Configure Hybrid Azure AD Join – A complete guide
In this blog we will discuss how to configure Hybrid Azure AD Join and how to join join a domain-joined device with Azure Active Directory. By the end of this blog you will learn all the concepts of Hybrid Azure AD join and how it works.
Table of Contents
Watch the video
Watch this video on our YouTube channel and learn how to configure Hybrid Azure AD join and how to join domain-joined Windows machines to Azure AD.
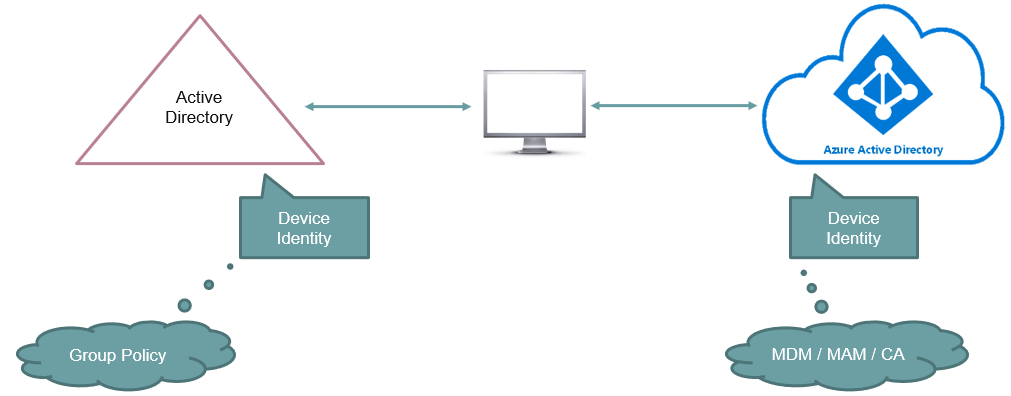
What is Hybrid Azure AD Joined device
In nutshell, Hybrid Azure AD joined device is a device that is joined with on-premises Active Directory domain and is registered with Azure Active Directory (Microsoft Entra ID).
When we join a device with on-premises Active Directory domain, a device object gets created in Active Directory for that particular device. You can find that object in Active Directory under Computers OU. When this object is created, you can apply group policies on this device, or you can apply other policies in your on-premises AD. Let’s say, you want to apply cloud policies on this device. For example, Intune policies, seamless single sign-in, or conditional access policies. So in order to apply these policies, you need a device object in Azure AD as well. And once a device identity is created in Azure AD, you can apply cloud policies on this device.
Hybrid Azure AD Join requirements
Now let’s understand the prerequisites for configuring a device as Hybrid Azure AD Join.
- You need to make sure that you are using the latest version of Azure AD connect (Microsoft Entra Connect).
- While configuring Azure AD Connect for Hybrid Azure AD join, you need to add the OUs within the syncing scope where the devices are stored.
- You need credentials of Global Administrator account of your Azure AD tenant, and the enterprise admin credentials of on premises Active Directory.
- Before you configure Azure AD Connect, make sure that below URLs are allowed in your network.
https://enterpriseregistration.windows.net
https://login.microsoftonline.com
https://device.login.microsoftonline.com
https://autologon.microsoftazuread-sso.com
- You need to make sure that your devices are using a supported Operating System as given below:
Windows current devices
Windows 11
Windows 10
Windows Server 2019
Windows Server 2016
Windows down-level devices
Windows 8.1
Windows 7
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008
How to Configure Hybrid Azure AD join
Before you start configure Hybrid Azure AD join, please make sure you have installed Azure AD Connect and it is synchronizing identities from on-premises to Azure AD. If you want to know how to install Azure AD Connect step by step, please watch this video.
Step 1. Configure Hybrid Azure AD join group policy to allow URLs
We will create a Group Policy in local Active Directory to allow the URLs required to configure Hybrid Azure AD join. Please follow below steps to allow these URLs using group policy.
