Analyze ADFS Authentication using Fiddler
In this blog we will analyze ADFS authentication using Fiddler trace tool.
Table of Contents
Watch video
Watch this video to learn how to use fiddler to capture traffic and how to analyze ADFS authentication using Fiddler.
What is Fiddler Trace
The Fiddler tool assists in the debugging of web applications by capturing the network traffic between the Internet and test computers. This tool allows users to examine both incoming and outgoing data, providing the capability to observe and alter requests and responses before they reach the browser. Additionally, Fiddler incorporates a robust event-based scripting subsystem that can be expanded using any .NET Framework language.
Download Fiddler trace tool
To download Fiddler trace tool, click this link, enter your email address and fill in the requested details and click Download For Windows. Once Fiddler installation file is downloaded, install it.
How to use Fiddler to capture traffic
Open Fiddler trace tool, go to File tab and click Capture Traffic to stop fiddler from capturing the traffic.
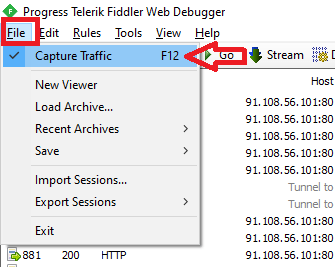
Click Tools, and click Options.
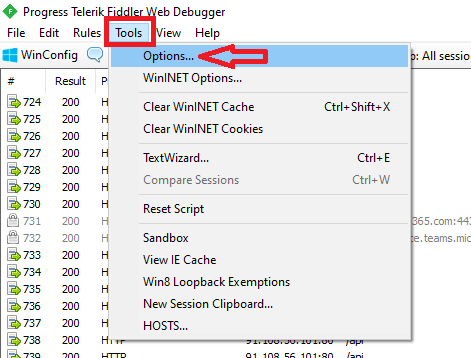
On the Options page, go to HTTPS tab and check Decrypt HTTPS traffic. Click OK on certificate prompt and click OK again.
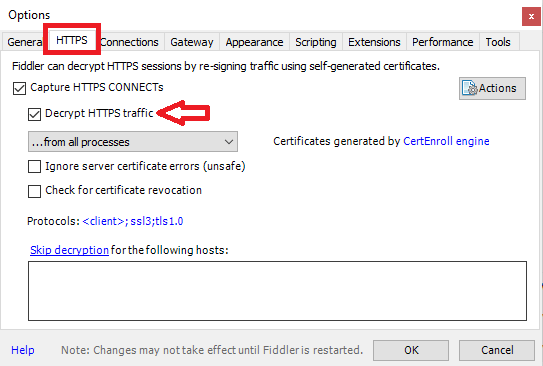
Go to File tab and click Capture Traffic again to start capturing the traffic in fiddler trace tool.
Analyze ADFS authentication using Fiddler trace tool
In this example I will login to outlook.office.com (OWA) using one of the user accounts (testuser@office365concepts.com) in Active Directory. Also I have deployed ADFS and the domain office365concepts.com is federated.
Note: You can use Fiddler trace tool to analyze any type of browser based authentication or to test any issues with we-based applications.
When you will type outlook.office.com in the browser and press Enter, you will be redirected to Microsoft 365 Security Token Service (STS) which is https://login.microsoftonline.com.
