Exchange Troubleshooting Assistant (ExTRA) to assist in identifying potential problems.
- Gather information: Collect relevant information about the affected database and its environment. This includes the specific error messages, database size, available disk space, recent changes or updates, and any other relevant details. This information will aid in troubleshooting and determining the appropriate resolution steps.
- Verify backups: Check if you have valid and recent backups of the affected database. Valid backups can be a crucial resource for restoring data if corruption is severe. Ensure that the backup process is functioning correctly and regularly test the restoration process to confirm its reliability.
- Run database repair utilities: Exchange Server provides built-in tools for database repair. Use the “ESEUTIL” and “ISINTEG” utilities to check and repair the integrity of the Exchange database. These utilities can fix minor corruption issues, but they may require the database to be taken offline during the repair process.a. ESEUTIL: Use this command-line utility to analyze and repair the Exchange database at the database or page level. Run the following commands:
- eseutil /mh [database file] – Verify the integrity of the database header.
- eseutil /p [database file] – Repair the database. This may result in data loss.
- eseutil /d [database file] – Defragment the database after repair (recommended).
- isinteg -s [server name] -fix -test [test name] – Use the appropriate test name, such as “alltests” or “folderfix,” to repair the database.
- Create a new mailbox database: If the corruption is severe or the repair utilities fail to resolve the issue, you may need to create a new mailbox database. Move the mailboxes from the corrupted database to the new one using the “New-MoveRequest” cmdlet in the Exchange Management Shell. This process will require some downtime for affected users.
- Monitor and validate: After implementing the necessary repairs or moving mailboxes to a new database, closely monitor the environment for any further signs of corruption. Verify that users can access their mailboxes without issues, and regularly check event logs and system health reports to ensure database integrity.
- Prevent future corruption: To minimize the risk of database corruption, follow these preventive measures:
- Keep Exchange Server and Windows Server updated with the latest service packs, cumulative updates, and security patches.
- Regularly back up Exchange databases and test the restoration process.
- Maintain sufficient disk space and monitor storage health.
- Implement a proper Exchange Server monitoring solution to proactively identify and address any issues.
- Monitor and address hardware or storage failures promptly.
48. What are the different options available for managing and securing mobile devices in Exchange Server 2010?
Exchange Server 2010 includes several options for managing and securing mobile devices. Here are the main options available:
- Exchange ActiveSync (EAS): Exchange ActiveSync is a protocol that allows mobile devices to synchronize with Exchange Server. It provides basic security features such as device password requirements, remote wipe capabilities, and device encryption. EAS can be used with various mobile devices, including smartphones and tablets.
- Mobile Device Mailbox Policies: Exchange Server 2010 allows you to create and apply mobile device mailbox policies to control device-specific settings. You can define policies that enforce password requirements, encryption settings, device blocking, and other security measures. These policies help you enforce security standards and control access to Exchange resources.
- Exchange Control Panel (ECP): The Exchange Control Panel is a web-based management interface that allows administrators to configure Exchange Server settings. It provides options to manage mobile devices, including the ability to manage device access rules, quarantine devices for review, and perform remote wipes if necessary.
- Exchange Management Shell: The Exchange Management Shell is a command-line interface that provides advanced management capabilities for Exchange Server. It allows administrators to perform tasks related to mobile device management, such as configuring device access rules, managing mailbox policies, and performing remote wipes.
- Third-Party Mobile Device Management (MDM) Solutions: While not built-in to Exchange Server 2010, you can integrate third-party Mobile Device Management solutions to enhance mobile device security and management capabilities. These solutions offer additional features such as advanced device encryption, application management, and comprehensive reporting.
49. How can you configure and manage the Exchange Control Panel (ECP) in Exchange Server 2010?
To configure and manage the Exchange Control Panel (ECP) in Exchange Server 2010, you can follow these steps:
- Access the ECP: Open a web browser on a computer connected to the network where Exchange Server 2010 is installed. Enter the URL for the ECP, typically in the format of “https://<Exchange_Server_Name>/ecp”. Replace “<Exchange_Server_Name>” with the name or IP address of your Exchange Server.
- Log in to the ECP: Enter your user credentials, typically your username and password, to log in to the ECP. Ensure that you have appropriate administrative permissions to access and manage Exchange settings.