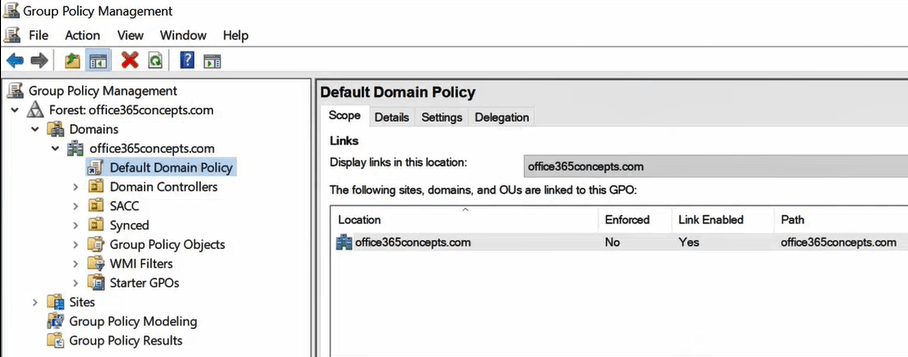
Go to Domain Controller and open Group Policy Management. In Group Policy Management wizard, expand Forest: Domain, expand Domains, and expand your domain name as shown below:
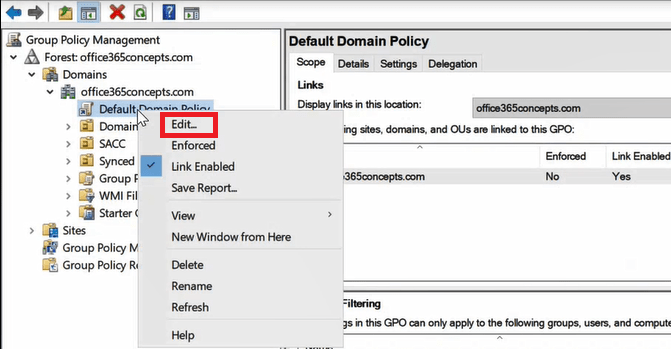
Right click Default Domain Policy and click Edit.
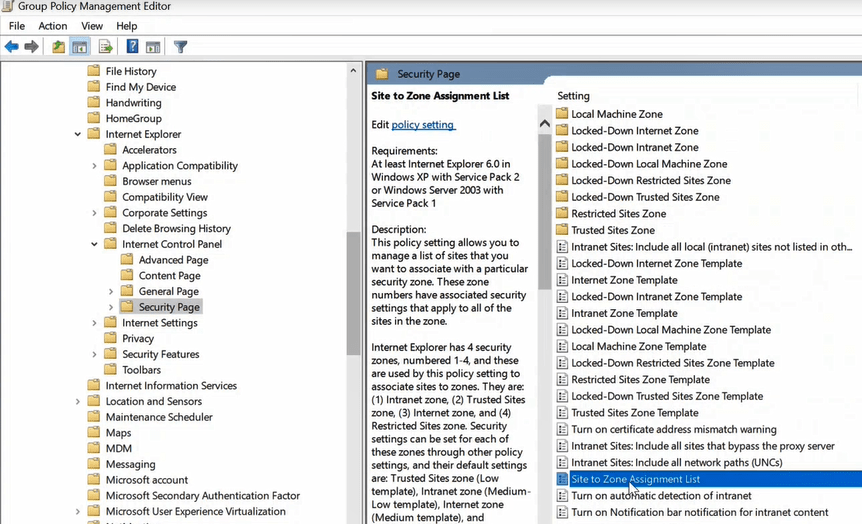
On the Group Policy Management Editor, under Computer Configuration expand Policies, expand Administrative Templates, expand Windows Components, expand Internet Explorer, expand Internet Control Panel, select Security Page, and double click Site to Zone Assignment List.
Set the policy to Enabled and click Show to add the URLs.
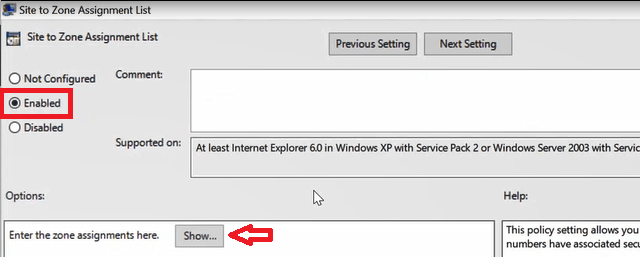
On the Show Contents page, add the below URLs and click OK as shown in below table and image:
| URL | Value |
| https://enterpriseregistration.windows.net | 1 |
| https://login.microsoftonline.com | 1 |
| https://device.login.microsoftonline.com | 1 |
| https://autologon.microsoftazuread-sso.com | 1 |
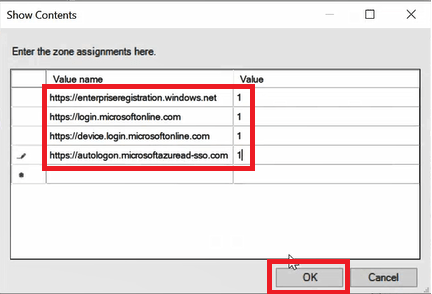
Step 2. Add OU in syncing scope
In the next step we will add the computers OU in Azure AD Connect syncing scope so that the devices can be synchronized to Azure Active Directory.
Go to Azure Ad Connect server and open Synchronization Service Manager. In Synchronization Service Manager, click Connectors and double click Active Directory connector.
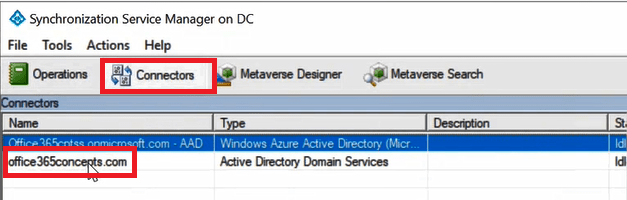
On the Properties page click Configure Directory Partitions.
