ADFS Authentication Flow
In this blog we will dive deep into ADFS authentication flow. We will learn how ADFS authentication works, and we will talk about Active and Passive authentication in ADFS.
Table of Contents
Watch video
Join us on YouTube and watch this video to learn ADFS authentication flow and how active and passive authentication works in ADFS.
ADFS Authentication Flow
Let’s understand ADFS authentication flow works.
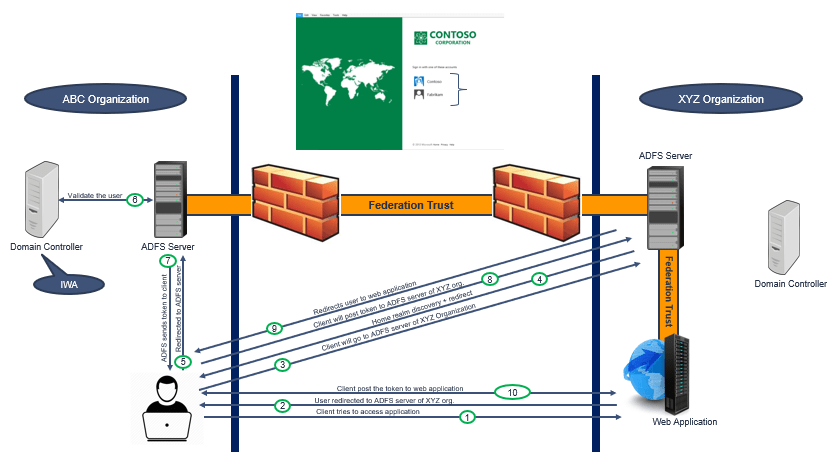
In above example we have 2 organizations. ABCorganization and XYZorganization. ABCorganization has a federation trust set up with XYZorganization, and application of XYZorganization is added as a Relying Party Trust in ABCorganization.
1. A user from ABCorganization is trying to access an application that is hosted in XYZorganization.
2. When this request will go to the application, application will ask the user to reach the federation server of XYZ Organization. Because the application can’t authenticate the user.
3. In 3rd step, client will go to ADFS server of XYZorganization, and will ask for the permission to access the application.
4. ADFS server of XYZorganization will identify that this user doesn’t belong to XYZorganization. So this server will perform Home Realm discovery to find out, to which organization this user belongs to. And it will present the user with a web page to choose his organization.
Important: A realm is a domain or security boundary in which your applications exist. When this user will try to access an application that is hosted in different organization, the federation server of that organization will try to find out if this user belongs to their organization or this is a remote user. The federation server of XYZorganization will present him a webpage, from where this user will select his organization. For example in above picture, if the user belongs to Contoso organization, user will click his organization name and he will be redirected to his organization’s ADFS server. This is called Home Realm Discovery.
5. In the 5th step, user will select his organization from the web page, he will enter his user name, and will be redirected to his organization’s ADFS server.
6. Then ADFS server will contact Domain Controller to validate the user. Domain Controller will authenticate the user using Integrated Windows Authentication.
7. Once Domain Controller will validate the user, ADFS will construct a token and will send this token to the client.
Important: In case of Microsoft 365 applications, the security token will contain 2 claims. Immutable ID and User Principal Name. And if this is not Microsoft 365 application, then depending on the application’s requirement, ADFS will add the claims within the token.
8. Then Client will post this token to the ADFS server of XYZorganization. Then ADFS server of XYZorganization will use a common secret key to decrypt this token. This common secret key is the token-signing certificate of ABCorganization’s ADFS server. Because both organizations have a federation trust and both have access to this token-signing certificate.
9. ADFS server of XYZorganization will decrypt the token, and if it finds the token is valid, it will create a new token and will share this token to the client.
10. Client will pass this token to the application and application will grant access to the user.
So this is how ADFS authentication flow works.
Passive Authentication in ADFS
Now let’s understand what is Passive Authentication in ADFS and how does it work.
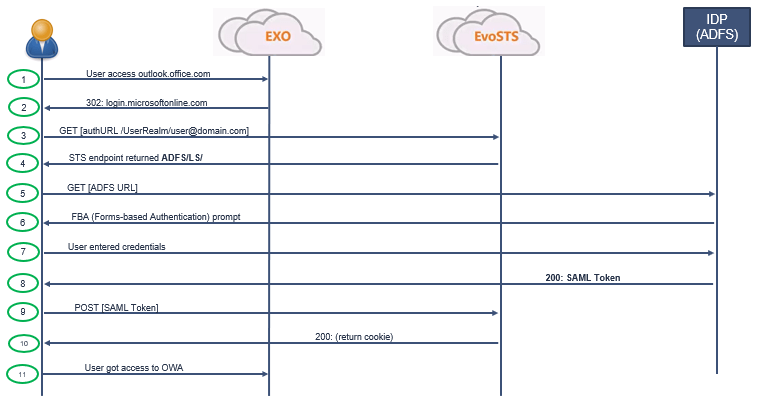
When a user tries to access a federated web application, that is called Passive Authentication. This type of request is handled by ADFS/LS endpoint.