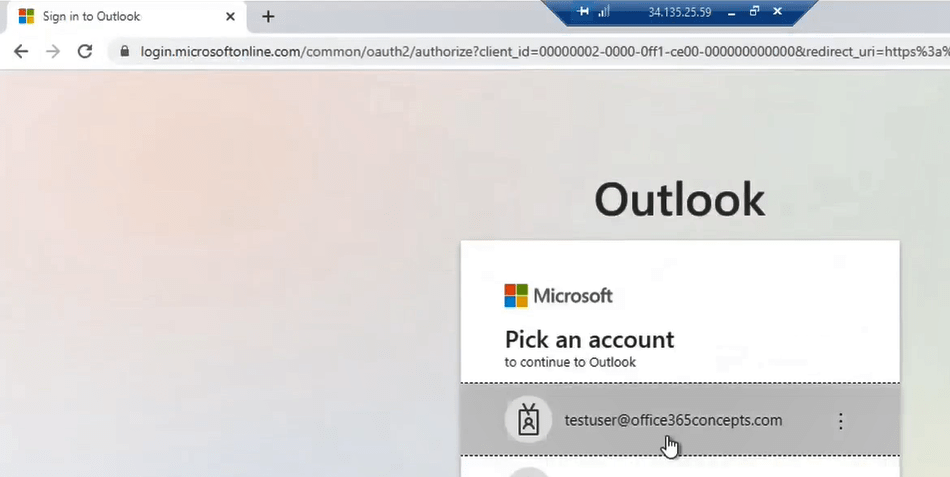
As soon as I will type or click the username testuser@office365concepts.com, the user will be redirected to the ADFS server authentication page as shown below:
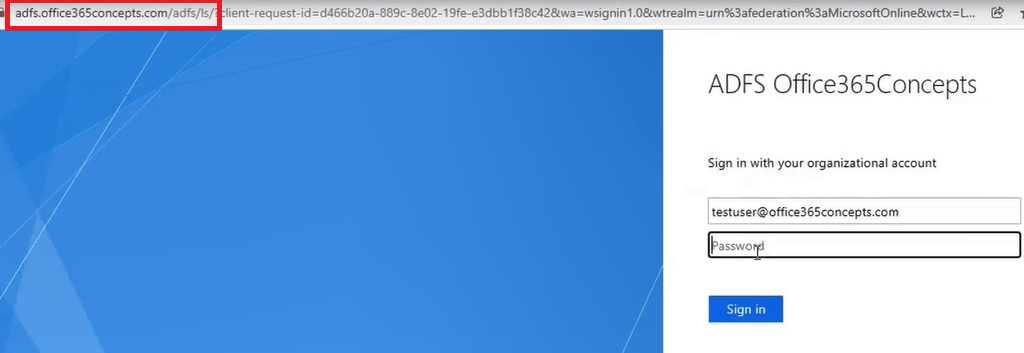
In the above image you can see the user is redirected to ADFS authentication page and you can see the URL that shows ADFS server Federation Service Identifier along with the ADFS endpoint that answered this request.
Enter the password for the account and click Sign in.
Now go to Fiddler trace tool, go to File and click Capture Traffic to stop Fiddler from capturing the traffic and let’s analyze Fiddler trace logs.
In the below image on the row 28, you can see we typed outlook.office.com, and in the row 30 you can see we are redirected to Microsoft 365 STS page.
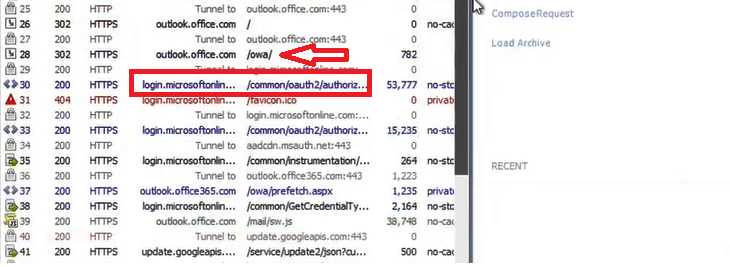
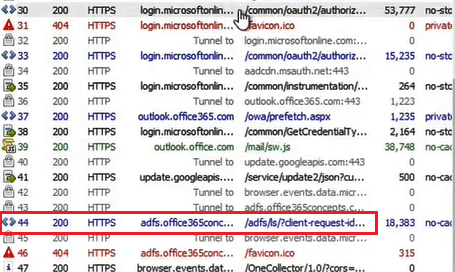
In the below image on row 44, you can see I was redirected to the ADFS server authentication page and you can see the ADFS server endpoint that answered the browser request.