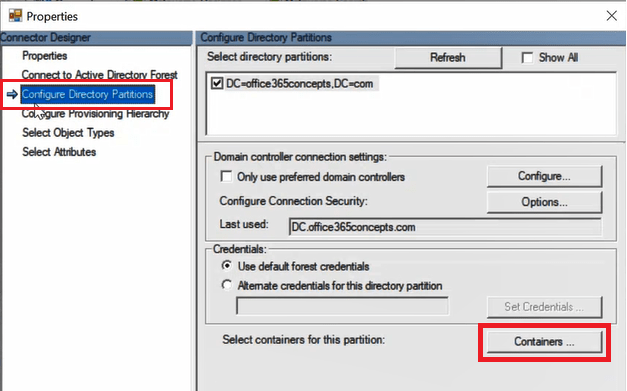
On the Credentials page, enter Username and password for on-premises Enterprise Administrator account and click OK.
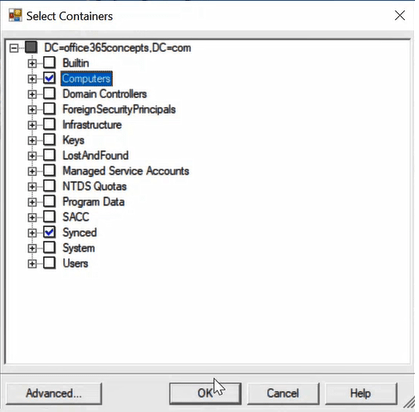
On the Select Containers page, select the OU that stores your computers and click OK.
Step 3. Configure Hybrid Azure AD join using Azure AD Connect
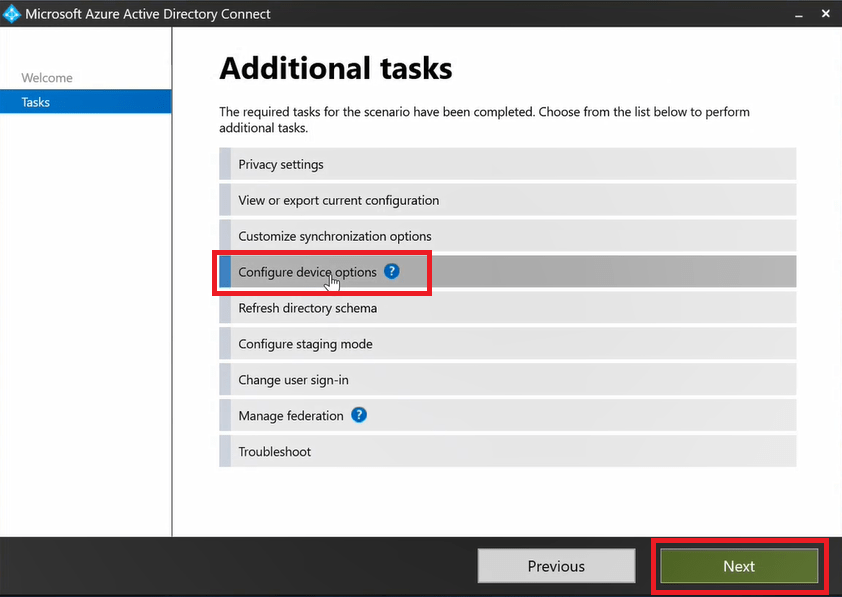
Now let’s configure Hybrid Azure AD join. Open Azure AD Connect wizard, and click Configure. On the Additional tasks page, select Configure device options and click Next.
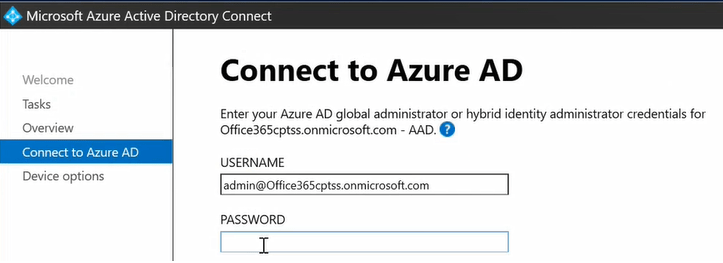
On the Overview page click Next. On the Connect to Azure AD page, type the username and password of Azure AD Global Administrator account and click Next.
