What is ADFS (Active Directory Federation Services)
In this blog you will learn what is ADFS (Active Directory Federation Services), what is claims-based identity model, you will learn how federation trust works, and we will compare Active Directory with ADFS.
Table of Contents
Watch video
Join us on our YouTube channel Office365Concepts and watch ADFS Fundamentals to gain the basic understanding of ADFS concepts that will help you to understand this and the upcoming articles on Active Directory Federation Services.
What is ADFS (Active Directory Federation Services)
If we go by definition, ADFS (Active Directory Federation Services) works on claims-based identity model. ADFS is a component of Windows Server Operating System that provides users with single sign-on access to the systems and the applications those are located across organizational boundaries.
ADFS Example 1: Let’s consider couple of examples to under what is Active Directory Federation Services and things will be more clear.
Let’s assume we have 2 organizations, organization1 and organization2. Organization1 wants to access an application that is hosted in organization2.
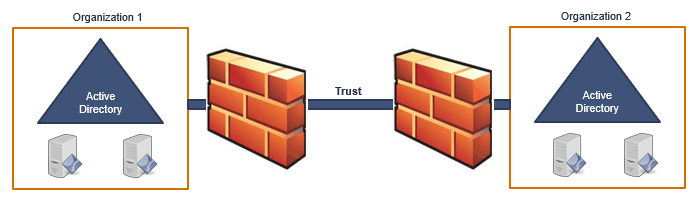
Now to achieve this, both organizations need to create a trust so that they can share their resources with each other. But this can lead to a security risk. Because both organizations will be able to access all of their resources. Moreover, in order to create a trust, both organizations need to open certain port numbers. For example, 389, 443, 89 and 636.
Now this is where ADFS comes in the picture.
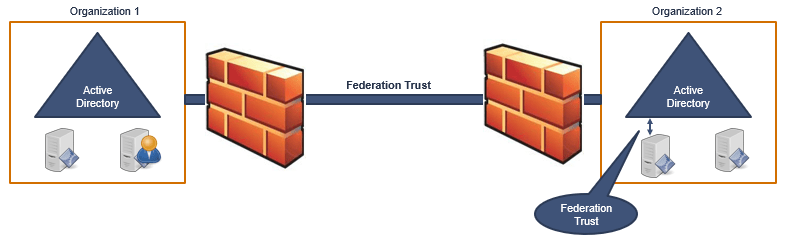
In ADFS, we create a federation trust with a particular application. And this way the users from one organization will be able to access only the application that they are authorized to. And this trust requires only port 443 to be opened.
ADFS Example 2: Let’s consider one more example to understand why do we need ADFS.
When an Active Directory account wants to access certain applications, Active Directory generates a Kerberos ticket once the user has been authenticated.
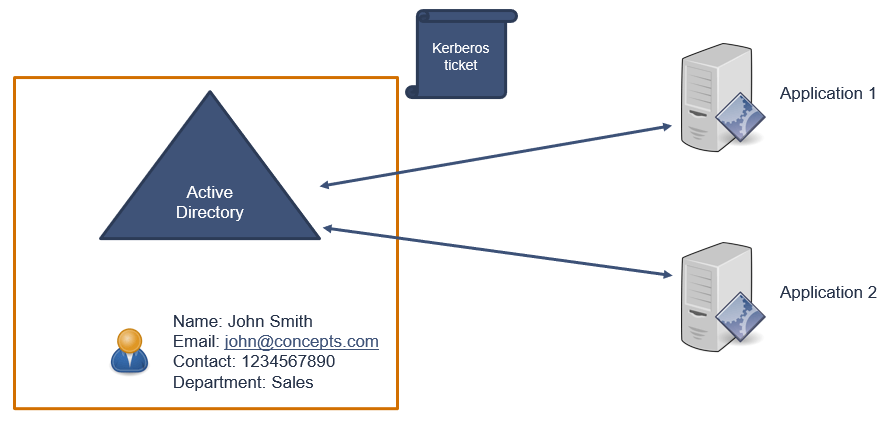
And this Kerberos ticket will be sent to the applications that this user is trying to access.
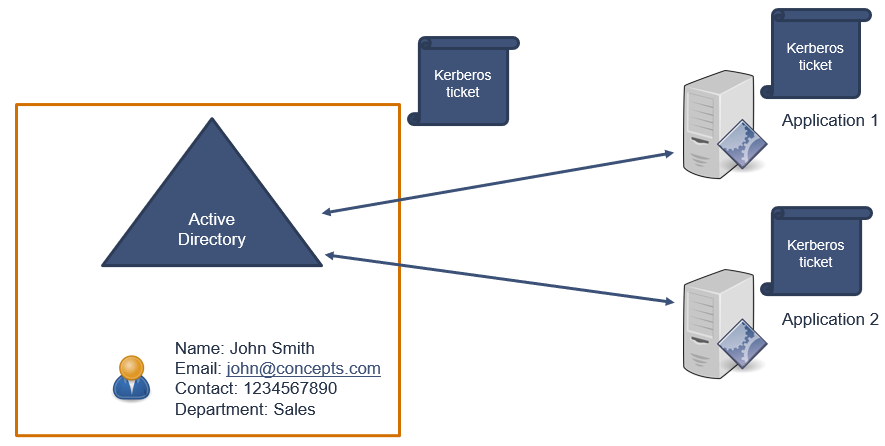
One thing to note here is, that Kerberos ticket will always contain same set of attributes. A Kerberos ticket contains User Account SID, Group SID, and Authentication Time Stamp.
In above example, a user is trying to access 2 different applications. When this user will be authenticated, Active Directory will generate 2 Kerberos tickets and will send these tickets to both the applications. And both Kerberos tickets will have same set of attributes. So that means, it doesn’t matter what sort of applications user is trying to access, same set of Kerberos tickets will be sent to the applications.