Double click on the header that shows ADFS server URL, on the right side of the window make sure Inspectors is selected, and click WebForms. In this section you can see the username that was used to login to outlook.office.com.
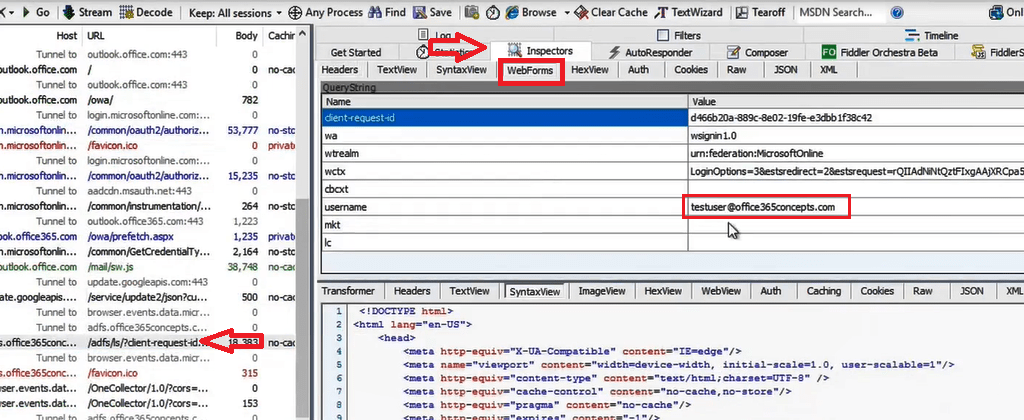
On the row 50 you can see the password that user entered in ADFS authentication page.
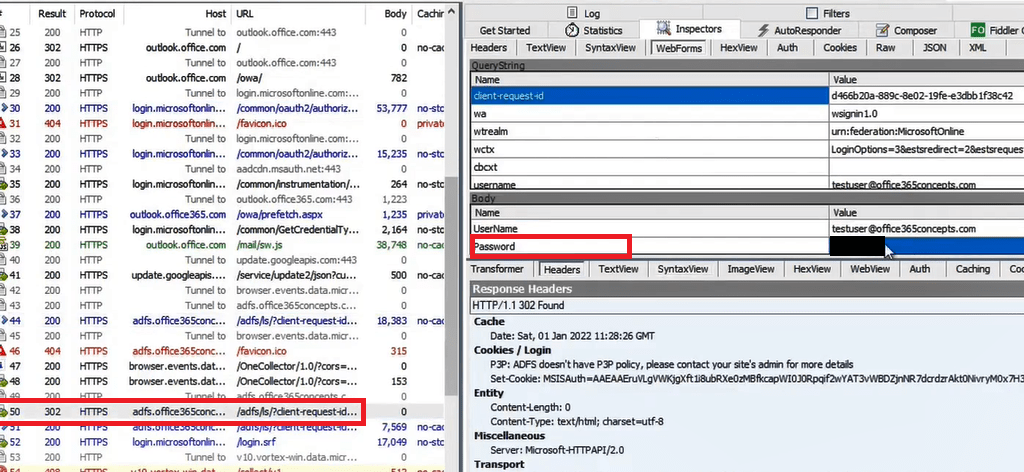
On the row 51 under Headers tab within the Response Headers section, we can see the user was authenticated and 4 cookies were issued to the user.
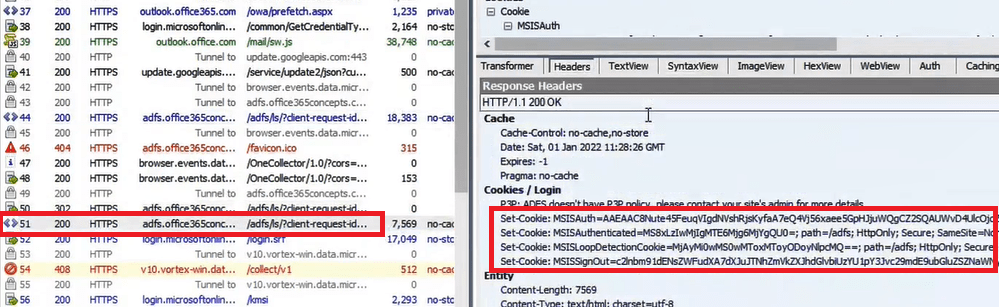
MSISAuth: This cookie tells that the user is authenticated.