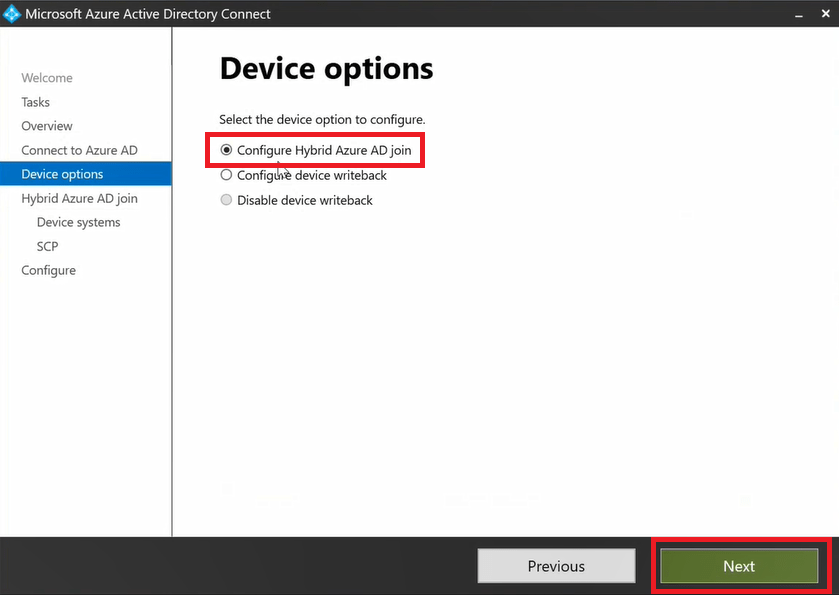
On the Device options page of Azure AD Connect, select Configure Hybrid Azure AD join and click Next.
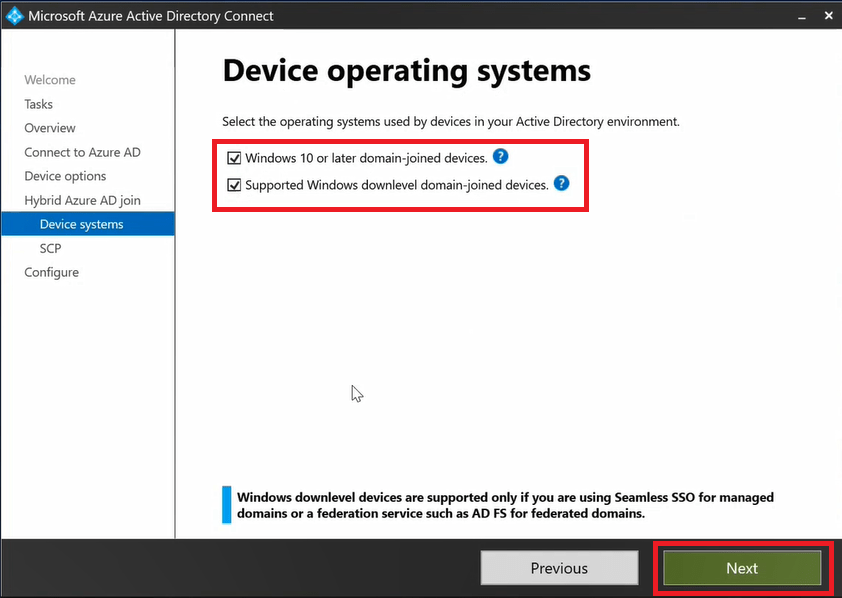
On the Device operating systems page, select Windows 10 or later domain-joined devices and Supported Windows downlevel domain-joined devices and click Next.
On the SCP configuration page, under Forest select on-premises Active Directory domain, under Authentication Service select Azure Active Directory and click Add. On the credentials prompt, type on-premises Enterprise Admin credentials and click OK.
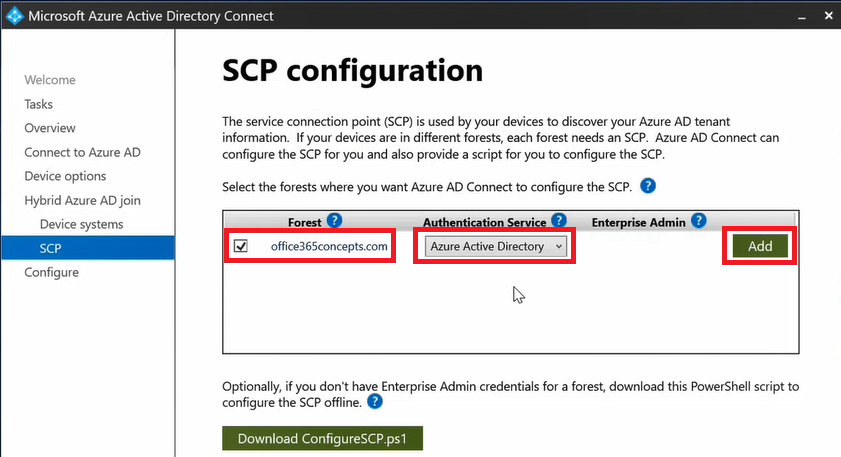
Click Next.
