Decoding MDM vs MAM: A Closer Look at Mobile Management Approaches
In this blog post, we delve into the MDM vs MAM debate, shedding light on the nuances of each strategy and exploring their unique benefits and functionalities. Whether you’re an IT professional looking to enhance mobile security or a business owner seeking to optimize mobile device usage, this comprehensive guide will equip you with the knowledge needed to make informed decisions.
New to Microsoft Intune or want to understand fundamentals of Microsoft Intune, refer to our previous article to get an understanding of Microsoft Intune and its fundamentals.
MDM vs MAM
In today’s increasingly mobile-driven world, organizations face the critical challenge of effectively managing and securing their devices and applications. Two prominent approaches that have emerged in the realm of mobile management are Mobile Device Management (MDM) and Mobile Application Management (MAM).
While both approaches aim to enhance control and security over mobile devices and applications, they tackle distinct aspects of mobile management.
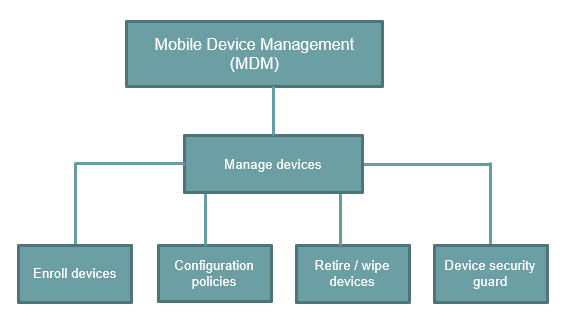
What is MDM (Mobile Device Management).
MDM (Mobile Device Management) allows administrators to manage and control the corporate-owned and personal devices. Mobile Device Management allows you to enroll the devices, push configuration profiles on devices, administrators can wipe the device remotely, or they can reset the device to the factory settings.
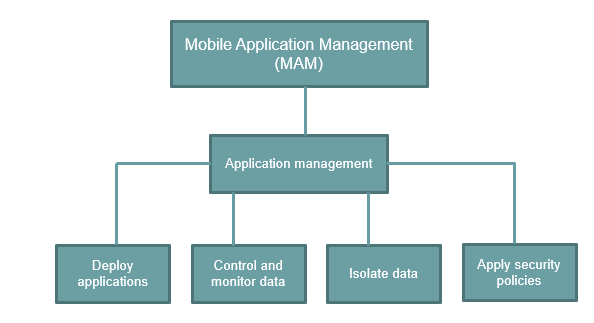
What is MAM (Mobile Access Management).
MAM (Mobile Application Management) focuses on application management. MAM allows you to control and monitor the organizational data in user’s personal devices or the corporate-owned devices. You can isolate the organizational data from the personal data within the devices. You can use Application Management Policies to prevent your users from copying the business data from Office apps to their personal applications. You can control the application deployment on the devices. With the help of Mobile Application Management policies, you can enforce strong compliance security policies on the application level.
Difference between MDM and MAM.
MDM is about controlling devices. MDM acts as a device security guard.
MAM focuses on management of the applications those are installed on the devices. MAM is about application monitoring.
What is Device lifecycle.
All devices that you manage have a lifecycle. With Microsoft Intune, you can manage the entire lifecycle of the devices. For example, if a company purchases a laptop, first, it needs to be enrolled with Microsoft Intune. Once this device is enrolled, then it needs to be configured as per company’s security requirements. Then the data that is stored on the device, has to be protected. And finally, when this device is no longer in use, you need to retire the device, or wipe the data from that device.
A device lifecycle has 4 phases.
- Enroll
- Configure
- Protect
- Retire
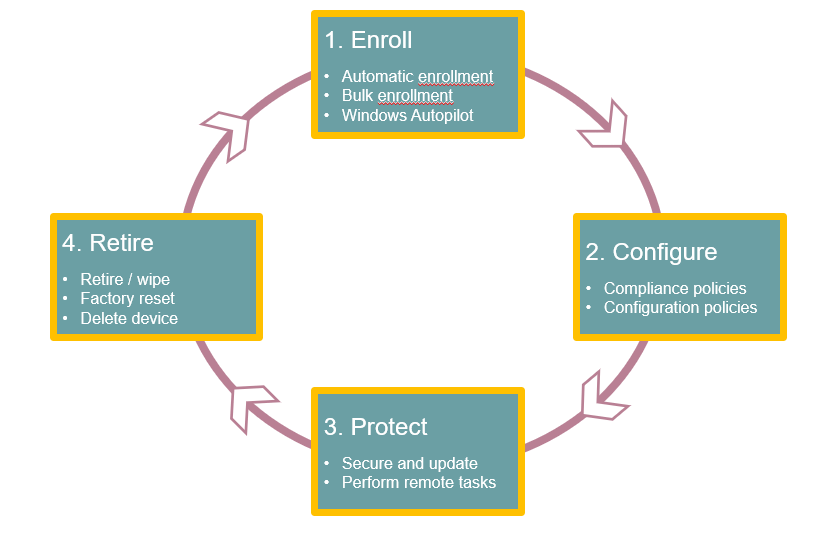
Enroll: Enrolling a device is like registering a device in Microsoft Endpoint Manager. If you want to manage a device, the first step is to enroll that device in Microsoft Intune.
