Demystifying the High Risk Delivery Pool (HRDP) in Exchange Online
If we go by definition, High Risk Delivery Pool or HRDP is a separate pool of outbound IP addresses that Exchange online protection (EOP) uses for routing the outbound messages which are identified as spam emails.
When a customer’s email system has been compromised by malware or a malicious spam attack, and it’s sending outbound spam through the hosted filtering service, this can result in the IP addresses of the Office 365 data center servers being listed on third-party block lists. To prevent this, all outbound messages that exceed the spam threshold are sent through a high-risk delivery pool. This secondary outbound email pool is only used to send messages that may be of low quality. This helps to protect the rest of the network from sending messages that are more likely to result in the sending IP address being blocked.
Let’s deep dive into High Risk Delivery Pool (HRDP) and let’s understand step by step how does HRDP work in Exchange Online.
📌📌 Refer to this video on our YouTube channel to know more about High Risk Delivery Pool (HRDP)Table of Contents
What is High Risk Delivery Pool (HRDP)
So what is High-Risk Delivery Pool for outbound messages? If a user from an Exchange Online tenant sends an email, that email will be processed by one of the Microsoft email servers. And the IP address of that email server will be added as the Connecting IP (IP address of email server that processed the email) address within the email header.
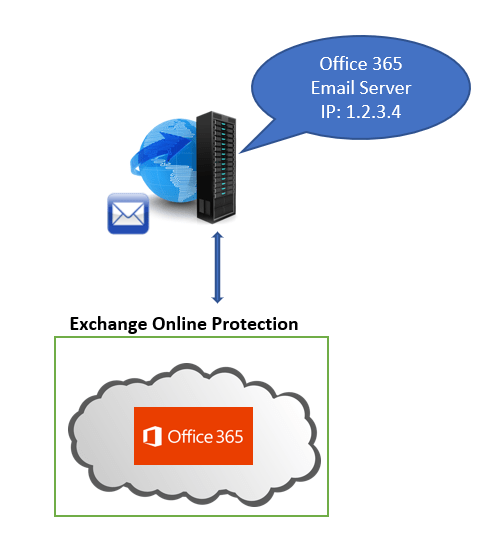
Now let’s assume, this email is a SPAM or a bulk email sent from user’s mailbox. When the recipient’s email server will receive this email, it will scan the email and during this process, this email will be marked as SPAM and the SCL value will be stamped as 5 or higher.
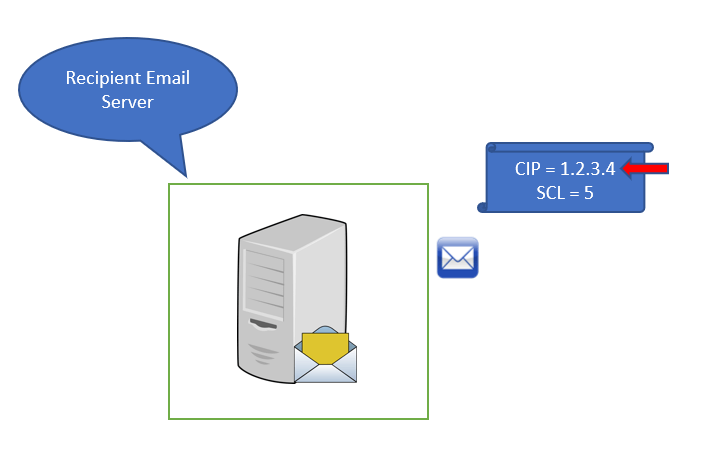
Moreover, the recipient email server will add the connecting IP address, within its low reputation IP addresses list. Because this IP address belongs to the email server (sender’s email server) that has processed a SPAM email.
Now let’s assume, If a user from another Office 365 tenant will send a legitimate email and if this email will be processed by the same email server, the recipient email server will not accept this email. Because this email was processed by an email server that had a low reputation IP address. So this is a serious problem if legitimate emails will be rejected by the recipient email servers.