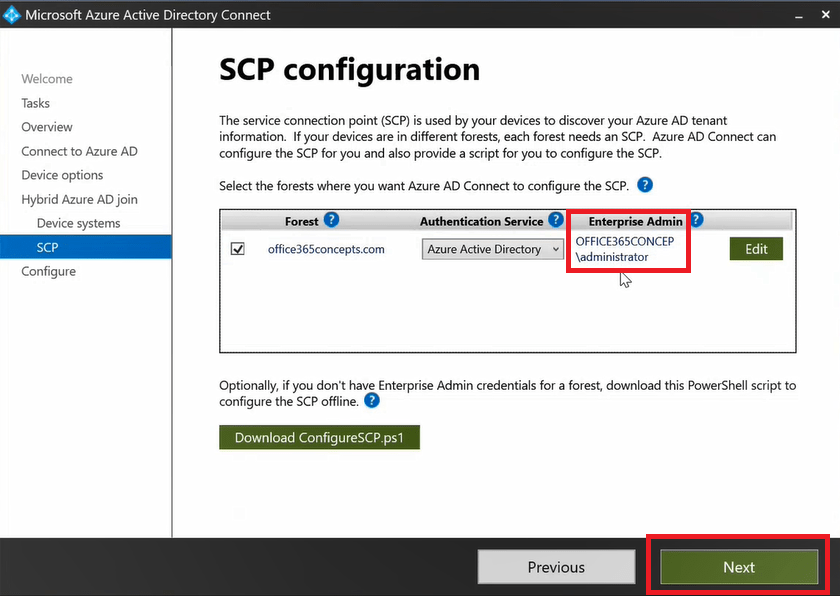
Important: SCP Configuration creates a Service Connection Point in on-premises Active Directory. This service connection point will be used by the on-premises devices to locate Azure Active Directory tenant.
On the Ready to configure page click Configure. Once configuration is complete, click Exit.
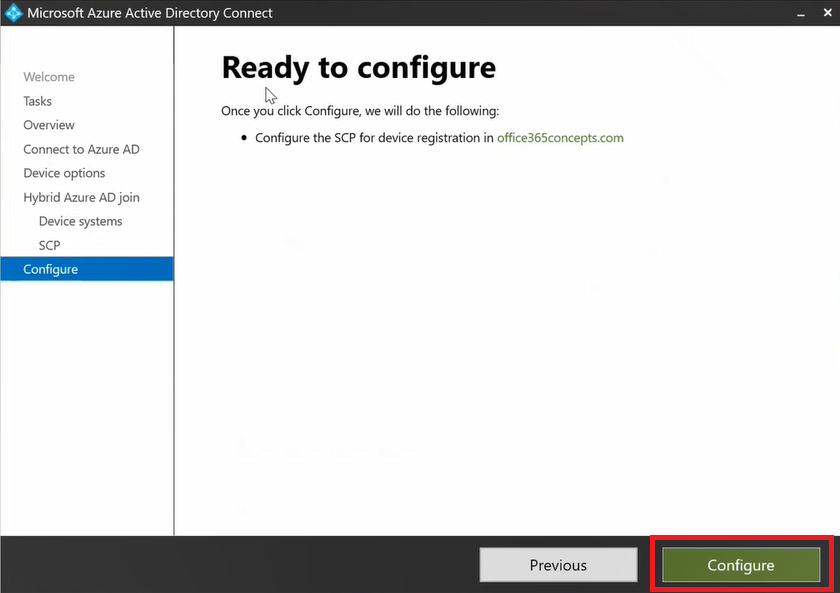
Step 4. How to find Hybrid Azure AD join SCP in Active Directory
To find Hybrid Azure AD join SCP object, open ADSI Edit from Windows Administrative Tools. On the ADSI Edit wizard, right click ADSI Edit and click Connect to.
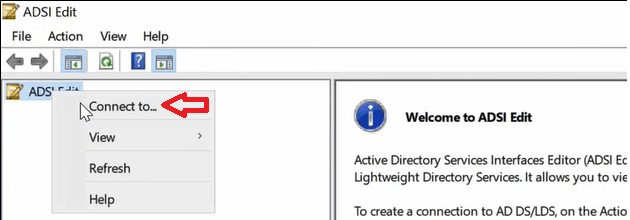
On Connection Settings page, under Select a well known Naming Context select Configuration and click OK.
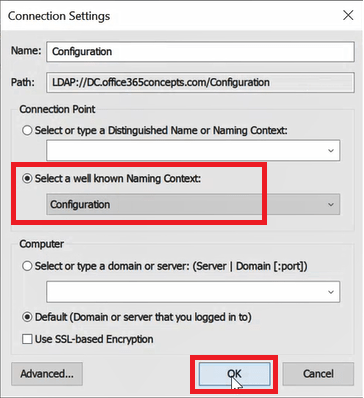
Expand Configuration [DC.domain.com], expand CN=Configuration, Expand CN=Services, and click CN=Device Registration Configuration. You will see Service Connection Point (SCP) object that will be used by the devices to connect to your Azure AD tenant..