Configure: Once a device is enrolled, you need to make sure the device is secure, and compliant with the company standards. With the help of device configuration profiles, you can enforce users to use password on the devices that has organization data stored. Or you can disable the use of camera on the mobile devices.
Protect: After configuring the devices, you need to make sure the data that is stored on the devices is secured. Microsoft Intune provides policies that can help you to protect the devices from un-authorized access. You can use multi-factor authentication, that adds an extra layer of security to the user sign-ins. You can use Windows Hello Pin or fingerprint to sign-in to the devices (instead of using the password).
Retire: And when a device is stolen, or when it is replaced, you can either retire the device, or wipe the organization data from the device. Or you can even restore the device to factory settings.
What is App lifecycle.
Like device lifecycle, applications also has a lifecycle. But app Lifecycle has 5 phases.
- Add
- Deploy
- Configure
- Protect
- Retire
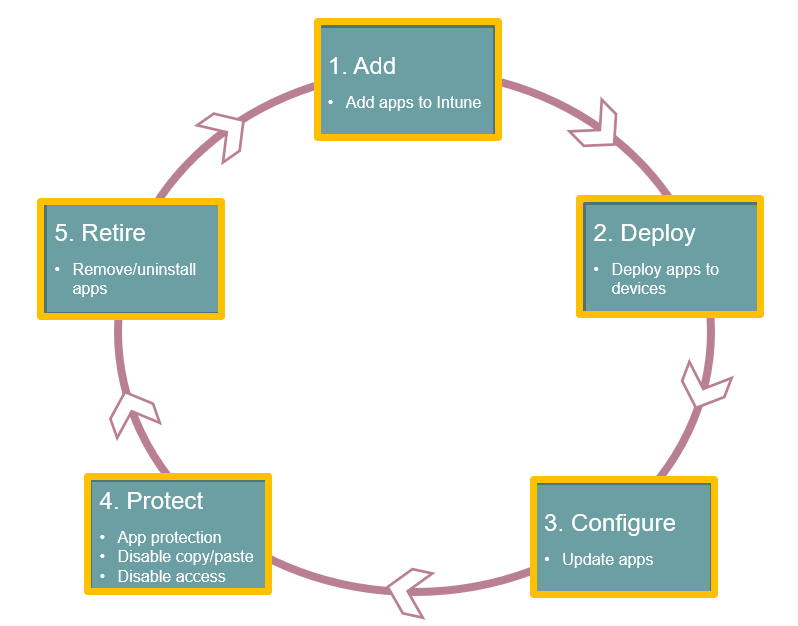
Add: The first step in app deployment is to add the applications to Intune that you want to manage and assign to the devices. With Microsoft Intune you can add different types of applications including apps those are built in-house (line-of-business apps), you can use applications from the store, and the applications on the web.
Deploy: After you have added the app in Intune, you assign or deploy those apps to the devices. And after the app is deployed, you can monitor from Intune if the application was successfully deployed on the device. You can also purchase applications from Apple store or Windows app store. You can deploy the applications from these stores from Microsoft Endpoint Manager.
Configure: As part of the app lifecycle, new versions of applications are regularly released. Intune provides tools to easily update the applications to a newer version.
Protect: Intune gives you many ways to help protect the data in your applications. You can use Conditional Access to control the access to the emails basis on the conditions that you specify. With the help of app protection policies, you can protect the company data. For example, you can restrict copying the data between un-managed and managed apps or you can prevent applications from running on the non-compliant devices.
Retire: And finally, it is likely that applications that you have deployed, have become outdated and need to be removed. And with the help of Microsoft Intune you can easily un-install the applications.
License requirements for Microsoft Intune.
In order to use Microsoft Intune, you can use any one of these licenses:
- Microsoft 365 E3 and E5
- Enterprise Mobility & Security E3 or E5
- Microsoft 365 Business Premium
- Microsoft 365 F1 or F3
- Government plans G3 and G5
- Intune for Education
To learn more about Microsoft Intune, refer to this video on our YouTube channel.
In next post I will walk you through Microsoft Endpoint Manager. We will discuss all the options within Microsoft Endpoint Manager along with their use.
Conclusion
In conclusion, the MDM vs MAM debate presents organizations with valuable options for managing and securing their mobile devices and applications. Understanding the differences between MDM and MAM is crucial for making informed decisions that align with specific business needs and goals.
We hope this comprehensive guide on MDM vs MAM has empowered you with the knowledge and insights to make informed decisions. Whether you choose MDM, MAM, or a combination of both, implementing a robust mobile management strategy will enhance control, security, and productivity within your organization.
Thank you for joining us on this journey of understanding MDM vs MAM.
Further resources
We also welcome you to browse through our blog posts on Exchange mail flow:
What is SPF record and how does it work
How to setup SPF record in Office 365
What is DKIM record
What is DMARC record
What is MX (mail exchange) record
Happy Learning!!