MSISAuthenticated: This cookie will show the time and date when user was authenticated.
MSISLoopDetectionCookie: This cookie will show the number of attempts user has made to login.
MSISSignOut: Sign Out cookie will delete the user information when user will sign out from the application or he will close the browser.
Analyze cookies using Fiddler trace
Now let’s analyze the cookies using Fiddler trace tool.
MSISAuthenticated cookie: This cookie shows the time and date when user was authenticated. To analyze MSISAuthenticated cookie, right click on the cookie and click Send to TextWizard.
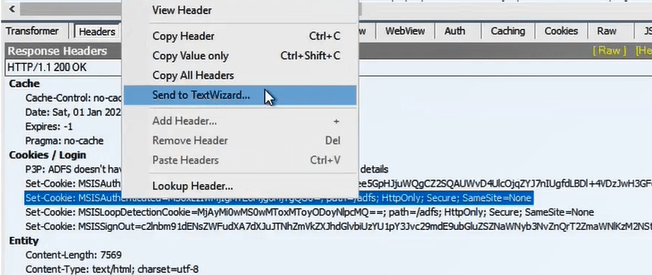
Remove the highlighted text in the below image:
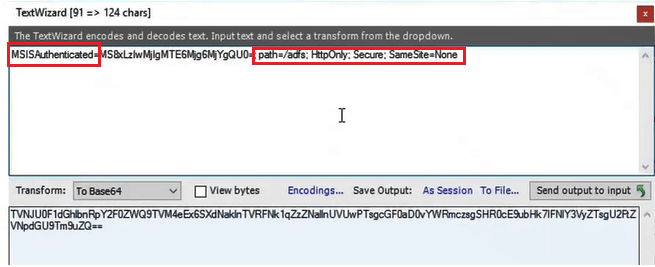
Select From Base64 next to Transform.
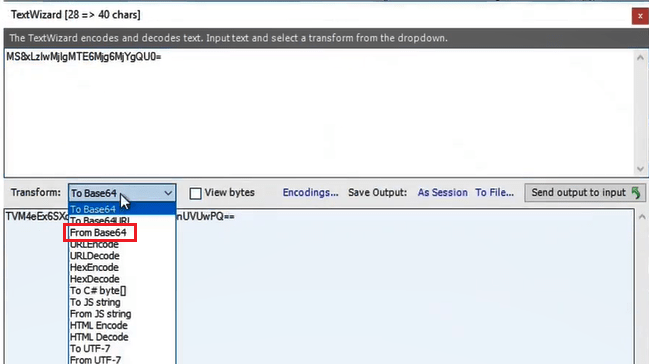
And you can see the date and time when the user was authenticated as shown in the below image:
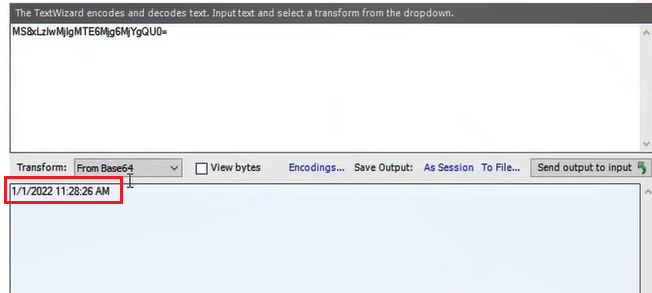
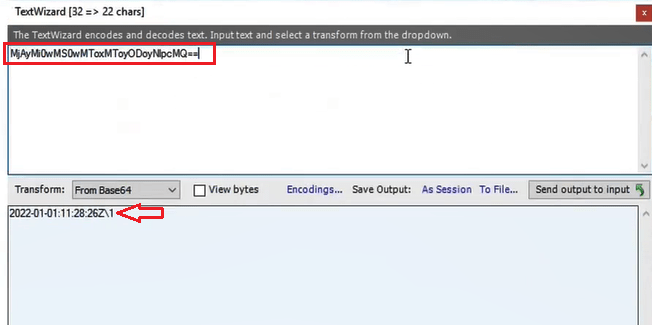
MSISLoopDetectionCookie: This cookie shows the number of attempts user has made to login to the application. To analyze this cookie, right click on the cookie and click Send to TextWizard.