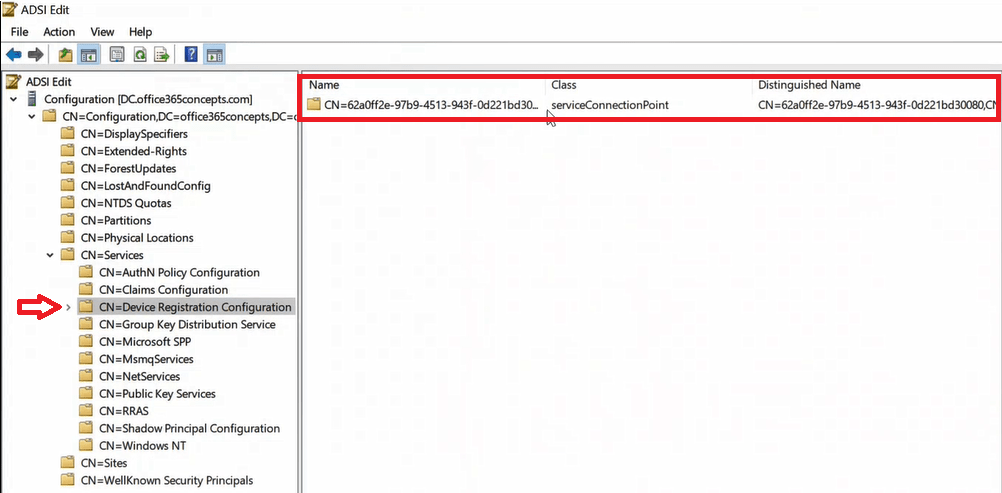
To see the properties of Service Connection Point, right click SCP object and click Properties.
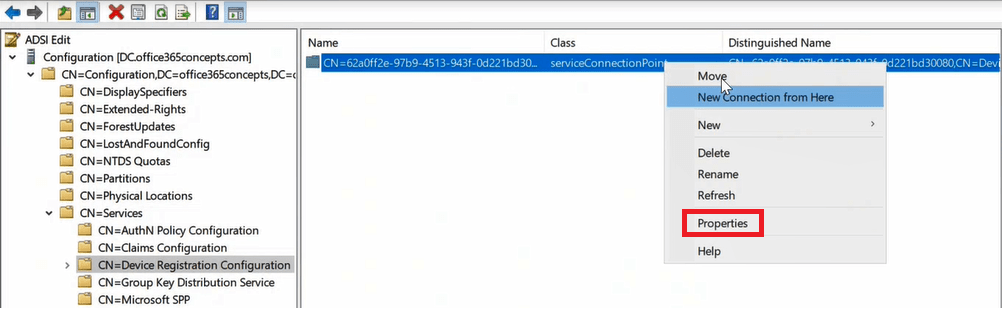
Under Attribute Editor tab, double click keywords attribute.
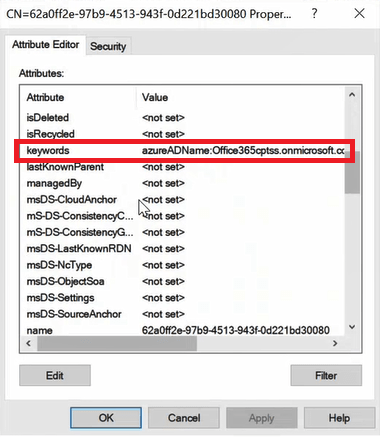
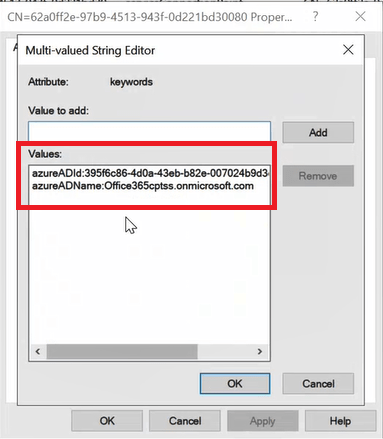
Under Values you will see Azure AD Tenant ID and your tenant’s initial domain (domain.onmicrosoft.com).
Step 5. Hybrid Azure AD join Automatic-Device-Join task in Task Scheduler
One of the most important concept in Hybrid Azure AD join is Task Scheduler. Task scheduler is a built-in windows application that is used to automate the programs or scripts.
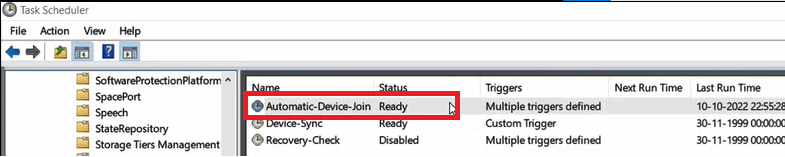
In client machine open Task Scheduler. On the Task Scheduler wizard, expand Task Scheduler Library, expand Microsoft, expand Windows, and click Workplace Join. You will see a task with name Automatic-Device-Join.
