Bypass ATP Safe Links/Attachment Processing: Microsoft Defender for Office 365
In this blog you will learn how to bypass ATP Safe Links and Safe Attachments processing. You will learn how to bypass ATP Safe Links/Attachment using mail flow rules and how to use safe links Do Not Rewrite feature.
Table of Contents
What is Advanced Threat Protection (ATP)
Advanced Threat Protection (ATP) refers to a set of security solutions and technologies designed to defend against sophisticated and evolving cyber threats. Advanced Threat Protection include Safe Links and Safe Attachments which are designed to enhance the security of Microsoft 365 (formerly Office 365) environments.
ATP Safe links
Safe Links is a feature of Microsoft Defender for Office 365 (previously known as Office 365 Advanced Threat Protection). It works by scanning URLs (web links) contained within emails to determine if they point to malicious or suspicious websites. When a user clicks on a link in an email, Safe Links checks the URL against a database of known malicious links and uses real-time analysis to identify potentially harmful sites. If the link is deemed safe, the user is directed to the intended website. However, if the link is identified as malicious, the user is either warned or blocked from accessing the site, depending on the organization’s policy settings.
ATP Safe Attachments
Safe Attachments is another feature of Microsoft Defender for Office 365. It provides protection against malware and other malicious content that may be delivered through email attachments. When an email containing an attachment is received, Safe Attachments opens the attachment in a virtualized environment, known as a sandbox, to analyze its behavior and determine if it poses any threats. If the attachment is identified as malicious, it is quarantined or removed before it can reach the recipient’s inbox, thereby preventing potential damage to the organization’s systems and data.
How to verify ATP scanning on email
To verify if ATP has taken action on an email, analyze email header and look for below values.
X-MS-Exchange-Organization-SafeAttachmentProcessing
X-MS-Exchange-Organization-SafeLinksProcessing
Bypass ATP scanning Office 365
Bypassing Advanced Threat Protection (ATP) scanning is generally not recommended, however, in certain situations there might be specific needs or contexts where bypassing of ATP scanning is required for troubleshooting, or other legitimate purposes. If you want to bypass Advanced Threat Protection scanning please follow below steps:
Safe Attachments bypass rule
To bypass Safe Attachments, create below mail flow rule (transport rule):
Go to Exchange Admin Center > Mail Flow > Rules, click Add a rule and click Create a new rule.
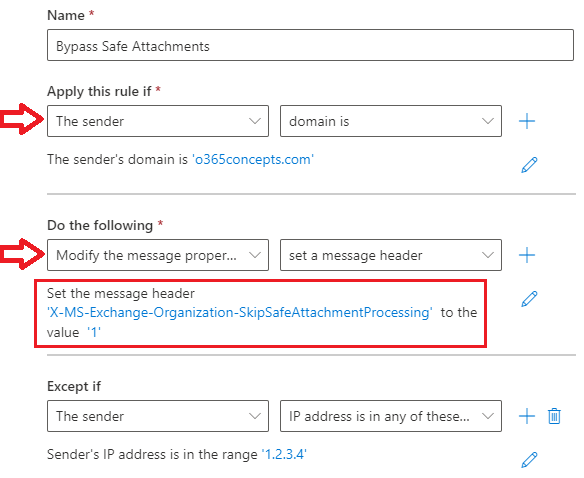
- Give this rule a relevant name like “Safe Attachments bypass rule”.
- Under Apply this rule if select The sender and then select domain is and type the domain name for which you want to bypass ATP safe attachments. You can also specify the IP address of the application/website from where you are relaying the emails. Under Apply this rule if select The sender and then select IP address is in any of these ranges or exactly matches and then add the IP address.
- Under Do the following select Modify the message properties and then select set a message header. Click Enter text for Set the message header, add X-MS-Exchange-Organization-SkipSafeAttachmentProcessing and add 1 for the value.
- If you want to add exception on this rule, you can add it under Except if.
- Click Next.
- Under Rule mode select Enforce.
- Under Severity select High.
- Check Stop processing more rules option.
- Click Next and click Finish.
Bypass ATP Safe Links
To bypass ATP safe links, please follow below steps to create a mail flow rule:
Go to Exchange Admin Center > Mail Flow > Rules, click Add a rule and click Create a new rule.