- Navigate the ECP Interface: Once logged in, you’ll see the ECP interface with various management options. The interface is organized into different sections, such as Mail Control Panel, Recipient Configuration, Organization Configuration, and Server Configuration.
- Configure Mailbox Policies: In the Mail Control Panel section, you can configure mailbox policies for managing mobile devices. You can create new policies or modify existing ones to enforce security settings, device access rules, and other related options.
- Manage Device Access Rules: In the Mail Control Panel section, you can also manage device access rules. These rules define which devices are allowed or blocked from connecting to Exchange Server. You can create rules based on device type, operating system, or other criteria.
- Review Quarantined Devices: In the Mail Control Panel section, you have the ability to review and manage quarantined devices. Quarantine allows you to review and approve or block devices before they can synchronize with Exchange Server. You can review device details and take appropriate action.
- Perform Remote Wipes: In case of a lost or stolen device, you can use the ECP to initiate a remote wipe to remove Exchange data from the device. This helps protect sensitive information. Navigate to the Mail Control Panel section and locate the remote wipe option.
- Customize ECP Settings: The ECP offers various customization options. You can configure the appearance, language settings, and other aspects of the ECP to match your organization’s requirements. Explore the options available in the ECP interface to customize it accordingly.
50. What are the best practices for disaster recovery planning and implementing high availability solutions in Exchange Server 2010?
Implementing disaster recovery planning and high availability solutions in Exchange Server 2010 involves several best practices to ensure data protection and business continuity. Here are some key considerations:
- Regular Backups: Perform regular backups of Exchange Server databases, including mailbox databases and public folder databases. Use reliable backup solutions that support Exchange Server 2010 and follow Microsoft’s recommended backup strategies. Test your backups regularly to ensure they are recoverable.
- Database Availability Groups (DAG): Implement Database Availability Groups to achieve high availability for mailbox databases. DAG allows you to create multiple database copies across multiple servers. This provides redundancy and automatic failover in case of a server or database failure. Ensure that DAG members are placed in separate physical locations for better disaster recovery.
- Server Hardware and Redundancy: Use reliable and redundant hardware for Exchange Server 2010 deployments. Implement redundant power supplies, network connections, and disk subsystems to minimize single points of failure. Consider using RAID configurations for data redundancy.
- Site Resilience: If your organization has multiple physical locations, consider implementing site resilience by deploying Exchange servers in different sites. This helps protect against site-level failures and ensures business continuity in the event of a disaster at one location.
- Virtualization and Clustering: If virtualizing Exchange Server 2010, leverage the capabilities of virtualization platforms and implement clustering for high availability. Virtualization technologies such as VMware vSphere or Microsoft Hyper-V can provide features like live migration and automatic failover to enhance availability.
- Test and Validate: Regularly test and validate your disaster recovery and high availability solutions. Perform planned failover and failback scenarios to ensure that the systems and processes work as expected. This helps identify any issues or gaps in your setup and allows for timely adjustments.
- Documented Procedures: Maintain detailed documentation of your disaster recovery and high availability procedures. Document the steps required to recover Exchange Server, restore databases, and implement failover/failback procedures. This documentation is crucial during stressful situations and aids in a quicker recovery.
- Monitoring and Alerting: Implement a robust monitoring and alerting system to proactively identify potential issues. Monitor key performance metrics, system health, database replication status, and backup success rates. Set up alerts to notify administrators of any abnormalities or failures.
After going through above Microsoft Exchange Server 2010 interview questions and answers, we welcome you to check our other blogs on Interview questions and answers on Cloud technologies:
40+ Azure Active Directory interview questions and answers
50+ Office 365 Interview questions and answers
40+ Exchange Hybrid Interview questions and answers
50+ Microsoft Exchange Online interview questions and answers
40+ Azure AD Connect Interview Questions and Answers
50+ Microsoft Exchange Server Interview Questions and Answers
Good Luck!

very good . Could you please also share for 2013, 2016 or 2019. Atleast for 2019 ex version as it is last.
Hi Sreeni.
Sure will post questions and answers on other Exchange Server versions as well. Thank you for taking time to read my post. Thanks again.