In this example, a user is trying to access https://outlook.office.com (OWA). EXO is Exchange Online, EvoSTS is the STS point or the Security Token Service for Microsoft 365. And IDP is the ADFS server of the organization that this user belongs to. So let’s see how this user will be authenticated.
- User will enter https://outlook.office.com in browser.
- User will be redirected to EvoSTS that is https://login.microsoftonline.com.
- Then user will connect to EvoSTS. EvoSTS will present Microsoft 365 sign-in page to the user, and user will enter his user principal name.
- EvoSTS will check if the domain of the user is federated or not. As my domain is federated, EvoSTS will return the STS endpoint to the user (ADFS Server redirection).
- Then user will contact its STS endpoint. That is ADFS server of its organization.
- ADFS server will present Forms-based Authentication prompt to the user.
- Then user will enter his password.
- When user is authenticated, ADFS server will issue a security token to the client.
- Client will post that token to EvoSTS.
- EvoSTS will issue authentication cookies to the user.
- User will get access to OWA.
Active Authentication in ADFS
Let’s understand what is Active authentication in ADFS and how dies it work.
Active authentication is used by Outlook desktop client and Active Sync clients.
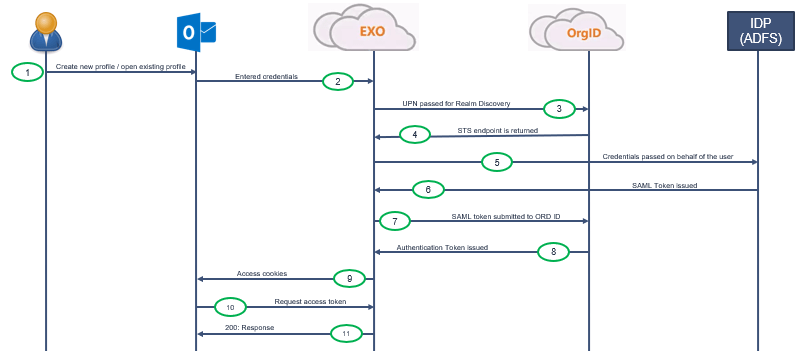
In this example, a user is trying to create a new outlook profile and his domain is federated. In passive authentication, we had EvoSTS, in active authentication requests are handled by OrgID. And IDP is again the ADFS server of the organization, this user belong to. So let’s understand the Active authentication flow.
- User is trying to create new outlook profile or he is opening an existing outlook profile.
- User will enter his credentials, and his credentials will be passed to Exchange Online.
- Exchange Online will pass his UserPrincipalName to OrgID for realm discovery.
- OrgID will check the domain name of the user UPN and will return STS endpoint to Exchange Online.
- On the 5th step, Exchange Online will pass user’s credentials to IDP on behalf of the user.
- Then ADFS server will issue a SAML token to Exchange Online.
- Then Exchange Online will submit that token to OrgID.
- In return, OrgID will issue an authentication token to Exchange Online.
- Exchange Online will issue access cookies to the client machine.
- Client machine will request the access token from Exchange Online.
- Exchange Online will issue the access token to the client, and the user will be able to configure the outlook profile.
So this is how Active Authentication works in ADFS when your domain is federated.
ADFS authentication flow and Fiddler
Analyze ADFS authentication using Fiddler
To learn how to analyze ADFS authentication using Fiddler trace, please watch this video.
Conclusion
In this blog we talked about ADFS authentication flow. We learnt what is Active Authentication in ADFS and what is Passive Authentication in ADFS.
Found this article helpful and informative, please share this blog within your community, join us on YouTube for videos on Cloud Technology, and join our Newsletter for early access of blogs and updates.
Related articles
We welcome you to browse our other articles on ADFS (Active Directory Federation Services):
What is ADFS
What is federation trust in ADFS
ADFS deployment types
How to install ADFS on Windows Server 2016
ADFS claims based architecture
Set up ADFS for Microsoft 365 for Single Sign-On
ADFS endpoints explained
What is ADFS relying party trust, ADFS Claim Rules
Happy Learning!!