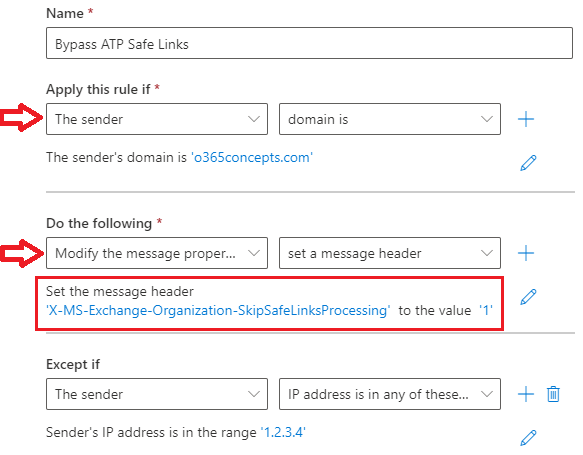
- Give this rule a relevant name like “Bypass ATP Safe Links”.
- Under Apply this rule if select The sender and then select domain is and type the domain name for which you want to bypass ATP safe attachments. You can also specify the IP address of the application/website from where you are relaying the emails. Under Apply this rule if select The sender and then select IP address is in any of these ranges or exactly matches and then add the IP address.
- Under Do the following select Modify the message properties and then select set a message header. Click Enter text for Set the message header, add X-MS-Exchange-Organization-SkipSafeLinksProcessing and add 1 for the value.
- If you want to add exception on this rule, you can add it under Except if.
- Click Next.
- Under Rule mode select Enforce.
- Under Severity select High.
- Check Stop processing more rules option.
- Click Next and click Finish.
Safe Links Do Not Rewrite URLs
Safe Links scans incoming email for known malicious hyperlinks. Scanned URLs are rewritten or wrapped using the Microsoft standard URL prefix: https://nam01.safelinks.protection..com. After the link is rewritten, it’s analyzed for potentially malicious content. Entries in the “Do not rewrite the following URLs” list aren’t scanned or wrapped by Safe Links during mail flow.
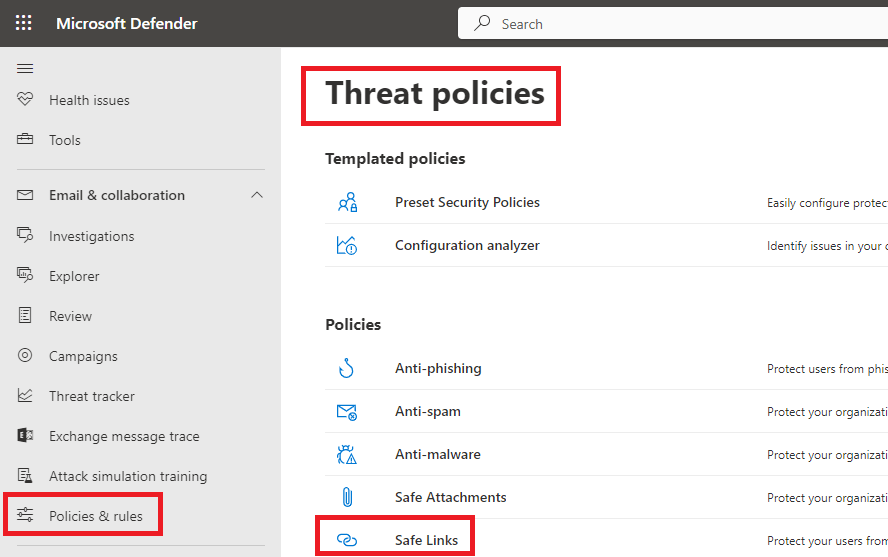
Each Safe Links policy contains a Do not rewrite the following URLs list that you can use to specify URLs that aren’t rewritten by Safe Links scanning. Go to Microsoft Defender, under Email & Collaboration click Policies & rules, click Threat policies, and click Safe links.
Give this policy a relevant name and click Next.