Moreover, if one of the user accounts from an Office 365 tenant is compromised and someone is sending SPAM emails using that account, these emails will be processes by one of the exchange online protection email servers. When this email will be sent to the recipient server, the recipient server will mark this email as SPAM and will add the connecting IP address within the low reputation IP address list.
To overcome this situation, Microsoft has a secondary pool of IP addresses that include only low reputation IP addresses. And this pool of low reputation IP addresses, is called High Risk Delivery Pool or HRDP.
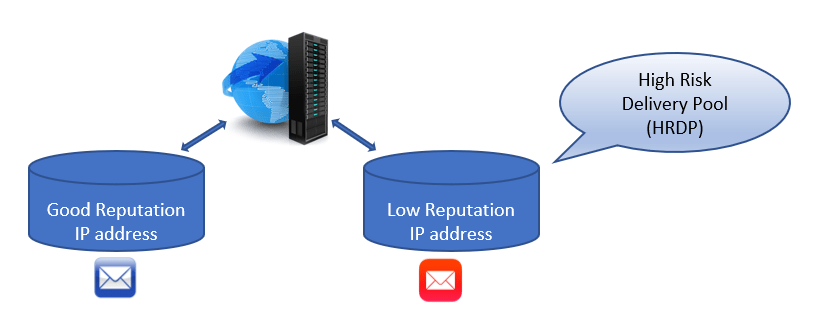
The use of a dedicated high-risk delivery pool helps ensure that the normal outbound pool is only sending messages that are known to be of a high-quality. Using this secondary IP pool helps to reduce the probability of the normal outbound-IP pool being added to a blocked list. The possibility of the high-risk delivery pool being placed on a blocked list remains a risk and we expect the HRDP IP address to be included in one or more external RBLs.
So if a SPAM email will be sent out from an Office 365 tenant, those emails will be processed by High Risk Delivery Pool servers and the legitimate emails will be processed by the good reputation IP addresses servers.
How to confirm if emails are sent through HRDP
Now the question arises, how a sender can identity if a particular email was processed by High Risk Delivery pool (HRDP) server.
To identify if an email was processes through HRDP low reputation IP addresses, look for below tab within an email header.
X-Forefront-Antispam-Report-Untrusted
If these tabs contain values SFV:SPM, SCL = 5 or higher, and SFP: 1501, that means this particular email was routed though high risk delivery pool servers.
If we run Extended Message Trace (EMT) and if we see SFV:SPM, SCL:5 or higher, and DI=SO, that means the email was routed through High Risk Delivery pool.
You can also check the public reputation of the IP addresses used to send the email. You can use mxtoolbox to check IP reputations.
Isolation and troubleshooting required when emails are sent using HRDP
- Ask the sender to send a blank email with just a signature to see if it is still marked as spam. If the email is still marked as spam, the signature may be the problem.
- Ask the sender to send a blank email with no signature or disclaimer. If the email is still marked as spam, there may be a reputation problem with the sending domain.
- Ask the sender to send the same email but with no signature. If the email is still marked as spam, the problem is likely in the email contents.
- Check the public reputation of the sending domain using mxtoolbox.
How to prevent legitimate emails from being routed via HRDP
So how you can prevent legitimate emails from being routed through High Risk Delivery Pool IP addresses? We recommend you to consider implementing the following measures in your Exchange Online organization:
- Maintain a clean email reputation: Continuously monitor the reputation of your email sending infrastructure, including IP addresses and domain reputation. Engage in email authentication practices like SPF, DKIM, and DMARC to improve deliverability and reduce the chances of legitimate emails being marked as spam emails (false positive) and being routed through HRDP IP addresses.
- Monitor email delivery and feedback loops: Stay vigilant by monitoring delivery reports and feedback loops from recipients. If you notice a significant increase in emails being routed through HRDP or receiving bounce notifications for legitimate emails, investigate and address the root cause promptly.
- Implement robust email security practices: Ensure that your organization has appropriate security measures in place, such as spam filters (inbound and outbound). This can help prevent malware infections or spam attacks that could lead to legitimate emails being flagged as high risk.