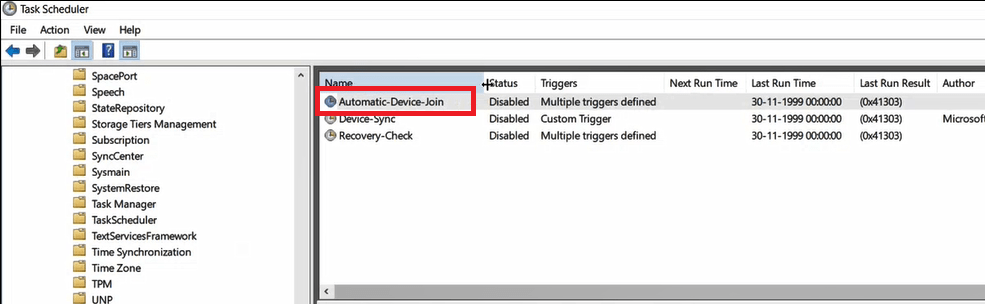
Automatic-Device-Join task is responsible to join the devices automatically with Azure AD. In the above image you can see this task is disabled, because the device is not joined to the Active Directory domain yet. Once we will join the device to on-premises Active Directory domain, this task will run automatically.
Step 6. Join client machine with Active Directory domain
To join a Windows 10 machine with Active Directory domain, go to Settings, click About, and click Advanced System Settings.
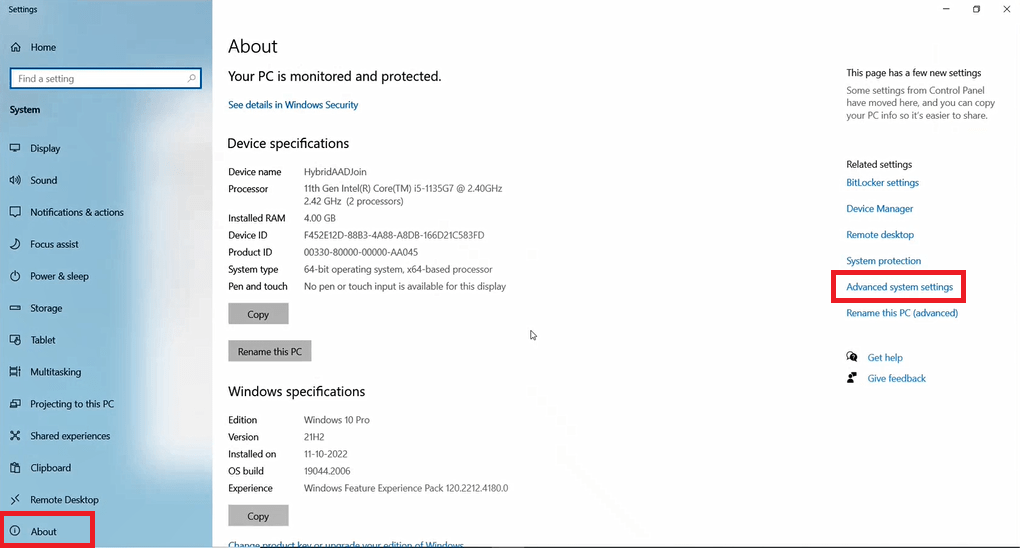
On the System Properties page, click Change.
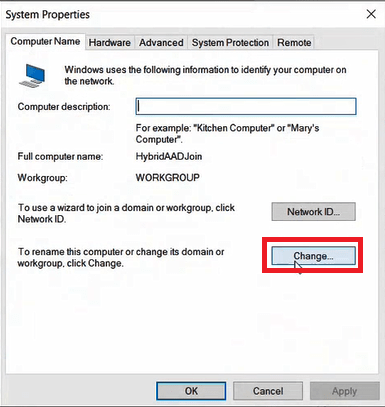
On the Computer Name/Domain Changes window, select Domain under Member of, and type on-premises Active Directory domain name and click OK.
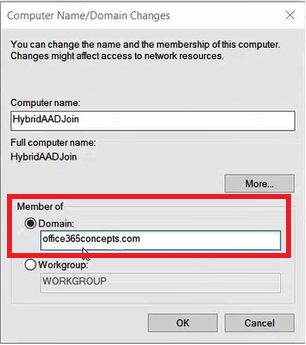
Provide on-premises Enterprise Admin credentials, click OK, and restart the machine when prompted.
Go back to Task Scheduler on the client machine, and you will see Automatic-Device-Join task in Ready state.
Step 7. Verify Azure AD certificate in computer object in Active Directory
When Automatic-Device-Join task is in ready state, the machine will contact Azure Active Directory to get a certificate. Once this device gets a certificate from Azure AD, it will store the public key of this certificate in its device object in local Active Directory.