Remove the text as shown below and select From Base64 next to Transform. And in the below image you can see user has made only one attempt to login to the application.
Analyze ADFS token using Fiddler
When the user testuser@office365concepts.com was authenticated, a security token was issued to the application. You can see the token in the below image. To analyze the token, right click on the text as shown below and click Copy.
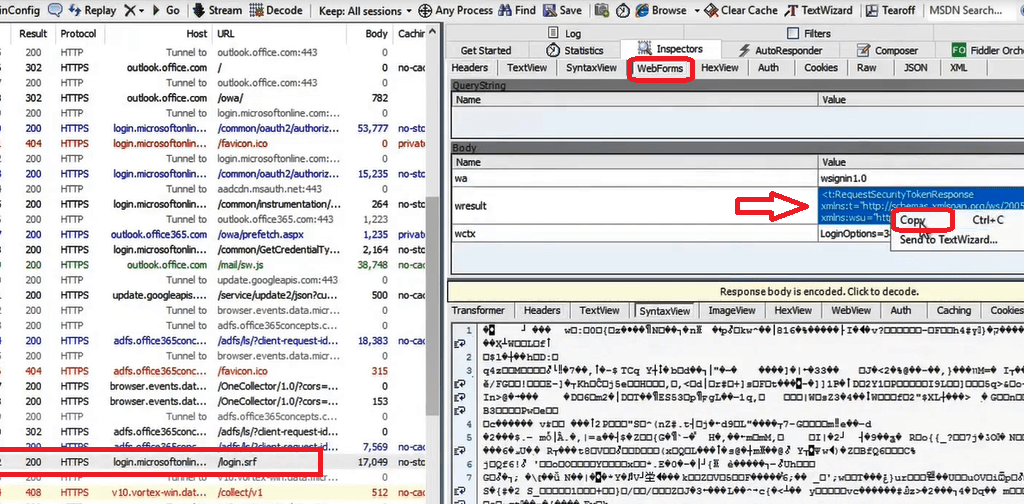
Paste this test in a notepad file and save it with .xml extension. Open the XML file to analyze the token.
Conclusion
In this blog you learnt what is Fiddler trace tool, how to use Fiddler to capture traffic, we learnt how to analyze ADFS authentication using Fiddler and how to analyze cookies using fiddler.
If you found this article helpful, please share it within your community and share your feedback in the comments below. Join us on our YouTube channel for the latest videos on Cloud technology and join our Newsletter for the early access of the blogs and the updates.
Related articles
We welcome you to browse our other articles on ADFS (Active Directory Federation Services):
What is ADFS
What is federation trust in ADFS
ADFS deployment types
How to install ADFS on Windows Server 2016
ADFS claims based architecture
Set up ADFS for Microsoft 365 for Single Sign-On
ADFS endpoints explained
What is ADFS relying party trust, ADFS Claim Rules
ADFS Authentication Flow
What is ADFS Federation Metadata
What is ADFS Claims Provider Trust
ADFS Certificates explained
How to install ADFS proxy server
What is Claims X-Ray in ADFS
Happy Learning!!