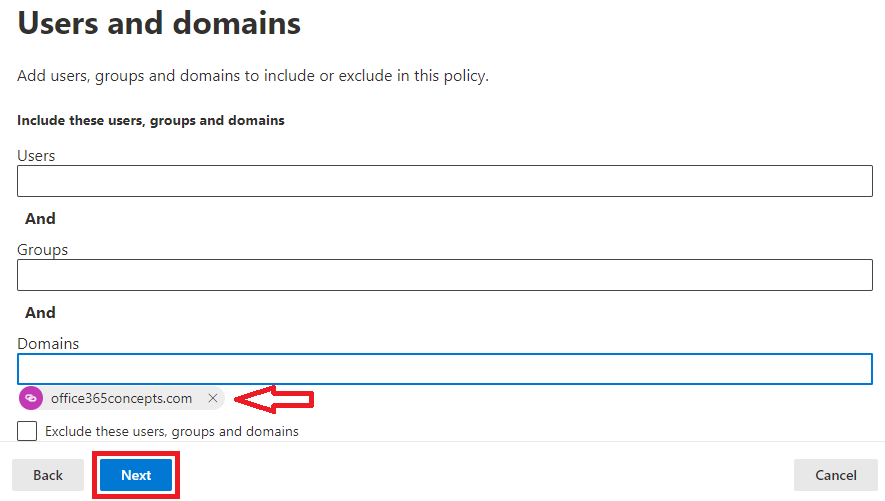
On the Users and domains page, add users, groups or domains on which you want this policy to be triggered. Once done, click Next.
On the URL & click protection settings page, click Manage 0 URLs.
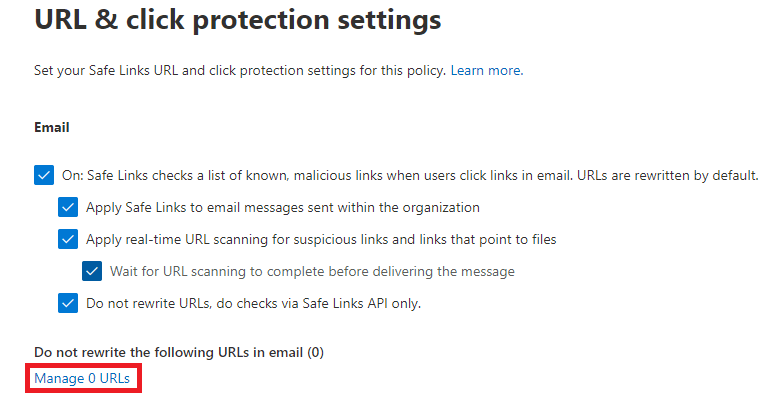
On the Manage URLs to not rewrite page, click Add URLs.
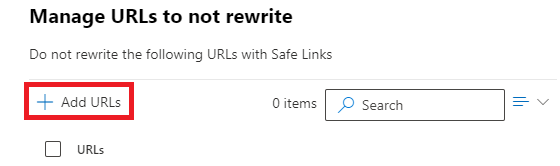
On the Add URLs page, add the URLs that should not be rewritten by the safe links policy and click Save.
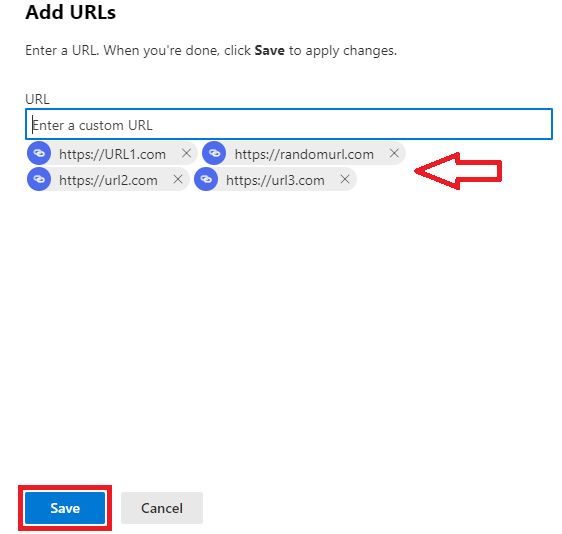
On the Manage URLs to not rewrite page you will see the URLs that you added in the previous screen. Click Done, click Next, and click Submit.
Conclusion
In this article you learnt how to bypass ATP scanning in Office 365. You might like our other article on How to stop spoofing in Office 365.
If you found this article helpful and informative, please share it within your community and do not forget to share your feedback in the comments below. Join our YouTube channel for the latest videos on the Cloud technology and join our Newsletter for the latest articles and updates.
Happy Learning!!