But the things will change when applications need a different set of attributes for the authentication purpose.
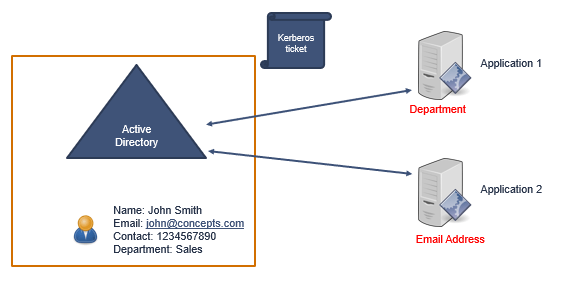
Let’s say if application1 needs Department attribute and application2 needs EmailAddress attribute for authentication. They do not need Group SID or Account SID attributes for authentication. So this is where ADFS come in the picture.
How ADFS works
Every user in Active Directory has certain attributes like, Email Address, Department, UserprincipalName or ContactNumber. All these attributes are called Claims in ADFS. In ADFS, when a user will try to access certain applications, those applications will contact ADFS server.
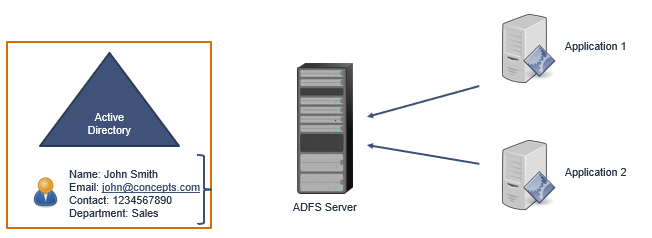
Then ADFS server will contact Active Directory to get the user authenticated.
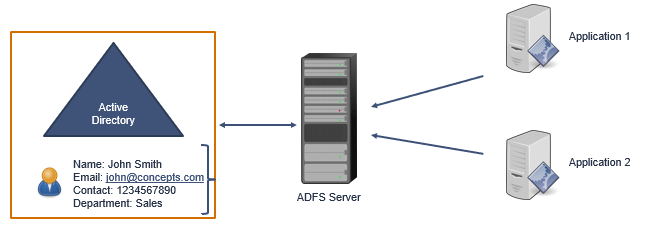
And once the user is authenticated, ADFS will send a token to the applications. But ADFS has the ability to customize the token as per the applications requirement. If application1 needs a token on the basis of Department attribute of the user, ADFS server will construct a token on the basis of Department attribute and will send it to the application.
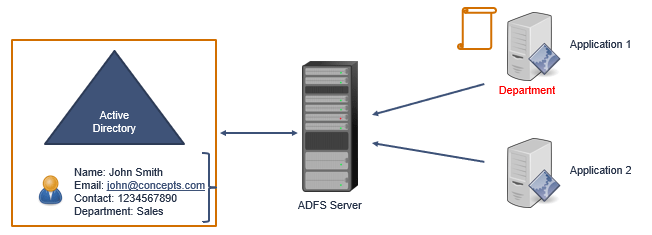
In the same way, if another application’s requirement is, that the user should be authenticated on the basis of EmailAddress attribute, ADFS will construct another token including email address of the user and will send it to the application.
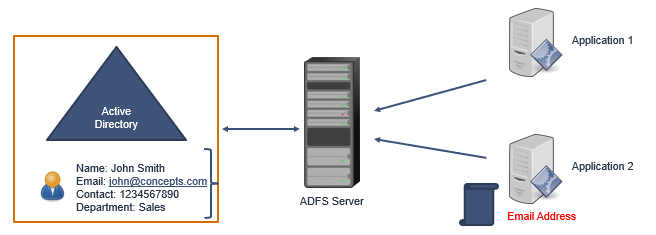
So this is one of the reasons why do we need ADFS (Active Directory Federation Services).
What is Claims Based identity Model
ADFS has the ability to customize the response as per the applications requirement. If an application’s requirement is, that once user is authenticated, I need EmailAddress attribute in the token to validate that user, ADFS will construct a token and will include EmailAddress attribute within the token, and will send it to the application. Application provider will validate the token and will provide access to the user. This is called claims-based Identity model or claims-based access-control authorization model.
ADFS vs Active Directory
Now if we compare Active Directory with ADFS, what we can understand?
| Active Directory | ADFS |
| The acknowledgement that Active Directory issues after the authentication is called ticket. | The acknowledgement that ADFS issues is called token. |
| Kerberos tickets that are issued by Active Directory cannot be customized. | ADFS token can be customized as per the application requirement. |
| In Active Directory, applications directly contact Active Directory for authentication. | In ADFS, applications contact ADFS server and ADFS server contacts Active Directory for authentication. Because ADFS is placed between the application and Active Directory. |
So what is Active Directory Federation Services
ADFS works on claims-based identity model. ADFS is a component of Windows Server Operating system that provides users with single sign-on access to the systems and the applications those are located across organizational boundaries. ADFS works on claims-based identity model because it issues claim-based tokens to the applications.
Conclusion
In this blog you learnt what is Active Directory Federation Services (ADFS), you learnt how ADFS works, what is Claims-based identity model, and what is the difference between Active Directory and ADFS.
In the next blog we will talk about Federation Trust, ADFS authentication process, we will talk about Claims, STS, Claims Provider, Identity Provider, Relying Party Trust, and much more.
Found this article helpful and informative? You may also like our Exchange Server 2019 + Exchange Hybrid series. Please share this blog within your community and join our Newsletter for early blogs and updates.
Happy Learning!