- Educate users on email security best practices: Train your employees on how to identify and handle suspicious emails, including phishing attempts or potentially harmful attachments. By promoting email security awareness, you can reduce the likelihood of internal systems being compromised and prevent legitimate emails from being routed through HRDP.
Report false positive emails to Microsoft protection team
If your emails are being routed through High Risk Delivery Pool (HRDP), there is nothing much that you can do to fix this as an administrator. You need to submit these emails to Microsoft protection team so that they can adjust the filtering servers accordingly. There are multiple ways to report these email samples to Microsoft protection team.
Submit email samples through email
Collect the original sample of the email from the sender’s sent item folder and submit the sample to the protection team following below steps:
- Create a new, blank email.
- Address the email to the Microsoft team that reviews messages at not_junk@office365.microsoft.com.
- Copy and paste the affected message into that email (as an attachment).
- Make sure all information, including mail header information is included
- Click Send.
Allow 24 hours for the filters to be updated and in case the issue persists contact Microsoft Support team.
Submit email samples from submission portal
Administrators can use Submission portal in Microsoft 365 Defender to report false positive and false negative emails. In Submission portal admins can report emails, URLs and the attachments as well.
Users can also report false positive or false negative emails from OWA (built-in Report button) or using Microsoft Report Message and Report Phishing add-ins in Outlook.
After emails are submitted in Submission portal, Microsoft analyzes the emails and adjust the email filters accordingly.
FAQs on High Risk Delivery Pool (HRDP)
1. What is high risk delivery pool?
High Risk Delivery Pool or HRDP is a separate pool of outbound IP addresses that Exchange online protection (EOP) uses for routing the outbound messages which are identified as spam emails.
When a customer’s email system has been compromised by malware or a malicious spam attack, and it’s sending outbound spam through the hosted filtering service, this can result in the IP addresses of the Office 365 data center servers being listed on third-party block lists. To prevent this, all outbound messages that exceed the spam threshold are sent through a high-risk delivery pool. This secondary outbound email pool is only used to send messages that may be of low quality. This helps to protect the rest of the network from sending messages that are more likely to result in the sending IP address being blocked.
2. What is the SFP value on message header when an email is send from high risk delivery pool?
If X-Forefront-Antispam-Report-Untrusted contain values SFV:SPM, SCL = 5 or higher, and SFP: 1501, that means this particular email was routed though high risk delivery pool servers.
3. How do you know if my email is blocked in Office 365
To determine if your email is blocked in Office 365, you can follow these steps:
Check bounced or rejected emails: If your emails are not reaching their intended recipients, you may receive bounce notifications or error messages indicating that the message was blocked. Review these messages for any information about the block or rejection.
Contact the recipient: If you suspect that your emails are being blocked, you can reach out to the recipients and inquire if they are receiving your messages or if they have observed any issues or blocks from your email address.
Check block lists: Office 365 may use various block lists or spam filters to prevent unwanted or malicious emails. You can check if your email address or domain is listed on any block lists by using online tools that provide block list lookup services.
Monitor delivery reports: If you have access to delivery reports or email tracking features in your Office 365 account, you can monitor the delivery status of your sent emails. This can give you insights into whether your emails are reaching their destinations or if there are any blocks or delivery issues.
Further resources
We also welcome you to browse through our other blog posts on Exchange mail flow:
What is SPF record and how does it work
How to setup SPF record in Office 365
What is DKIM record
What is DMARC record
What is MX (mail exchange) record
In conclusion, we have delved into the depths of the High Risk Delivery Pool (HRDP) in Exchange Online, shedding light on its purpose, functionality, and significance in maintaining robust email security. By staying proactive with email security practices, educating users, regularly updating systems, and maintaining a clean email reputation, we can reduce the chances of legitimate emails being misrouted via the HRDP. It’s crucial to strike a balance between robust security measures and ensuring that legitimate communication flows smoothly.
Thank you for joining us on this journey of Exchange Online troubleshooting High Risk Delivery Pool (HRDP). We hope this guide has provided you with valuable insights and practical knowledge to enhance your email security practices.
Stay vigilant, stay secure!