To verify Azure AD certificate in computer object, go to Active Directory Users and Computers, find the computer object in OU and open its properties. on the Properties page, go to Attribute Editor tab and find UserCertificate attribute. This attribute holds the public key of the Azure AD certificate that will be used by this device to communicate with Azure AD.
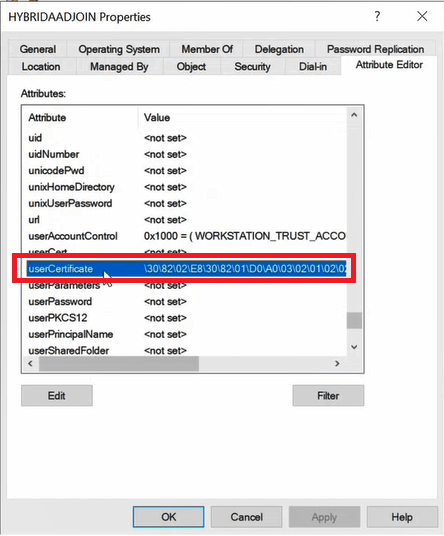
Important: If a device doesn’t has certificate public key in UserCertificate attribute, Azure AD Connect (Microsoft Entra Connect) will not synchronize that particular device to Azure Active Directory.
Step 8. Run Sync Cycle in Azure AD Connect
This is the last step where you will synchronize the on-premises Active Directory computer objects to Azure AD. You can either run Delta Sync or Initial Sync (Full Sync).
#Delta Sync#
start-adsyncsynccycle - policytype delta
#Initial Sync#
start-adsyncsynccycle - policytype InitialStep 9. Verify Hybrid Azure AD join devices
On the client machine open Command Prompt and run DSREGCMD /Status. In the below image you can see the device shows as DomainJoined and AzureAdJoined. This indicates the device is Hybrid Azure AD joined.
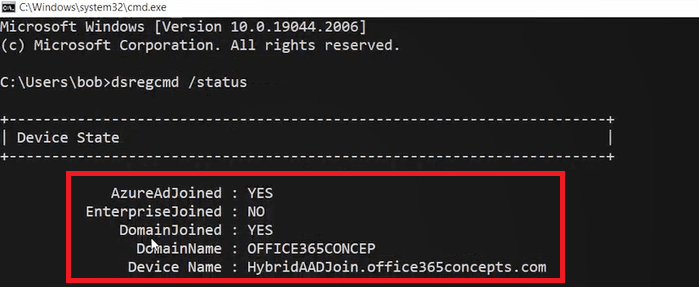
You can verify the device status from Azure Active Directory as well. Go to Azure Active Directory, click Devices, and click All Devices.
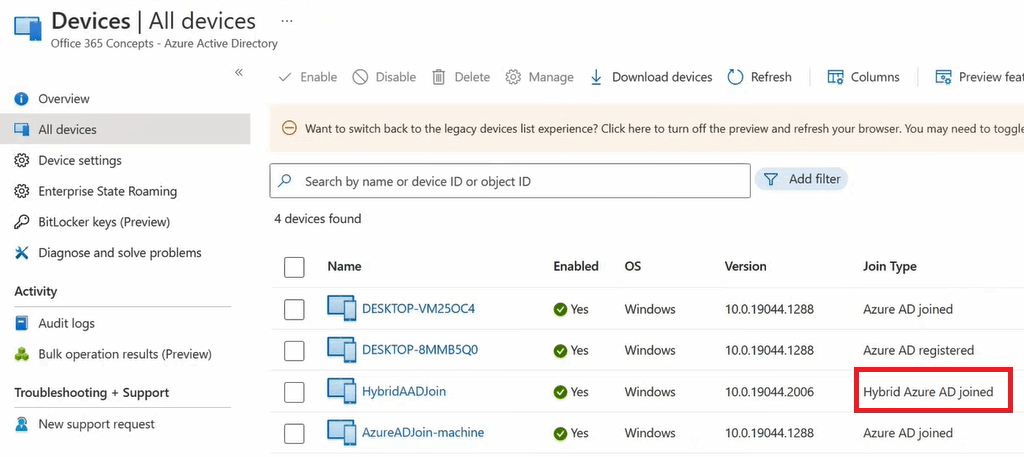
Conclusion
In this blog we learnt what is Hybrid Azure AD join device and how to configure Hybrid Azure AD join. You might like our other articles on Azure AD Registered Devices and Azure AD Joined Devices.
If you found this article helpful and informative, please share it within your community and do not forget to share your feedback in the comments below. Join us on YouTube for the latest videos on the Cloud technology and join our Newsletter for the early access of the blogs and updates.
Happy Learning!!

Based on this Configuration and GPO’s The device is enrolled only in Azure Active Right? The device is not enrolled in Intune Right?.Need your Thoughts.
Hi John,
These steps are to join on-premises AD domain-joined machine with Azure AD (Microsoft Entra ID). The devices will not be enrolled in Intune.
Thanks.